Intel NUC - Hyper-V and pfSense
-
I want to achieve following setup:
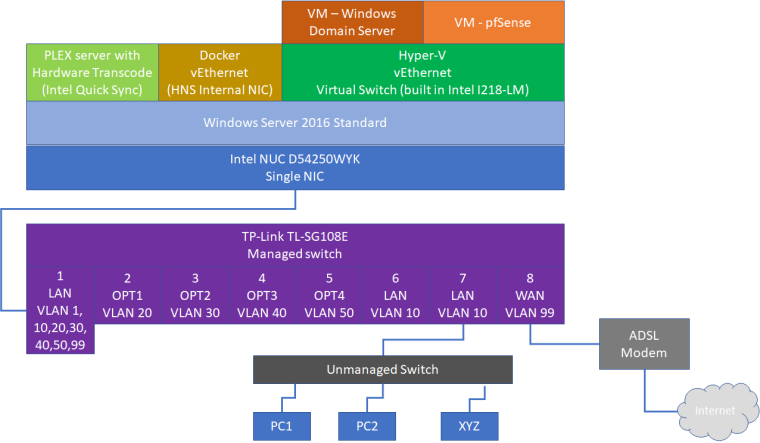
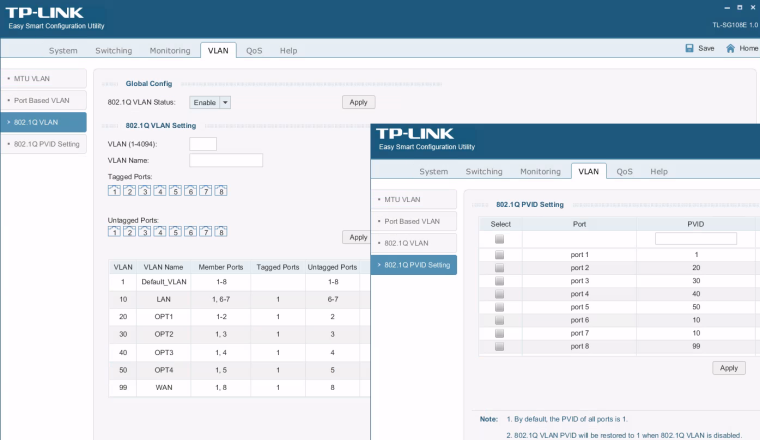
Intel NUC running Windows Server 2016 with Hyper-V role (to run few virtual machines, AD server, etc) plus virtualized pfSense. I have managed switch on which I set up following VLAN's: 10 - LAN, 99 - WAN, 20 - home automation. pfSense has been also set up as follows: VLAN 10 - LAN, VLAN 99 - WAN, VLAN 20 - OPT1.
I cannot however get it all to work.
I tried to change Virtual LAN Identification to 10 and 99 for the pfSense virtual machine Network Adapter - no difference, no internet.
How to set it all up correctly? -
How are you testing it? Where from?
Is pfSense using a DHCP WAN? Does it get an IP?
How is Hyper-V configured?
Steve
-
pfSense is running as virtual machine on Hyper-V on Intel NUC (I don't want to sacrifice entire PC only for router) and is set as follows:
Switch Port | pfSense interface | VLAN ID | IP
1 | LAN | VLAN 1,10,20,30,40,50 | static IP 192.168.1.1
2 | OPT1 | VLAN 20 |
3 | OPT2 | VLAN 30 |
4 | OPT3 | VLAN 40 |
5 | OPT4 | VLAN 50 |
6 | | untagged | DHCP from pfSense LAN interface
7 | | untagged | DHCP from pfSense LAN interface
8 | WAN | VLAN 99 | DHCP (expected IP from 192.168.88.1/24 but not getting anything)For testing, it is connected to my current network, so it should get IP from 192.168.88.1/24 but it is not reporting any IP.
