Advice - Allowing client to bypass pfblocker-ng
-
Hi there,
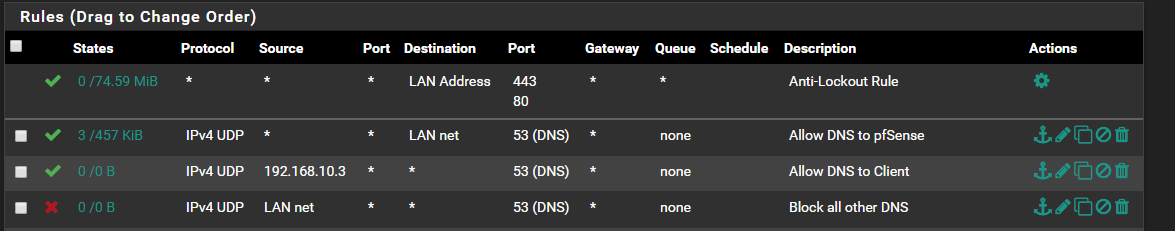
so I've installed pfblocker-ng and setup my dns rules (see attached) on the firewall and added my lists for DNSBL and all is working perfectly. I lookup a known bad site and it resolves to 10.10.10.1 .. excellentHowever I want to allow my desktop smartphone to bypass pfblocker and I'm having issues getting it to work. I followed Lawrence on youtube and he advise to put a rule at the top of the list to allow an IP to DNS before the block (also in attached pic) but no joy .. I still get sent to 10.10.10.1 on a lookup.
any help appreciated

-
There is one post here
https://forum.netgate.com/topic/129365/bypassing-dnsbl-for-specific-ips
-
@ronpfs said in Advice - Allowing client to bypass pfblocker-ng:
There is one post here
https://forum.netgate.com/topic/129365/bypassing-dnsbl-for-specific-ips
That worked :) Thank you very much.
For newbies like myself.. a little hint .. the custom option is at the end under DNS resolver.
-
Lawrence rule serves to allow host 192.168.10.3 to change its own DNS server setting and use an external one, bypassing internal DNS resolver and then the DNSBL filter. Requests to access an external DNS server from all other hosts are denied by the last firewall rule above.
