Snort Package Updates Available
-
Snort Package Updates
Updates for the Snort binary and GUI packages have been posted to the pfSense 2.4.5-DEVEL tree. These updates include version 2.9.12 of the Snort binary and a GUI package fix for Shared Object rule categories selections failing to save on the CATEGORIES tab.The new Snort package version is 3.2.9.8_3. This new package will also install the 2.9.12 version of the Snort binary. The new package is active in 2.4.5-DEVEL, and it should appear in the 2.4.4-RELEASE tree in the very near future.
-
Starting rules update... Time: 2018-11-06 15:07:03 Downloading Snort Subscriber rules md5 file snortrules-snapshot-29120.tar.gz.md5... Checking Snort Subscriber rules md5 file... There is a new set of Snort Subscriber rules posted. Downloading file 'snortrules-snapshot-29120.tar.gz'... Done downloading rules file. Downloading Emerging Threats Open rules md5 file emerging.rules.tar.gz.md5... Checking Emerging Threats Open rules md5 file... There is a new set of Emerging Threats Open rules posted. Downloading file 'emerging.rules.tar.gz'... Done downloading rules file. Extracting and installing Snort Subscriber Ruleset... Using Snort Subscriber precompiled SO rules for FreeBSD-11 ... Installation of Snort Subscriber rules completed. Extracting and installing Emerging Threats Open rules... Installation of Emerging Threats Open rules completed. Copying new config and map files... Updating rules configuration for: WAN ... Updating rules configuration for: LAN ... Updating rules configuration for: OPT2 ... The Rules update has finished. Time: 2018-11-06 15:08:22 -
I see the following messages in the log during the upgrade, is it okay to remove these files or should I just leave as is. I like to keep things tidy if possible but if it might break something I will leave it alone.
You may need to manually remove /usr/local/etc/snort/classification.config if it is no longer needed. You may need to manually remove /usr/local/etc/snort/gen-msg.map if it is no longer needed. You may need to manually remove /usr/local/etc/snort/preproc_rules/decoder.rules if it is no longer needed. You may need to manually remove /usr/local/etc/snort/preproc_rules/preprocessor.rules if it is no longer needed. You may need to manually remove /usr/local/etc/snort/preproc_rules/sensitive-data.rules if it is no longer needed. You may need to manually remove /usr/local/etc/snort/reference.config if it is no longer needed. You may need to manually remove /usr/local/etc/snort/snort.conf if it is no longer needed. You may need to manually remove /usr/local/etc/snort/threshold.conf if it is no longer needed. You may need to manually remove /usr/local/etc/snort/unicode.map if it is no longer needed. You may need to manually remove /usr/local/etc/snort/file_magic.conf if it is no longer needed. You may need to manually remove /usr/local/etc/snort/attribute_table.dtd if it is no longer needed. -
