pfsense with Unbiquiti 8-port Switch and VLANs
-
@bcman1984 Have you posted in the ubiquity forums?
Also, I have used nguvu.org as a setup guide for vlans and pfsense. Helped me out significantly setting up wlan's on vlan's.
Following as I do see a new switch in my future. -
Not sure what running an openvpn server has to do with manual.. You mean you ran an openvpn client on pfsense? And you used manual vs the much easier hybrid? Not sure what that has to do with this setup?
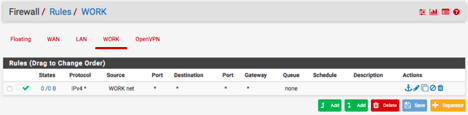
I would suggest you get with unifi for configuration issues with their switches. Pfsense is drop dead easy. A native network on a physical interface is no tagged, its a native network. You create a vlan its tagged with your ID you pick.
Connecting that to a switch the port connected to this physical interface the port would be native untagged with whatever vlan that is 1, or whatever you setup the switch vlan to be for that port untagged. The pvid would be set to this vlan.. Any untagged inbound traffic the switch sees to that port would be untagged on that vlan in the switch. And you would setup tagged for all vlans entering and leaving that port as their tags.
Other ports on the switch you want on a specific vlan for a device would all be untagged in the vlan you want.
-
@mtarbox Thank you for the link, i'll go check it out!
-
@johnpoz said in pfsense with Unbiquiti 8-port Switch and VLANs:
Not sure what running an openvpn server has to do with manual.. You mean you ran an openvpn client on pfsense? And you used manual vs the much easier hybrid? Not sure what that has to do with this setup?
I would suggest you get with unifi for configuration issues with their switches. Pfsense is drop dead easy. A native network on a physical interface is no tagged, its a native network. You create a vlan its tagged with your ID you pick.
Connecting that to a switch the port connected to this physical interface the port would be native untagged with whatever vlan that is 1, or whatever you setup the switch vlan to be for that port untagged. The pvid would be set to this vlan.. Any untagged inbound traffic the switch sees to that port would be untagged on that vlan in the switch. And you would setup tagged for all vlans entering and leaving that port as their tags.
Other ports on the switch you want on a specific vlan for a device would all be untagged in the vlan you want.
You are correct, it was an openvpn client on pfsense not a server, my bad. It was set up that way based on a tutorial i used. Am i still OK to switch it back to hybrid? If so, should i switch it to hybrid and recreate the vlan on pfsense?
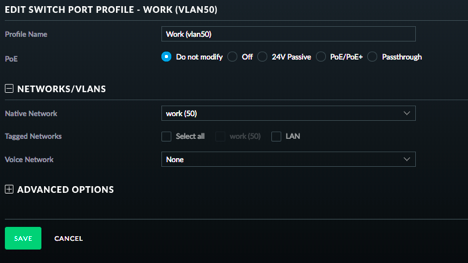
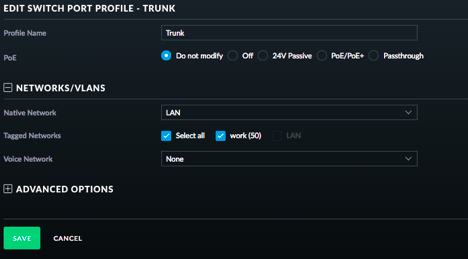
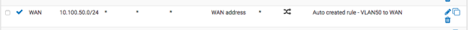
for my trunk, i was leaving the native LAN as untagged, and then tagging vlan50, and then on port 3/4 i was setting vlan50 as untagged so that it would get tagged when leaving the port.
I'll submit a post on unifi's forums to see what i could be doing wrong with the switch config.
Thanks!
-
Are you still using vpn client on psfense? If so then just use hybrid so you can policy route/nat traffic out your vpn interface you created.
There is almost never a reason to use manual... There are alot of CRAP guides out there that is for sure!!
Your setup seems correct as worded.. While I don't use the unifi switches, I do use their AP and read their forums.. And to be honest there seem to be many a post with vlan setup on their switches being lets call it flakey.. What firmware are you running on them? What controller version are you using?
-
currently no, i didn't get very good speeds with it. haven't had much time to dig into it. I will set it back to hybrid, thank you for the tip
I see a lot of guides out there for unifi and their AP's, which i do have one, just haven't set it up yet, i thought i would get the simpler single vlan set up and working on 2 ports before i went with the multiple vlans on an AP, lol.
From what i read with the ports is that if the device does not have the ability to tag the traffic itself, then you need to set the port as untagged to the vlan you want it to be so that it tags it. with the AP's, they have the ability to tag the traffic, so you can just tag it on the port.
for the firmware:
controller: 5.8.28
switch: 3.9.42.9152 -
Yes on an AP your vlans would be tagged for your different SSIDS that are on different vlans.
Your management IP of the AP would be on the native vlan, or untagged network. They have suppose to have added the ability for the AP IP and management to be on a vlan but have not had time to play with that, and currently no need in my network since I just run my controller on native untagged vlan.
I would sniff on your pfsense vlan interface - do you see dhcp discover from yoru clients? Do you see anything in your dhcp logs for the clients dhcp discover?
-
i don't see anything on the pfsense dhcp server logs. restarted the dhcp service just to make sure, and i see the following:
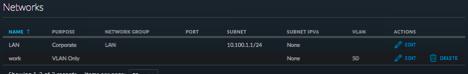
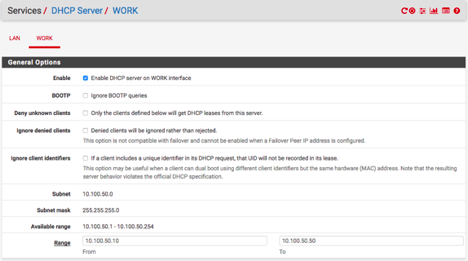
Sep 13 13:00:01 dhcpd Listening on BPF/igb0.50/90:e2:ba:36:e5:84/10.100.50.0/24
Sep 13 13:00:01 dhcpd Sending on BPF/igb0.50/90:e2:ba:36:e5:84/10.100.50.0/24
Sep 13 13:00:01 dhcpd Listening on BPF/igb0/90:e2:ba:36:e5:84/10.100.1.0/24
Sep 13 13:00:01 dhcpd Sending on BPF/igb0/90:e2:ba:36:e5:84/10.100.1.0/24i'll have to get wireshark and see what i can find
-
Well if your not seeing anything - then its impossible to hand out an IP... So looks like your switch setup is not right..
-
i wanted to close the loop on this. I ended up starting over and reset the switch and rebuilt the vlans on pfsense. It is working as expected now, so i must have messed something up previously. Thank you all for you help!