How to prevent DDOS using Snort?
-
Unless you created a port forward, or running openvpn or something where the wizard would all traffic on your wan to port vpn listen on ALL unsolicited traffic to your wan is dropped/blocked out of the box.
Please post your wan rules as asked, and actually state why you feel you were attacked? A couple hundred hits? Is that even your WAN.. the 5353 and 1900 are most likely broadcast traffic from your lan side.. Or its BS noise from your ISP layer 2 on your wan.
-
-
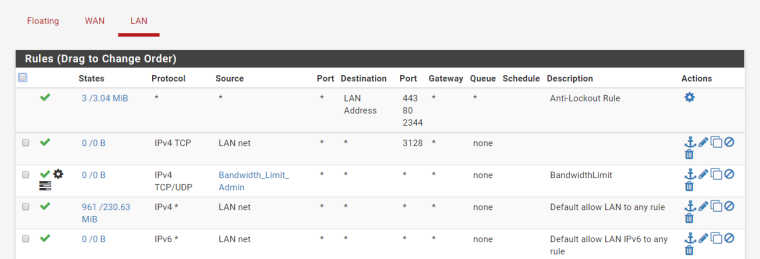
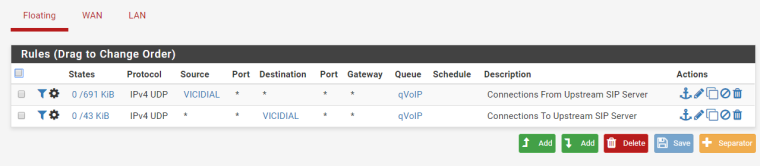
Any floating rules ?
-
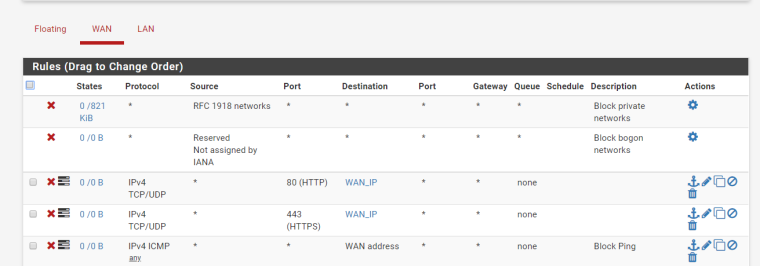
-
The rules on your wan are pointless!!! All interfaces have default deny on them.. Its pointless for those rules unless you have turned off default logging and just want to log those ports and pings.
And again where is this attack?, I see nothing in your logs but some very LOW level amount of noise...
-
@johnpoz said in How to prevent DDOS using Snort?:
The rules on your wan are pointless!!! All interfaces have default deny on them.. Its pointless for those rules unless you have turned off default logging and just want to log those ports and pings.
what should i do sir ? delete the port 80 and 443 rules? to avoid incoming SYN flood to my WAN IP?
-
What? They are pointless in that fact that they are dropped by default... There is no reason for those rules unless you had turned off default logging of default rule and wanted to log them as see you have enabled logging on the rules.
Those have ZERO to do with any SYN flood ;)
Again where is this attack? If you had say 1000 hits in a second or something you might have something to investigate... But you have nothing but very very low amount of typical noise in your logs.
-
@johnpoz sorry noob question where i can check if i got 1000 hits per seconds ? maybe im just curious last night ?
-
Hey @jlee18 , I am actually incl. the snort block getting approximately about 0 to 3/4(/short times maybe max10) hits per second. After these there is at least a Minute where is often not even one lonely hit (log-alert, under snort or even system logs -> firewall log)
Many are ET or Portscans automatically blocked by pfSense (with or without snort, for example as the firewall blocks incomings on WAN by default)
As I worked it out this is all the normal "background noise".
If I am surfing the WWW the "hits" (alerts, blocks and so on) increase radically but even if there is nothing online (TV off, Printer on standby, any PC or Smartphone "off") there are at least 500 hits per 12 hours on my WAN. All "normal" as suggesting as Portscans, "trial and error brake-ins" or as I guess security look-offs (trying to find malicious or malware-spreading Command & Control-Hosts or similars...)
That nerves, yes. But aint my Business so my Firewall blocks em and that's all at least I can do about :-D
I didnt read the Thread all again but read it several Days ago (sorry for that!)
But I just wanted at least give you an answer on how to at least get an overview of how many hits per second might get produced on your Firewall.As mentioned: I get between 0 and max10. Sometimes there's even a minute nothing happening on WAN and than there is a hit every 20 seconds or even every minute. And very rarely there seems to be combined operations or "randomly happened hits" which can reach up to lets say maximum 10/hits per second (for just a few seconds)
I am noob as you and just wanted to share my experience with you. If you got any further questions, here's the right place to state them. :-)
BTW I got an own thread where now nobody answered for 2 1/2 Days but it's okay...gotta read more about and (hopefully) worked it correctly out for me :-D