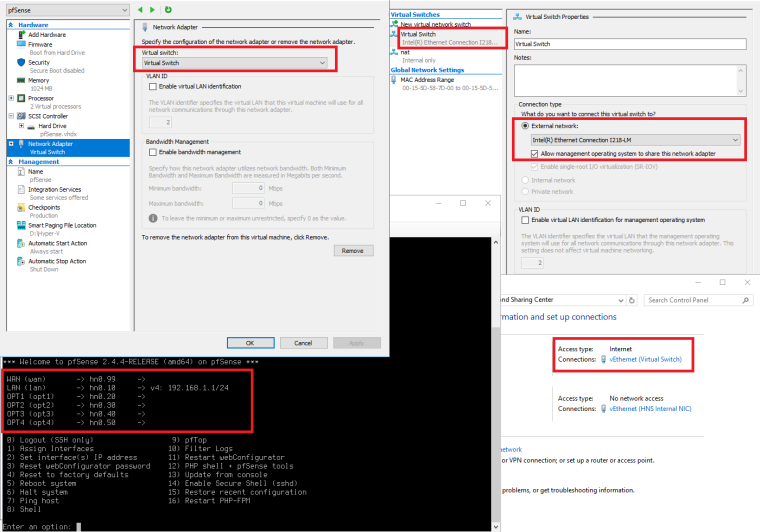
I'm attaching pictures describing the entire setup. Hopefully they are clear enough.
I'm more than sure that I'm missing something here, so your help would be greatly appreciated.
-
The thing that stands out for me there is that you don't have the interface reserved only for hyper-v. So the host OS and the other things running on it can access the DSL modem unfirewalled. It also means the host might be pulling a DHCP lease directly in which case I wouldn't expect hyper-V to be able to.
My Hyper-V experience is very limited though.

Steve
-
@stephenw10 Thanks for your feedback.
Intel NUC has only one single network card so there is no other option than sharing that single NIC between everything: Operating System, Hyper-V, Docker, etc.
Speaking of isolating network traffic - this should be a problem due to VLAN implementation on the managed switch. All WAN communication goes over VLAN 99 which is no used by anything else, so it should be safe and no external traffic should be visible or interfere with internal LAN traffic. I'm not an expert though. -
I think I just sorted it all out!
To let pfSense run on Hyper-V hosted on single network adapter Intel NUC with multiple VLANs, and together with virtual machines as well as other local Windows services and programs, I took following steps:
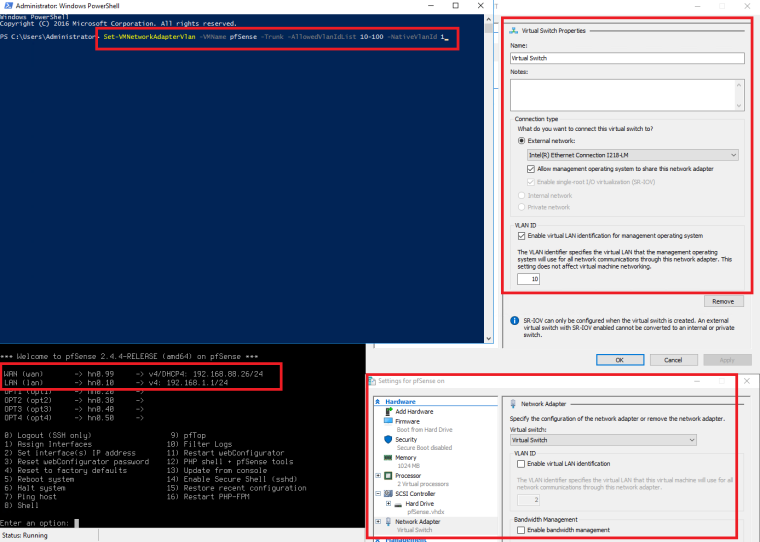
- Run PowerShell as Administrator
- Run: Set-VMNetworkAdapterVlan -VMName pfSense -Trunk -AllowedVlanIdList 10-100 -NativeVlanId 1
note: pfSense is the name of Virtual Machine and AllowedVlanIdList covers range of VLANs configured for pfSense. NativeVlanId is left with default ID=1
more about PS command: https://docs.microsoft.com/en-us/powershell/module/hyper-v/set-vmnetworkadaptervlan?view=win10-ps - Change Hyper-V Virtual Switch to enable VLAN = 10 (as configured on port 1 of the TP-Link managed switch - see my first post).
note: do not enable any VLAN identification on Virtual Network card configured for pfSense. - Change for all other virtual machines VLAN to 10 (do not enable VLAN inside virtual machine - leave default VLAN ID = 0)
Final VLAN configuration as per component:
- Intel NUC network card - no change, default config (no VLAN)
- Hyper-V Virtual Switch - enable VLAN = 10
- pfSense virtual machine Network Adapter VLAN disabled
- every other Hyper-V virtual machine's Network Adapter VLAN = 10
- no need to configure or change anything for Docker
I'm yet to test this configuration so any comments welcome.
Screenshot for reference.