Issue with floating rule
-
I have a BLOCK ALL rule for a host on a LAN interface, and a floating ALLOW rule to allow ICMP traffic from any src to any dest for multiple interfaces. Both these rules match ICMP traffic I'm trying to block from said source, so I've unchecked the 'quick' option on the floating rule. My understanding is that with this configuration, the 'last match wins' meaning the BLOCK ALL rule would apply, but it does not. The floating rule still takes precedent, and the host can ping anything.
I have many other floating rules that I hope to have blocked via the interface rule as well.
-
Show us your rules.
-
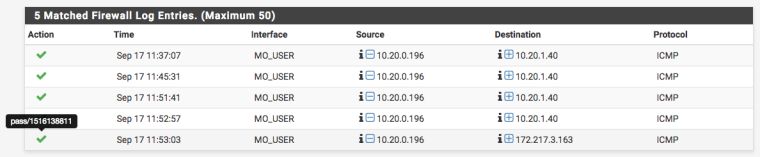
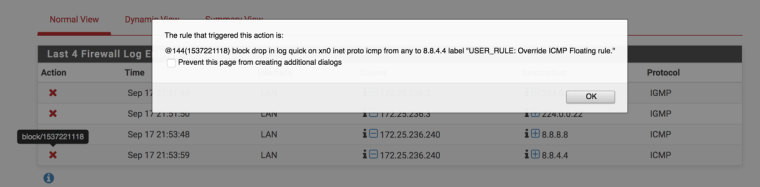
Here's the logs showing the ICMP going through

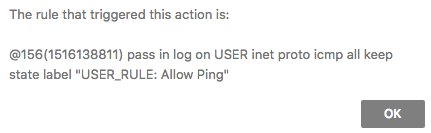
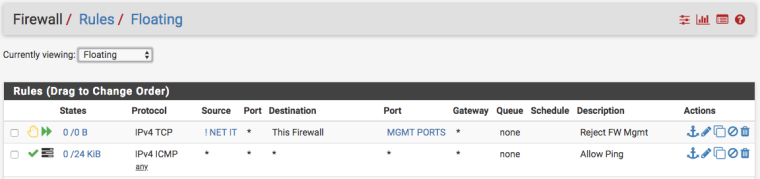
Here's the floating rules. I've truncated the list, the one that triggers is in the screenshot
Here's the interface rules
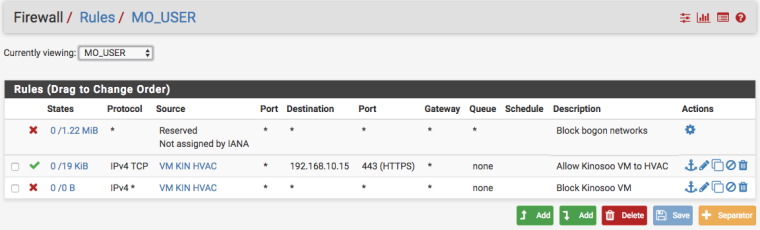
I'm hoping the last rule on MO_USER interface would win over the floating rule that allows ICMP, but it does not.
-
Is there also a USER interface in addition to MO_USER? What you posted looks like traffic originating from USER to MO_USER. That will be governed by rules on the USER tab. MO_USER rules are for traffic originating from, not to, MO_USER hosts.
-
Yes, there is a group interface named USER, which MO_USER is a member of. Here are the rules for this interface group
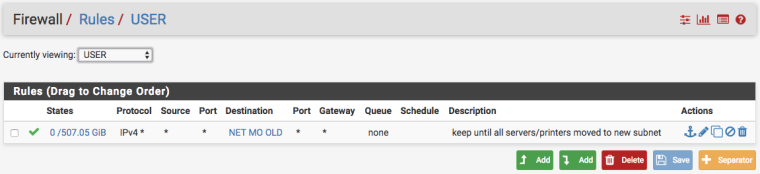
The dest is a private network that i'm migrating from, and doesn't apply in this case.
This is the ping result from the source VM_KIN_HVAC (10.20.0.196)
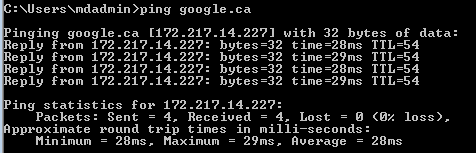
-
OK and what rule is passing that traffic?
Rules are processed in this order:
Floating rules (selectable direction, selectable quick)
Interface Group rules (inbound only, quick always set)
Interface rules (inbound only, quick always set)So, if MO_USER is a member of the USER interface group, that pass rule will pass all traffic including those pings.
-
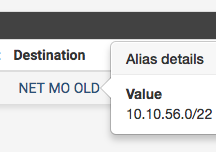
I would agree with everything you said, to the point of where the USER rule would pass the ping traffic, because the destination I'm testing does not match the dest in the rule.
The dest shown on the rule on the USER interface
Here I can show that the source can ping both internal and external destinations. The rule allowing this is the floating rule 'Allow Ping'
I'm sure I'm missing something trivial...
-
You posted that state passed by rule @156 which looks like a floating rule on USER in the inbound direction.
You also pass the same traffic on the interface group rule, it looks like.
Interface rules on MO_USER have nothing to do with pings to hosts on MO_USER.
You have a pass floating rule for the ping from source any to dest any.
That traffic would have to be subsequently blocked by a rule or it will be passed. What rule do you think should block it?
You might need to make a complete diagram of the part of your network complete with interface addresses, names, and the pertinent host addresses. I'm not tracking something because your interface names mean nothing to me and you've used aliases so the rule screen shots don't give the whole picture.
Also need to know exactly what interfaces are in the USER interface group.
-
For testing purposes, I have logging enabled only on the floating rule that allows pings, so I know that's the one passing the traffic, and not any other. The floating rule applies to the interface group USER, which MO_USER is a member of. Not sure if thats the part I'm not understanding correctly, because I'm expecting the last rule listed on the MO_USER interface to block this traffic.
If this isn't clear enough, I will try to explain myself better tomorrow, with diagrams and details.
-
Yeah. Have to assume far too much based on that description (no specifics like IP addresses and interface networks).
Note the counters on the last block rule on MO_USER has no matches/hits.
Working here:
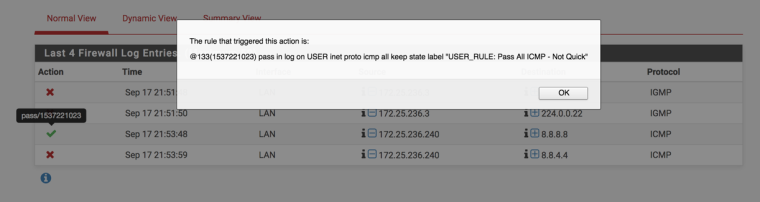
-
Hi Derelict,
Just getting another chance to look things over today, and realized that its working as expected without making any changes. It must have been an issue with open states, even though I killed the ones I could find, or could it be something else?
-
Not sure what you were initially seeing so any feedback would be just a guess.