However, if host 192.168.10.3 keeps using the internal DNS, its calls to DNS are subjected to the DNSBL filter as all the the other host calls. In this case the solution to bypass this filter is the one proposed above.
-
The allow rule to pfsense is wrong... It allows access to ANY thing on the lan net on port 53 UDP.. So any client on the lan net could access any dns they want that resides on lan net. That rule should be set to pfsense Lan IP as the destination.
It should also be both udp and tcp
Same for the other rules - dns can be both udp and dns... While allowing only udp will prob work for most stuff, if the client needs to switch over to use tcp for a reason, then the dns queries would fail.
-
I'd change the allow rules to "LAN net" (or in case of the .10.3 an alias) and the block rule to source any? So you block out unwanted clients, that may have been connected to the network and setup with an alternative IP range?
And wouldn't "This Firewall" be good instead of "LAN address" in case you upgrade that to a CARP setup?Just a thought
-
@johnpoz Is possible if you can show an exemple, thanks
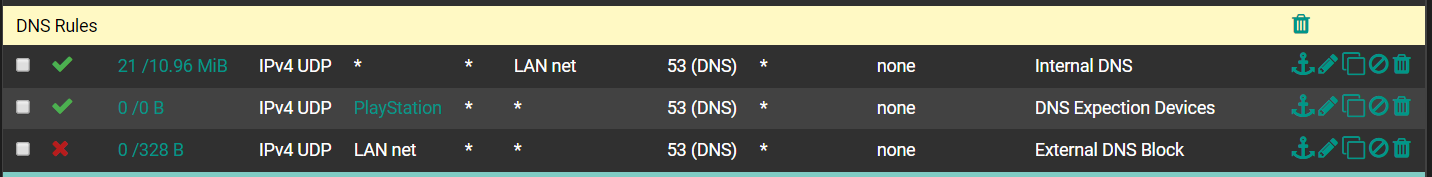
-
@manjotsc Here
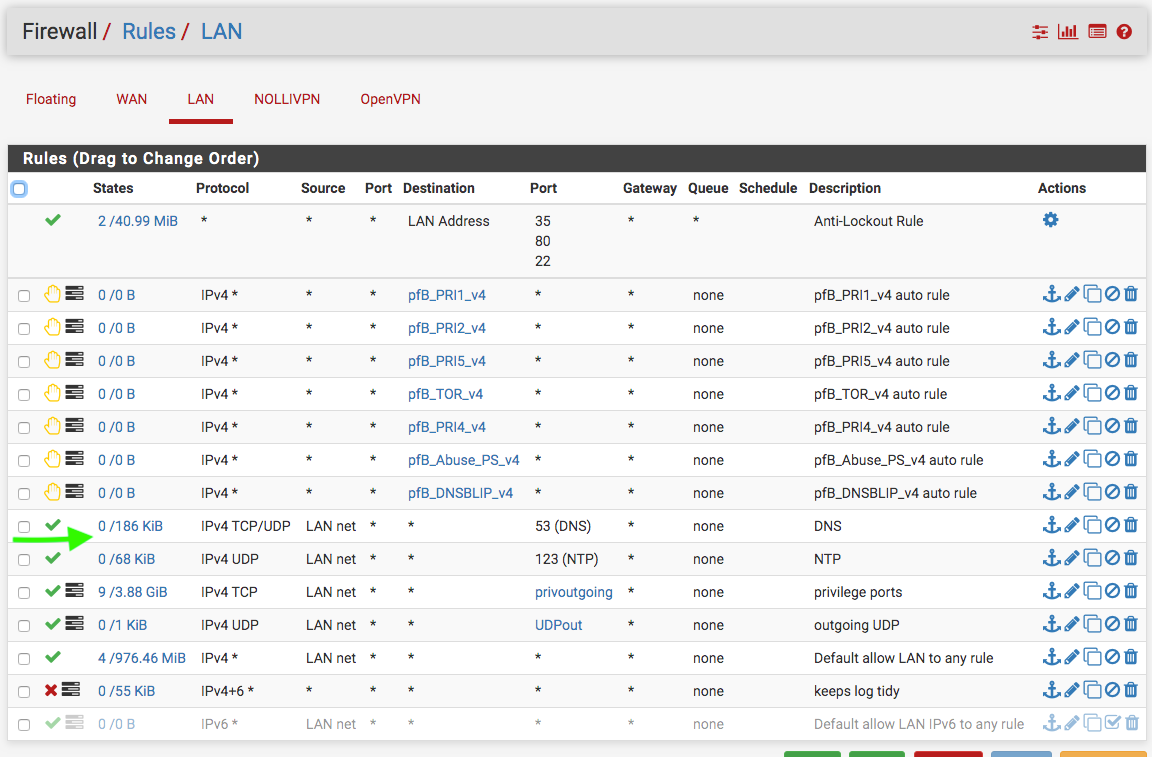
-
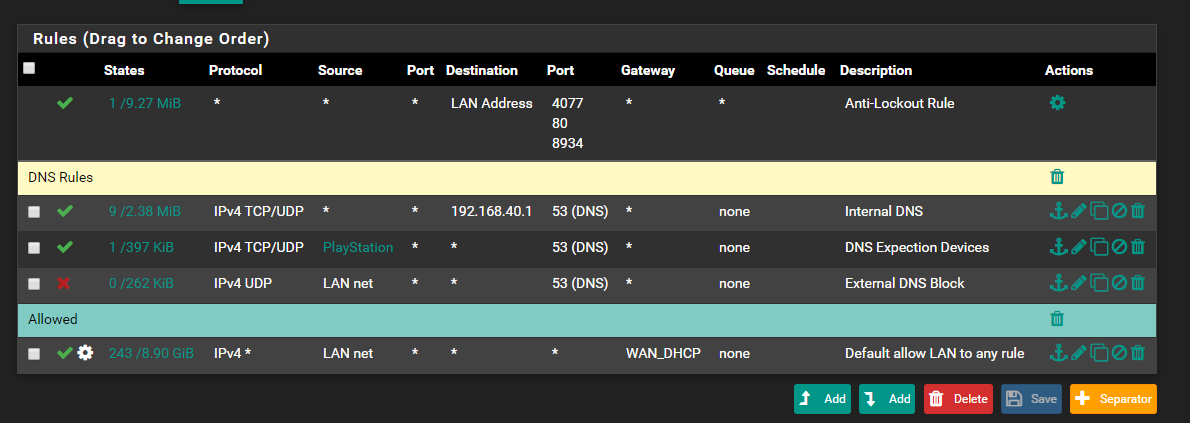
@NollipfSense But there is no usage in states collum of DNS Expection Devices, it's 0/0B it's normal? And also one thing, My LAN Devices are able to use any DNS Server. Regardless of rules.
