OPENVPN SITE-TO-SITE Tunel does not connect
-
Good afternoon guys, I have the following scenario:
company A - LAN 192.168.0.0/24
company B - LAN 192.168.20.0/24
Tunnel OPENVPN 172.16.0.0/30
Port: 1194 released on Wan, and configured protocol release in openvpn rules.
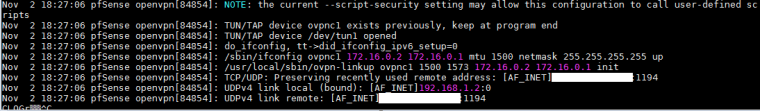
However, when trying to close the tunnel I am getting the following MSG in the log
company A OPENVPN server:
Server log:
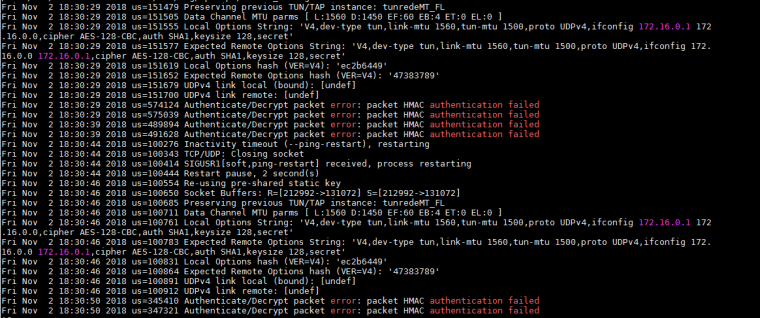
Client -
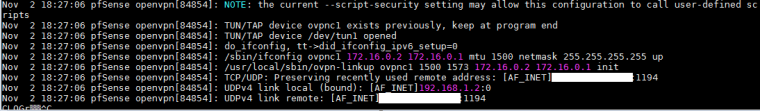
-
It looks like you have a tunnel subnet mismatch. The server seems to be expecting 172.16.0.0-172.16.0.1 andf the client 172.16.0.1-172.16.0.2. The client side seems correct. Hard to say quite how that might have been configured.
Are both sides set as p2p shared key?Both as subnet rather than net/30? (You can only choose subnet in p2p shared-key).
Can we see screenshots of the config on both sides?
Steve
-
A couple of things:
-
Give us the whole picture. It's evident that Company A's config is not from PFsense, so please provide more clarity on the two networks, what the edge devices are, etc
-
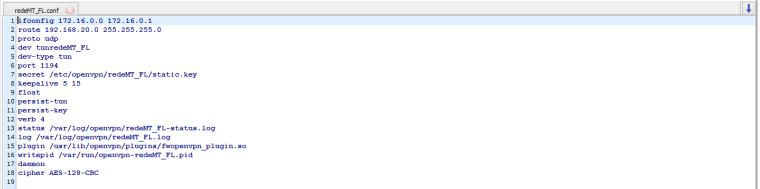
You've stated that Company A is the server, but it looks like the client to me. Post the config from Company B (server1.conf).
-
On Company A's config, the ifconfig line is wrong. 172.16.0.0 is a network address and shouldn't be in there. That line should read:
ifconfig {IP_of_Local_VPN_Endpoint} {IP_of_Remote_VPN_Endpoint} -
-
Good night, I thank you for the help comments, I was able to solve the problem, in fact as it is a pfsense implementation from scratch, I was using version 2.4.4 that caused an incompatibility with firewall A, so I went back to the version 2.3.5 and the problem was resolved.
-
Hmm, interesting. It should be backwards compatible. You should be able to get whatever is at firewall A to connect to 2.4.4 if it can connect to 2.3.5.
2.3.X is EoL now. There will no longer be security updates for it.Steve
-
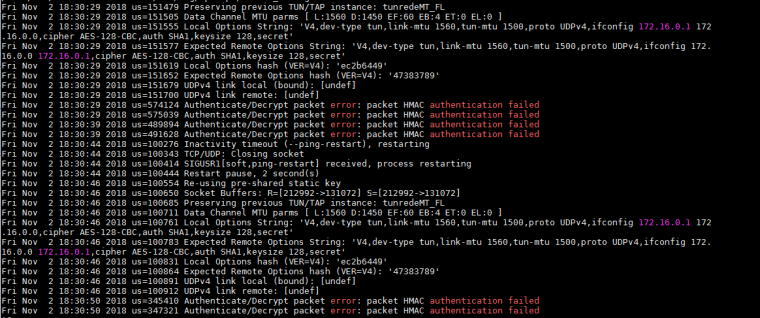
packet HMAC authentication failed is very often just down to wrong TLS Configuration or wrong key / key direction.
Going just back to some old Version like 2.3.5 is a very bad idea.-Rico