Best use of pfBlocker
-
I'm trying to figure out the best way to go about implementing pfBlocker. I've had it set up on several units and it runs fine and has helped stop its share of breach attempts, but just blocking many countries isn't ideal. Instead I've read we should just whitelist the countries we do want to use. To that end, why is pfBlocker designed to just go through and select all of the countries to block? Is there a way to invert it and have only select countries to allow instead? I know pfSense blocks all connections by default but if you're running a mail server, web server, RDP server or some other internal server and you want to limit it's exposure I find pfBlocker to be ideal. I'm looking here and I can see a custom pass list being created, but that appears to me that it's giving those countries access past the firewall as it creates a firewall pass rule. Or am I missing something?
Thanks in advance!
-
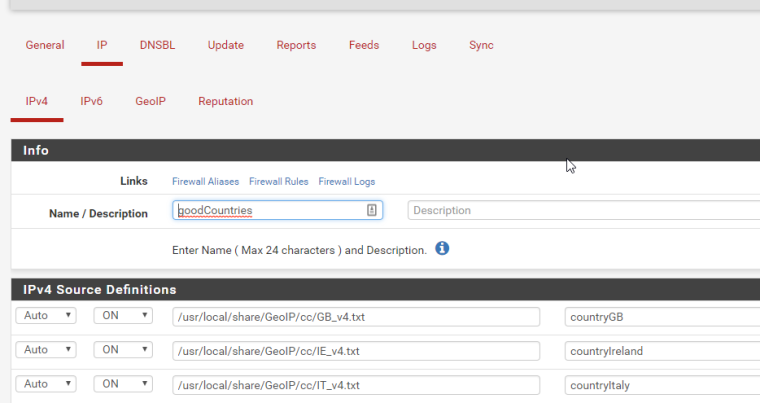
@stewart Yea, this is the way I do it. I create an alias in pfblocker and then make rules using it. Basically I say "if packet is not in goodcountries then block". This was the only way to do it a year or so ago and there might be new ways, but I haven't tried.
-
@bbrendon said in Best use of pfBlocker:
@stewart Yea, this is the way I do it. I create an alias in pfblocker and then make rules using it. Basically I say "if packet is not in goodcountries then block". This was the only way to do it a year or so ago and there might be new ways, but I haven't tried.
With pfBlockerNG-devel, you don't need to link the the GeoIP files anymore... it will still work, but you can now change the
Statefield to the newGeoIPoption :)You can also use Auto-Rules and configure the Advanced In/Outbound Rule options to configure more settings for the Firewall Rules.