XG-7100: multiple VLAN interfaces on single physical port
-
On SG-8860 I could create serveral VLANs on a physical interface, and assign then each VLAN to a logical interface. I'm trying to do the same with XG-7100, but can't seem to find the way (or documentation) to do it.
Let's assume I need 2 VLANs (11, 12), and want to setup port ETH4 as parent port for them, to create later LAN11 and LAN12 interfaces. How should I proceed? Is it possible?
What I did so far is:
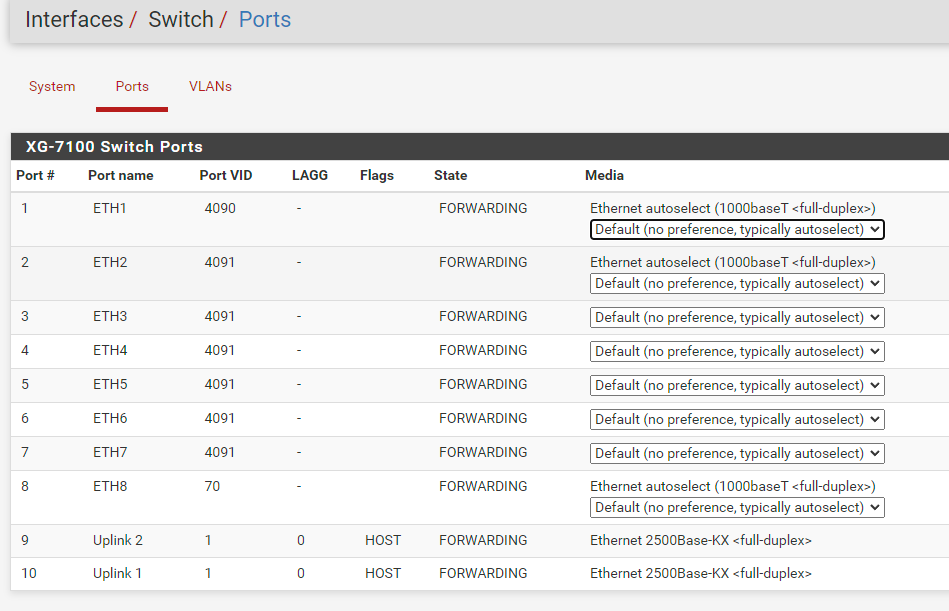
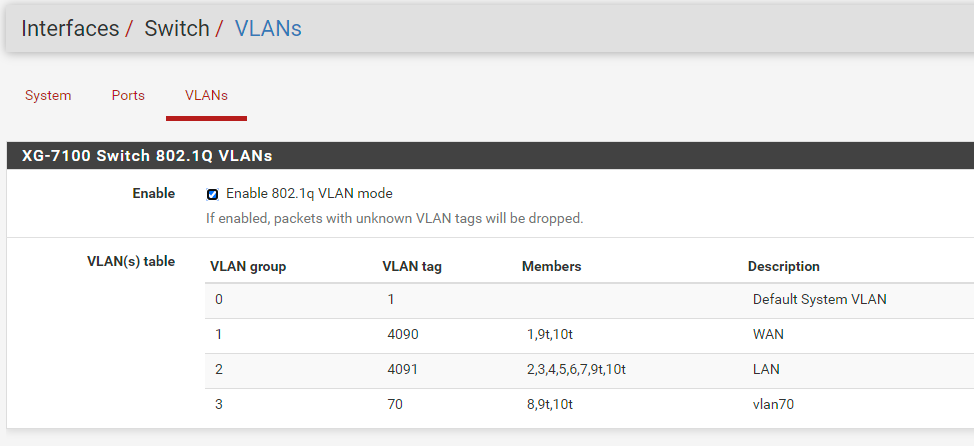
- Create VLAN's 4084, 11 and 12 on lagg0
- On Interfaces / Switch / Ports assigned PVID 4084 to ETH4
- On Interfaces / Switch / VLANs assigned:
VLAN group 4, VLAN tag 4084, Members 4,9t,10t
VLAN group 5, VLAN tag 11, Members 4t,9t,10t
VLAN group 6, VLAN tag 12, Members 4t,9t,10t - On Interfaces / Assign:
Interface LAN11 on Network port VLAN 11 on lagg0
Interface LAN12 on Network port VLAN 12 on lagg0
After this, I can't reach the interface's IPs
I'm not sure about assigning tag 4084 as I don't need untagged traffic, just the two tagged VLANs
Any help would be much appreciated
-
That looks right.