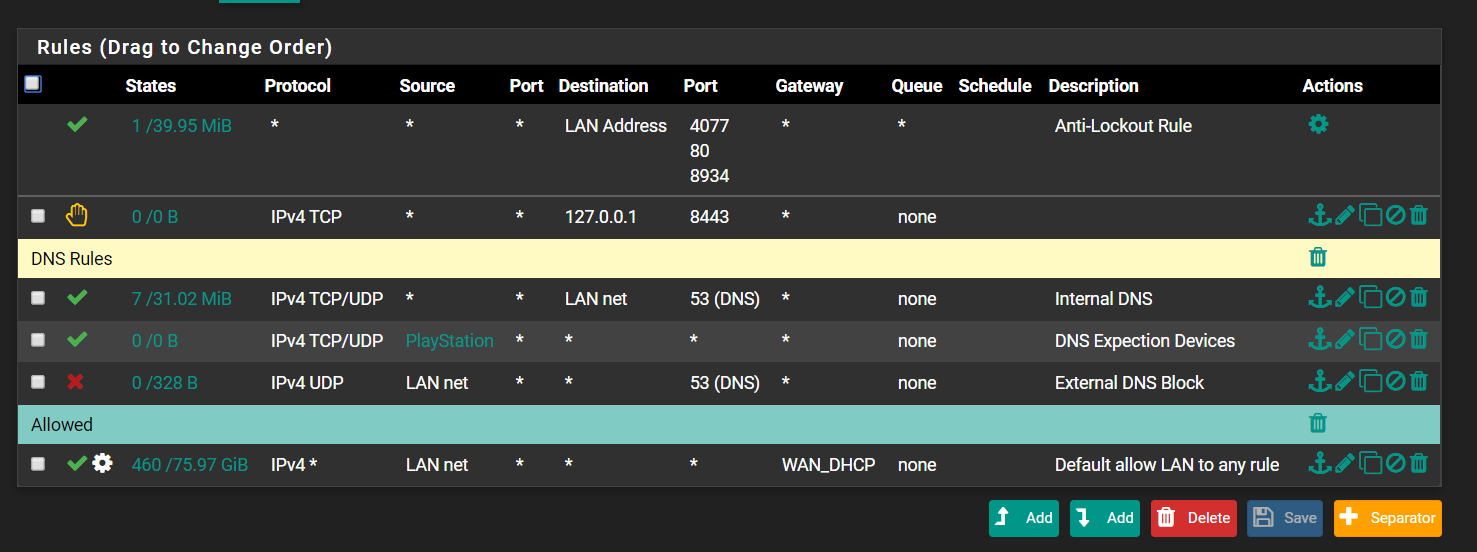
-
@manjotsc said in Advice - Allowing client to bypass pfblocker-ng:
My LAN Devices are able to use any DNS Server. Regardless of rules.
You understand that in no scenario does lan device talk to pfsense to talk to another device on lan... Unless your using pfsense as a bridge and the device they want to talk to is on the other side of that bridge.
I take it those rules are on your lan interface.. If so that rule to lan net destination is pointless.. Other than that would talk to pfsense IP in lan net... But it normally would be written with lan address if that is what you want to allow.
Clearly your rules are blocking hits to other dns, see the 328 B of traffic.
And your playstation - your letting it do more than dns with that rule.
And just not a clue to when you think there would be a dest of 127.0.0.1? Are you doing a port forward somewhere trying to redirect stop it with a rule? To 8443?
-
Thanks for recommendations, and about 127.0.01 rule, i dont know why did it.
Does it looks good now?
-
Hello All.
I would like to ask about the following. I have some IPs bundled in an ALIAS and these IPs should bypass pfBlockerNG. When I unselect these IPs by their dedicated VPN-Interface in "Select Outbound Firewall Interface", these IPs are still get filtered by pfBlocker. Is this the reason for for this because of checking the option for floating rules (Open VPN) in DNSBL firewall rules?
Nevertheless, I found wesfox's link for bypassing single IPs. Would this be the right way to bypass pfBlockerNG for some LAN IPs?
Thx for your support in advance.