Solved: Two factor authentication for admin login
-
Hello,
Is there an option to use two factor authentication for pfsense login page? If yes, I would like to use google authenticator for this?
-
- Install the FreeRADIUS package and configure it for OTP with Google Authenticator, setup a NAS entry for localhost
- Add a new RADIUS auth server entry pointing to localhost
- Set pfSense to use RADIUS auth for the GUI
Then you enter your PIN+GA Code as the password when logging in.
-
Thank you for your reply. I have installed freeradius3.
1. System / User Manager / Authentication Servers
Added Radius Server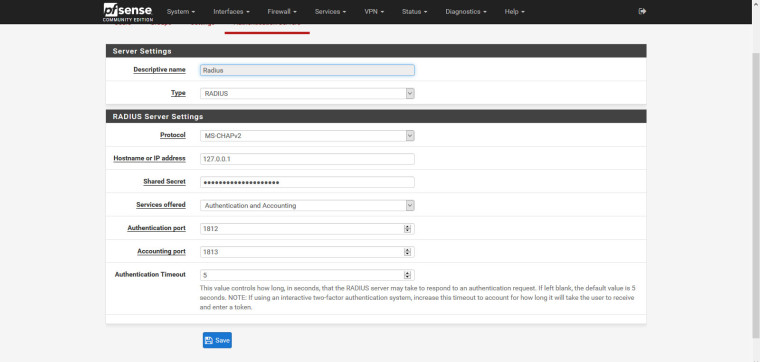
2. FreeRADIUS: Interfaces / Edit / Interfaces
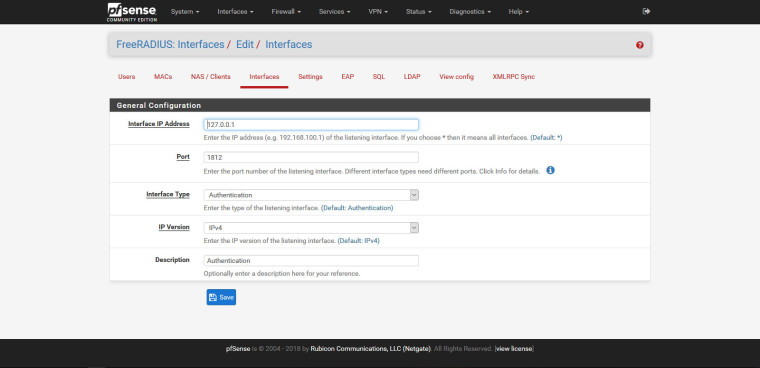
3. FreeRADIUS: Clients / Edit / NAS / Clients
Client IP Address: 127.0.0.1
Client Shortname: pfsense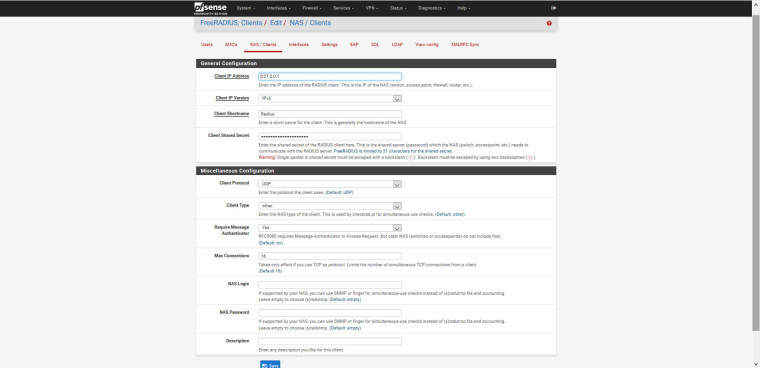
4. Package FreeRADIUS: Users / Users
Added username, enabled One-Time Password,
OTP Auth Method: Google Authenticator
Added Init-Secret and Pin
Generate QR code and added to my Google Authenticator on mobile app5. System / User Manager / Settings
Authentication Server: RadiusHow can I set pfSense to use RADIUS auth for the GUI?