Did you add firewall rules to the new interfaces to pass traffic?
What are you connecting to ETH4? How is that configured?
-
Yes, firewall rules are OK, just can't get even ping to work.
ETH4 is connected to an HP switch trunk port, tagging on all vlans
-
If it's tagging on all VLANs 4084 won't work because that's untagged on ETH4.
If you say it's all correct we'll probably need screenshots because what you're posting looks correct.
-
OK, so I took out 4084 from Switch VLAN tags. I just added it to try, but wasn't there on the first place.
Here're the screenshots. Not exactly the same I was describing because I wanted to make it generic, but the config changes accordingly
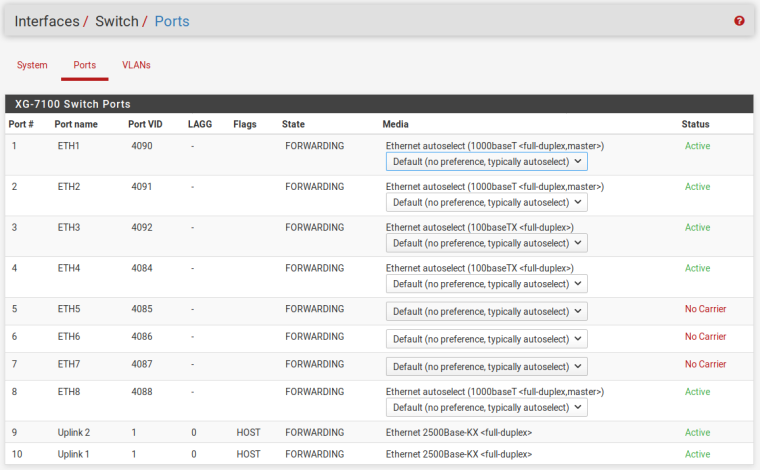
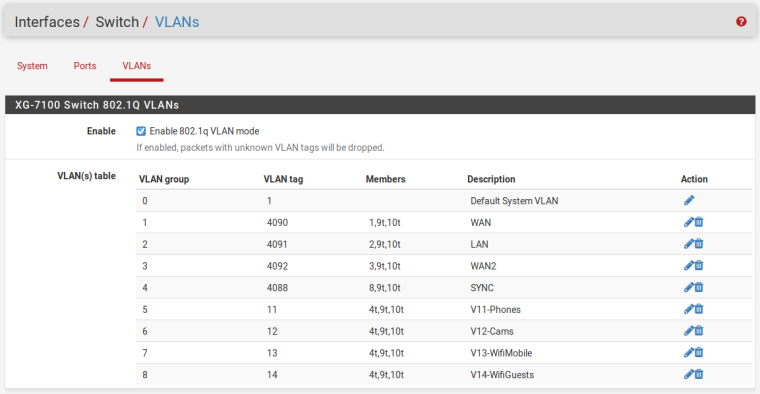
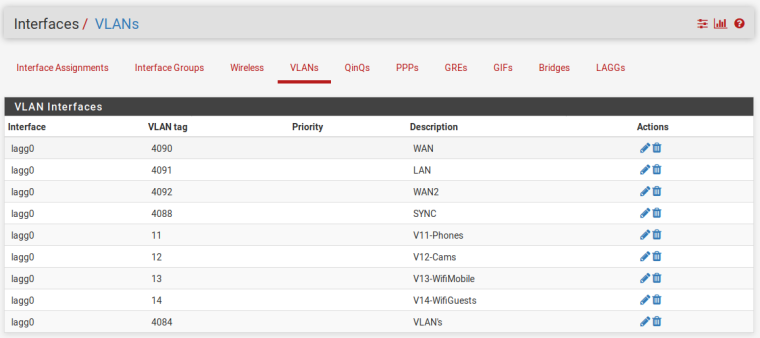
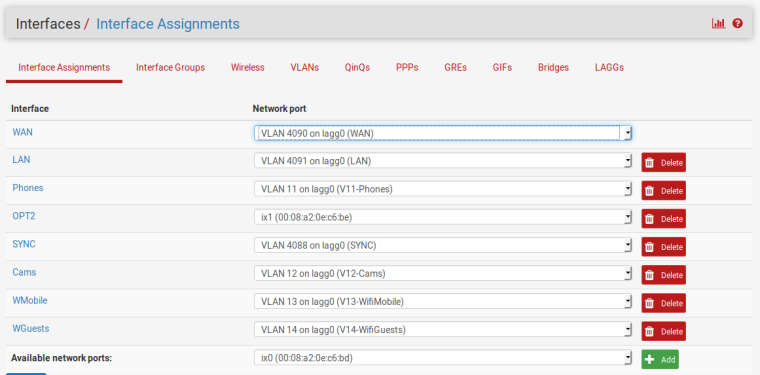
-
Any ideas on this? I'm about to set each VLAN on a physical port, but that's ugly and changes my project.
