Route all Traffic over OpenVPN doesn't work
-
hi there
i want my VPN to route all traffic from connected clients.
i've been searching for days now and i could not find any solution, so i really hope somebody can help me here.i have setup an OpenVPN Server and Client. Client connects to PIA and with aliases.
Server is listening on UDP Port XYZZZ. I have set the DNS manually so it points to my pihole
I can connect and it works but not all traffic will be routed over the VPNNow i want to route all traffic over the VPN
i tried with the setting "Route all traffic over VPN" - no luck
i tried to push out the redirect-gateway def1 - no luck
the client connects to the Server but DNS will not be resolved. I have no internet access.Tried my pihole DNS and also tried to set it to 8.8.8.8 – there’s no difference. Still doesn’t work.
I believe it has to do with the settings and not the DNS/pihole itself because if i don’t route all traffic it works.Where do i need to look? Any suggestions?
Did i miss something? According to online manuals and YT videos the setup is pretty straight forward but somehow not for me…my setup:
ISP -> pfSense (2 NICs) -> Switch (8 Port) -> Devices - pihole
- NAS
- notebook
- AP
- phonesthanks
-
You may need to add an access list for the OpenVPN server's tunnel network to the resolver. Go to Services > DNS Resolver > Access Lists and add one with action "allow" for the tunnel network.
-
just added that, no difference. still the same issue...
any other suggestions?
is there a way how i can narrow down this and troubleshoot?
-
To be clear, are you saying that you want to be able to connect to your OpenVPN server, and from there have all traffic routed trough your PIA OpenVPN client connection? Because I'm not sure how to do that. It might work if you set the gateway corresponding to the PIA client connection as the default gateway, but that may also cause other issues.
-
first of all i want just to route all traffic while connected via VPN, not particulary neccesary trough PIA.
i would just be happy if i get it to work.i believe route it further via PIA should not be an issue
-
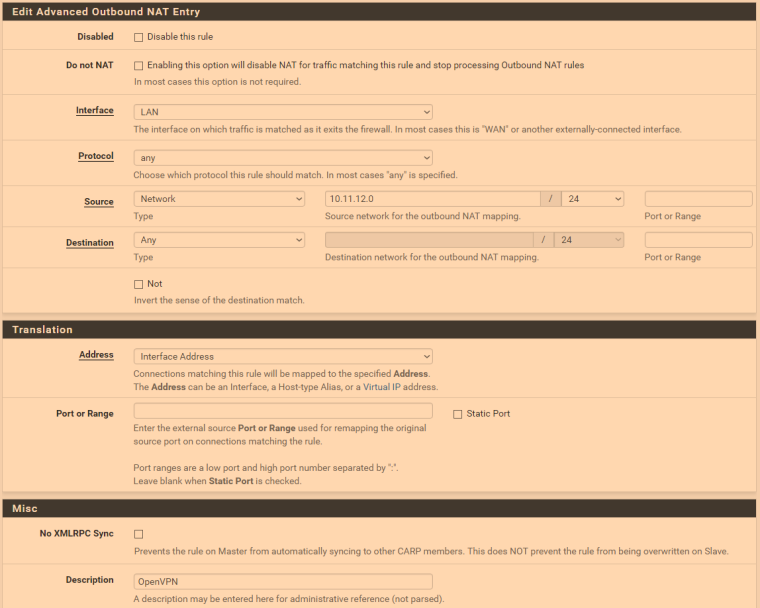
Ah okay, I didn't realize it wasn't working at all. Did you make an outbound NAT rule? It should look something like this, with 10.11.12.0 replaced with whatever your tunnel network is. Sorry for the color; seems to be a weird issue with screen shots and fl.ux.
-
For upstream traffic, the interface has to be "WAN", of course.
-
thanks for your help guys
i've had issues using the forum so i could not post until now.however, i tried both inputs, still no luck. any other suggestions?
-
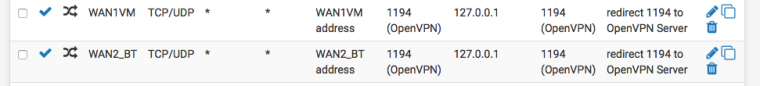
It works for me. Mine is a simple remote client setup using /30 for each client. Also I have the Openvpn server running on Localhost, and specific port forwards for the external ports running on each of my Dual WAN. This way I can easily change external port without stopping the server !!
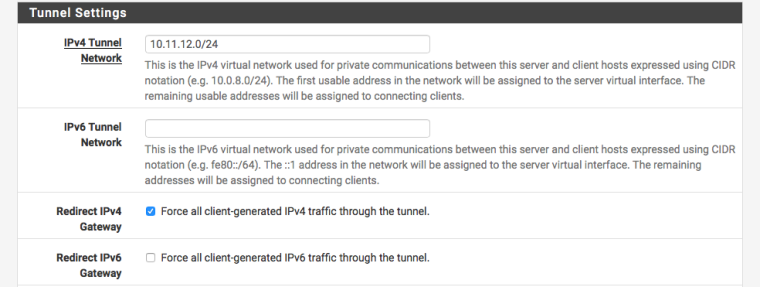
In VPN server setting just tick the box for force all traffic.
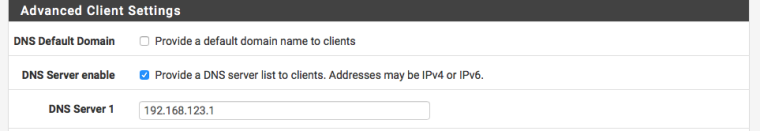
And make sure you provide the local DNS to clients !!
-
Firewall rules - lan- add each of your devices (assign a static up to then from dhcp lease page). Anyways add them again to the above then change the gateway to your vpn gateway
If you don’t have another gateway your vpn isn’t setup properly... my setup like this has been working for years! Pfsense is an amazing firewall