All freeradius eap-tls authentications fail when an SSL revocation list is enabled
-
Ok - so I parsed out the x509 crl into its own pem... Then checked it with openssl and you can see no certs listed.. Before this was never added to the ca_cert.pem that freerad uses for the CRL.
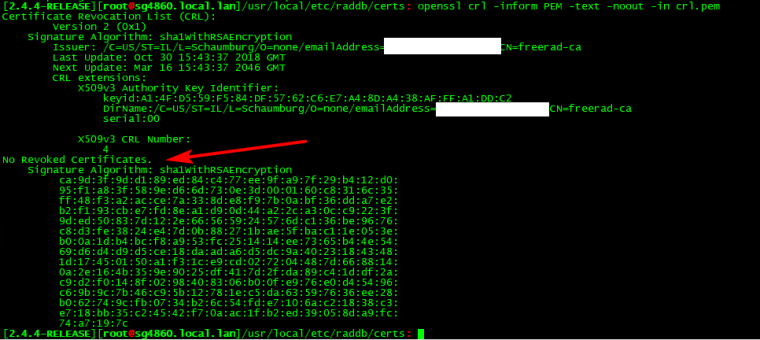
-
Maybe change this bit of code in
/usr/local/pkg/freeradius.inc:if ($crl_cert != false) { $crl = base64_decode($crl_cert['text']); $check_crl = "check_crl = yes"; } else { $check_crl="check_crl = no"; }To this:
if (($crl_cert != false) && !empty($crl_cert['text'])) { $crl = base64_decode($crl_cert['text']); $check_crl = "check_crl = yes"; } else { $check_crl="check_crl = no"; } -
Your the developer ;) Do you need a report of this to implement that? Or can you put it in without a redmine.
I'm not exactly sure what
$crl_cert['text']Actually does.. Normally that is a part of an array right.. To be honest having a hard time following what exactly you change is doing different. Other then doing some extra check on some variable.
-
I just meant to try that change to see if it helps.
The text is the PEM generated content of the CRL that gets updated when the system updates the CRL, usually when adding or removing a certificate or making another change to the CRL.
If that text is empty it would explain why you hit the error condition you did.
-
Oh would prob have to start over to try and recreate the problem.. Since its working for me now.. like I said when back to empty crl and its working, etc.
Maybe the OP can chime in.. It works just fine - even with empty crl it adds the crl to the ca_cert.pem file.
-
While it seems that you guys have it working for yourselves, at least with a blank CRL, my original issue still remains.
I never cared about blank CRLs, this was only a test I tried to see if a blank CRL would work any better than a populated one. My issue is that when any CRL is enabled, my logon fails, even though my cert is not in the CRL. I've tried deleting and recreating the CRL as well as using just a blank CRL, but the only time I can authenticate is when I leave the CRL setting as none.
-
And you validated your CRL is actually getting added the pem file?
-
There is a: -----BEGIN X509 CRL----- section in ca_crt.pem that appears when I enable the CRL, there is no crl.pem that ever appears.
-
there wont be... Pull out what gets added and look in what is in the CRL... you can do that with the cmd I posted above.
This works fine for me with either blank crl or crl with different cert revoked - my client that is not listed the crl. When i get home tonight I will revoke my client so that it blocks it... Then remove it from the crl, etc..
if your crl is getting added, your going to have to look to see what is in there - maybe your blocking your clients cert? Once I got the crl to be added to the ca pem, I have not been able to duplicate your problem.
-
I decoded the CRL and found 17 revoked certs, exactly the number of certs in the CRL displayed in the GUI, none of them were the serial of my cert. I added my cert in and see that it's added the CRL. Then I removed it and restarted freeradius. My cert was still in the revoked list in ca_cert.pem. So I changed the setting to none and back, this removed my cert from ca_cert.pem. In spite of this I still can't logon with my cert unless the CRL is set to none.
-
Are you actually restarting freerad when you change the certs listed in your crl?
I can not duplicate this
Nov 3 06:02:04 radiusd 29895 (7) Login OK: [j-iphone] (from client uap-pro port 0 cli D0-C5-F3-1F-EB-FF) 192.168.2.2 Nov 3 06:08:08 radiusd 78645 (27) Login incorrect (Failed retrieving values required to evaluate condition): [j-iphone/<via Auth-Type = eap>] (from client uap-pro port 0 cli D0-C5-F3-1F-EB-FF) 192.168.2.2 Nov 3 06:12:49 radiusd 95969 (7) Login OK: [j-iphone] (from client uap-pro port 0 cli D0-C5-F3-1F-EB-FF) 192.168.2.2Not in the CRL... login fine, put client in the CRL - blocked!! Pull his cert out of CRL fine..
-
@smacdoug why don't u remove all the certs involving freeradius and remove freeradius, reboot pfsense, and then install freeradius again. It will generate new default certs that you can use or remove and create your own certs.
-
I'm restarting the freeradius server using the Status-Services and clicking on the restart icon for radiusd.
In terms of deleting all my certs ans rebuilding from scratch, I'd prefer not if I can avoid it. Freeradius is authenticating all my WiFi users. They're all working fine as long as I don't enable a CRL. Creating all new certs to distribute to all my clients is something I'd prefer not to do.
-
And your seeing it restart in the log?
I have tried to duplicate this.. Other than the problems I had with it not adding the CRL at all, which fixed once I put in a cert.. I am not having any issues with this..
Maybe if you run it in debug mode you can get more info to figure out where the problem is.
-
Ok. When I do that I see this in the log which looks relevant:
eap_tls: ERROR: SSL says error 12 : CRL has expired
Since this is a new CRL I'm not sure why it thinks it's expired already. If I run your openssl command I see this:
Last Update: Oct 30 14:47:34 2018 GMT
Next Update: Feb 8 08:19:18 2010 GMTWhich doesn't seem to make sense.
-
No sure doesn't so yeah that would explain the issue..
Just create a new one.. How many days are you putting in for lifetime... Are you importing or creating?
-
Is this on ARM or amd64?
Maybe it's hitting a 32-bit rollover in UNIX timestamps at 2038.
-
It's ARM (Netgate SG-3100)
If I change the default lifetime from 9999 to 3650, I get a correct expiry of 10 years in the future, if I double that to 7300, I get September 2002.
If I leave it at 10 years, the my radius authentications work.
Us this rollover something that can be addressed in a pfsense update?
-
I have a sg3100... Let me give it a try.
-
I can look into adjusting the defaults on ARM, or for everyone: https://redmine.pfsense.org/issues/9098
Curious that it didn't happen on 2.4.3, but we did change to a pure PHP CRL library on 2.4.4. We had been using a PHP openssl module patch before.