Can access LAN web GUI from DMZ
-
Hi,
I have blocked access to the admin GUI from within the DMZ using the IP address of the DMZ interface.
I am unable to block access to the admin GUI from the DMZ when I use the IP address for the LAN interface. Any help would be appreciated. No matter what I do I can access the web GUI using the LAN interface IP when in the DMZ.
Kind regards
Richard
-
@richley said in Can access LAN web GUI from DMZ:
I am unable to block access to the admin GUI from the DMZ when I use the IP address for the LAN interface.
?
If you allow nothing on the DMZ there will be no access to the WebGUI.If you have widely opened firewall rules on the DMZ you have to set a block rule to the top of the rule set. At destination select "This firewall (self)" and enter the management port you use.
This should block access to any interface address. -
Hi viragomann,
I have created a rule that blocks access to the admin GUI from the DMZ when using the DMZ interface IP address in a browser and this works. If I enter the LAN IP address for pfsense when in the DMZ I am able to get to the login page this is what I need to block.
Kind regards
Richard
-
@viragomann said in Can access LAN web GUI from DMZ:
f you have widely opened firewall rules on the DMZ you have to set a block rule to the top of the rule set. At destination select "This firewall (self)" and enter the management port you use.
This should block access to any interface address.Post a screen shot of your dmz firewall rules, for a true DMZ it should look something like this:-
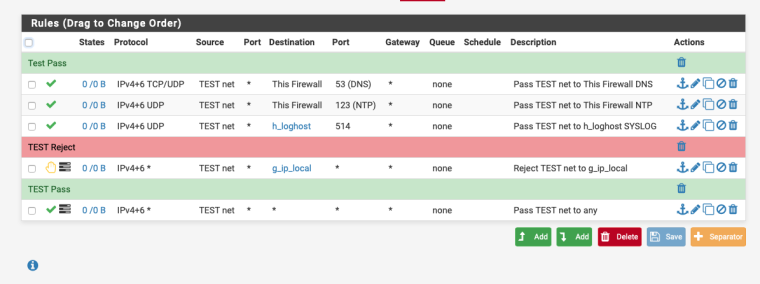
g_ip_local is an alias that contains all my ipv4 & ipv6 subnets.
-
Hi viragomann,
I have attached a screenshot as requested.
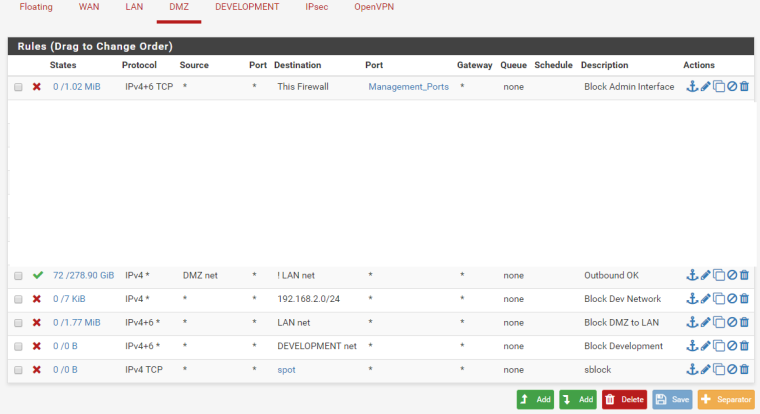 .
.Kind regards
Richard
-
Looks to me like its something in the rules you've blanked out or maybe its connecting via IPv6 and you need to change the rule to IPv4 & IPv6.
Have a look at the states on the pass rules.
-
So that rule should block any access to pfSense on management ports.
Maybe a floating rule is permitting the access?
However, consider that adding a block rule does not kill already existing states (connections). So you will have to kill existing states manually in Diagnostics > States > States.
-
Yeah looks like your whited out a huge amount of rules?
Also even the rules can see make no sense
You have an any rule that says hey DMZ net if your NOT going to lan net your allowed. Well below that a rule that says blocking going to 192.168.2/24 which is Dev Net? Why would that not be allowed in the dmz to NOT lan net rule?
Do you have downstream networks other than dmz net connected... And then below another rules that says block dev net, is that not 192.168.2/24 that you already blocked above, etc.
Please do not hide rules if you want help.. Its very simple. Rules are evaluated top down as traffic enters an interface. If a rule matches it wins and no other rules are evaluated. So run through your rules from the top. To see if traffic should be allowed or blocked. If you have a rule that blocks before an allow - and your still seeing allowed traffic then you prob have to clear a state from before you created that rule.
As to that rule on top blocking - if this firewall then it should. But don't know about his states, nor what he has in the alias.