As additional clue, capturing traffic I noticed bad checksum errors. After disabling checksum offload errors are gone, but still not working.
Any help will be appreciated, I'll be getting out of hair soon :)
-
I don't see a pfSense interface for WAN2 (4092).
It is normal to see checksum errors when checksum offloading is enabled because at the point of the pcap the checksum has not been calculated yet since it's done by the ethernet hardware.
You might have to explain what exactly isn't working at this point if you want more directed feedback.
-
Yes, WAN2 is not being used yet.
What exactly isn't working? None of the VLAN (11-14) interfaces can reach the net, in any direction. On those interfaces, any traffic originated on the host or directed to it seems to die on the physical port. Looks like a disconnected port.
On SG-8860, with the same setup (4 VLANS on a physical port), with the same rules and same configuration on the switch port it's connected to (tried 2 different switchs so far), it works as expected.
I never had this problem before. Just setting up XG-7100 to be a CARP backup node, the other interfaces work just fine, but can't get VLAN interfaces to work. I don't know if I'm missing something about how the new "switch interfaces" work, just not sure what else to try.
Thanks
-
Can you ping the closest interface address?
Did you add firewall rules? Did you check outbound NAT?
-
What is the configuration of the switch connected to port 4?
-
Yes, all that. I also captured traffic but nothing shows on those interfaces. Examples:
Host A (8860) 192.168.14.10 (VLAN14)
Host B (7100) 192.168.14.11 (VLAN14)- If I ping from host A to B, I can see icmp traffic coming out from A, and nothing getting to B (it works OK with any other host on the net)
- If I ping from host B to A, I can only see ARP traffic coming out from B, asking for B's MAC (it doesn't work pinging any other host on the net)
- If I capture packets on VLAN interface 14 on B, I don't get any broadcast from the network either. I see VRRP coming out, but not getting to B or the net
Config on the switch: it's a trunk port, PVID 1, tagging all VLAN's. I use the same switch port configuration with the physical port I use for VLAN's on 8860, and it works!
Also tried setting port ETH5 as untagged VLAN 14, on an untagged switch's port, and works OK. So it's not a switch trunking or firewall rules issue
-
Just for the record. I finally found the cause of this: the interface was connected to the wrong switch port. It's hard to spot things like this when working remotely, but that was the problem.
Thanks anyway for your help
-
Thanks for letting us know.
-
@maliaga Hi, how can you have vlan 4091 AND vlan 11 on the same ETH2 port?
-
@nick-loenders said in XG-7100: multiple VLAN interfaces on single physical port:
@maliaga Hi, how can you have vlan 4091 AND vlan 11 on the same ETH2 port?
Tagged or untagged?
-
@derelict I don't fully understand the difference.
Basically I want one network cable connected on one port , eg ETH2 and pass two vlans on it, the 4091 (LAN) with DHCP 10.0.0.0/24 and the vlan 70 (VLAN) with DHCP 192.168.70.0/24
Problem is, I could connect the LAN on ETH2 and the VLAN 70 on ETH8 so with two cables to the first switch, but there is only 1 cable going from the first switch to the second at this time :(
-
@nick-loenders But you need to say whether you want one VLAN untagged and one tagged or both tagged (both cannot be untagged on the same port so that is not an option). It depends on how the device you are connecting to that port is configured.
-
-
@nick-loenders And then it went quiet :)
-
@nick-loenders Considering this is in Off-Topic and Non-Support Discussion I would expect it to get lost.
You still didn't specify what you wanted tagged and untagged and where.
How is the switch port connected configured?