-
I think you also need Service-Type = Administrative-User against the user.
-
Where is Service-Type = Administrative-User?
-
Your admin account would already have that set.. But you need to set under users manager to use your radius server not the local database.
-
Additional RADIUS Attributes (REPLY-ITEM) right at the bottom of the user you created in FreeRadius under the Advanced Configuration section.
-
I have many users using openvpn. Then those users will not be able to connect through openvpn?
-
You want these many users to connect to the pfSense login page ?
I use IPsec IKEv2 for a VPN solution so I add the following as an Additional RADIUS Attributes (CHECK-ITEM) NAS-Identifier == strongSwan, this basically only allows connection if the request has come from strongSwan and the VPN user ID.
This basically disables users connected to my LAN using their FreeRADIUS accounts to log into the routers management page.
If you ssh to your router and run a shell, then type in radsniff -x, then connect via OpenVPN, you'll see the NAS-Identifier output to the console.
You'd need to create an account to log into the pfSense GUI and include Additional RADIUS Attributes (REPLY-ITEM) Service-Type = Administrative-User.
I'd add the Additional RADIUS Attributes (CHECK-ITEM) NAS-Identifier == ?????? as a precaution to the OpenVPN users.
-
pfSense won't care about
Service-Type. It needs group membership or a username match.So you can have local users with the same usernames with appropriate permissions, or the much easier route, have groups on pfSense (like the default
adminsgroup) and then put something like this in the RADIUS user reply attribute:Class := "admins" -
Basically you want to be able to test that entry from Diagnostics > Authentication and when you login with the RADIUS credentials it should tell you that the user is a member of the
adminsgroup. -
LOL yup I was looking at the wrong user

Service-Type = Administrative-User is for my Linksys switches.
-
I have 2 admins in our pfsense and other users for vpn.I selected Radius in Authentication Server in User Manager. But I still login with the username created in local database, plus I can't login with the username created in Radius. I checked credentials in Diagnostics, it says The following input errors were detected: Authentication failed.
-
If RADIUS login fails it falls back to local users, so your local admin user in pfSense will still work. That is a safety measure so that you don't get locked out by a broken RADIUS server.
You need to concentrate on fixing the RADIUS settings if the authentication is failing, something there still isn't quite right.
-
Is there a tutorial for this? I have another question. if there is no internet, can I still login into pfsense web gio with two factor authentication?
-
@emammadov said in Two factor authentication for admin login:
Is there a tutorial for this?
https://www.youtube.com/watch?v=n2Z3rr4W2xw
https://www.slideshare.net/NetgateUSA/radius-and-ldap-on-pfsense-24-pfsense-hangout-february-2018I have another question. if there is no internet, can I still login into pfsense web gio with two factor authentication?
Google Authenticator does not actually contact Google for anything. It's a mathematically calculated OTP value based on your own key, date/time, etc. It isn't actually tied to any Google service/account/login/etc. It's basically a Google-branded equivalent to mOTP.
-
Thanks. I tried and it worked. Along with the user created on Radius, I can also login with the user created on local database though I have chosen Radius in Authentication Server. You said it is a safety measure.
I have a question. I disabled webgui login for default local admin user "admin" and it works only on console. I wonder if Radius login fails, 1. can I add any user created on the local database to admins group on pfsense console and 2. enable webgui login for admin user? -
The local user fallback will work for any local user, it doesn't need to be
admin. You can grant that user whatever privileges you want them to have. If adding them to theadminsgroup is what you want, that will work. -
I mean, I have disabled local admin user, so it can't login via webgui, it works only on ssh and console. If Radous server suddenly fails, how can I enable local admin user on SSH so that I can login via webgui!?
-
Yes, I know what you meant. What I'm saying is you can keep the actual "admin" account disabled and have some other local account you use instead that is always available for use.
Forcing yourself to re-enable admin when RADIUS is down is not a proper or reliable process. You can do it by resetting the admin password from the console which should re-enable it, or try
pfSsh.php playback changepassword adminfrom the shell.I wouldn't leave the firewall without some kind of active fallback authentication account though.