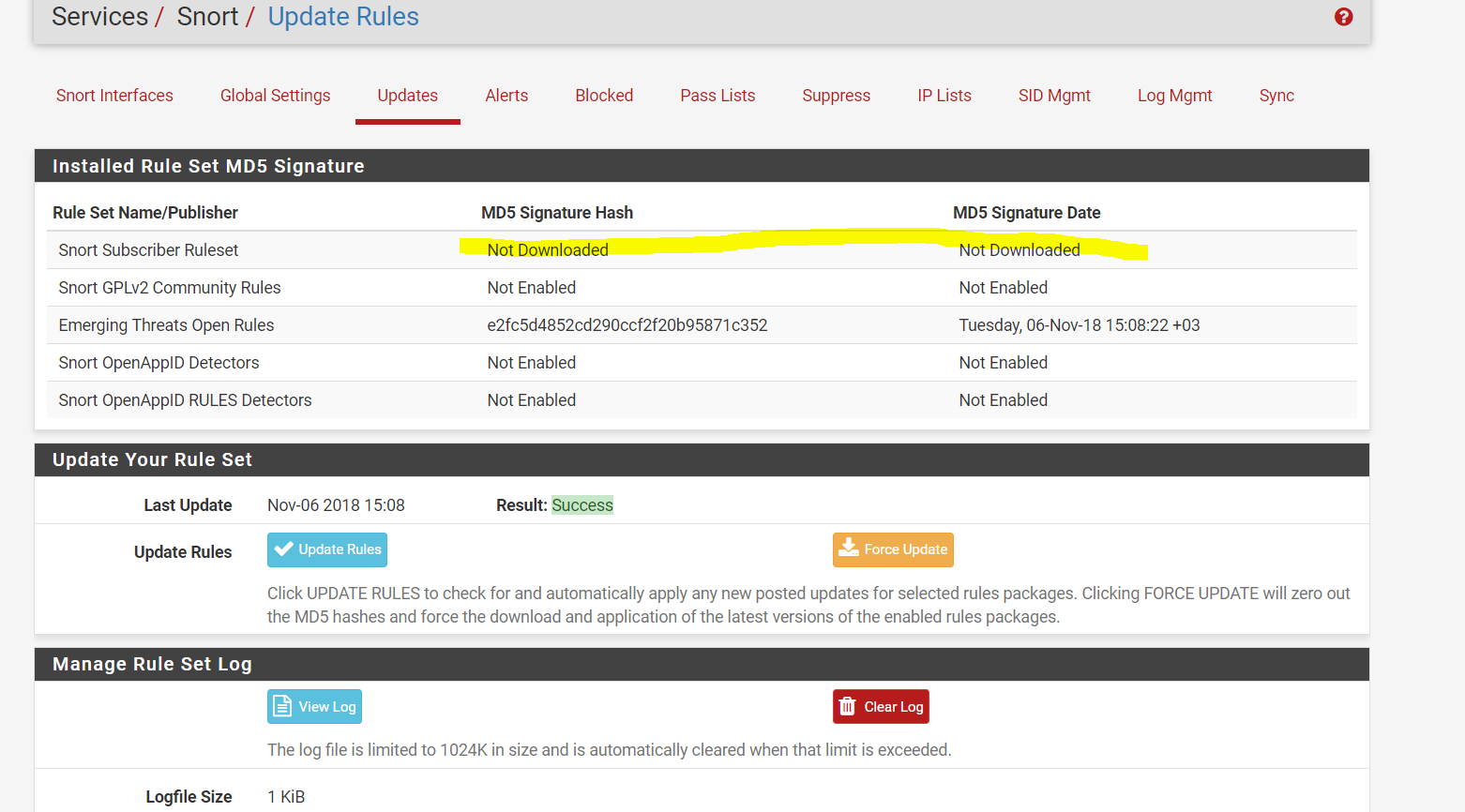
@turker did pfSense update the MD5 Signature Date field on the tab update? For me it states "Not Downloaded"
Starting rules update... Time: 2018-11-06 18:15:40 Downloading Snort Subscriber rules md5 file snortrules-snapshot-29120.tar.gz.md5... Checking Snort Subscriber rules md5 file... Snort Subscriber rules are up to date. Downloading Snort OpenAppID detectors md5 file snort-openappid.tar.gz.md5... Checking Snort OpenAppID detectors md5 file... There is a new set of Snort OpenAppID detectors posted. Downloading file 'snort-openappid.tar.gz'... Done downloading rules file. Downloading Snort OpenAppID RULES detectors md5 file appid_rules.tar.gz.md5... Checking Snort OpenAppID RULES detectors md5 file... There is a new set of Snort OpenAppID RULES detectors posted. Downloading file 'appid_rules.tar.gz'... Done downloading rules file. Downloading Snort GPLv2 Community Rules md5 file community-rules.tar.gz.md5... Checking Snort GPLv2 Community Rules md5 file... There is a new set of Snort GPLv2 Community Rules posted. Downloading file 'community-rules.tar.gz'... Done downloading rules file. Downloading Emerging Threats Open rules md5 file emerging.rules.tar.gz.md5... Checking Emerging Threats Open rules md5 file... There is a new set of Emerging Threats Open rules posted. Downloading file 'emerging.rules.tar.gz'... Done downloading rules file. Extracting and installing Snort OpenAppID detectors... Installation of Snort OpenAppID detectors completed. Extracting and installing Snort OpenAppID detectors... Installation of Snort OpenAppID detectors completed. Extracting and installing Snort GPLv2 Community Rules... Installation of Snort GPLv2 Community Rules completed. Extracting and installing Emerging Threats Open rules... Installation of Emerging Threats Open rules completed. Copying new config and map files... Updating rules configuration for: WAN ... Updating rules configuration for: LAN ... Updating rules configuration for: WLAN ... Restarting Snort to activate the new set of rules... Snort has restarted with your new set of rules. The Rules update has finished. Time: 2018-11-06 18:16:05Is this a bug? How can I check the rules are updated and in use ?
Futhermore it turned out snort was eating all the 8 GB of RAM. I just have stopped the service and removed the package.
-
The "Not Downloaded" text is a cosmetic error. The upstream Snort team changed the way the rules archive file is named with this latest version, and that change throws off some of the automatic stuff in the GUI package. I fixed two issues, but apparently missed this one. You can be confident the new file versions are downloaded and in use by looking at the Update Log file (you posted its contents). See how it says in there the 29120 file was downloaded and installed?
-
@bmeeks said in Snort Package Updates Available:
The "Not Downloaded" text is a cosmetic error. The upstream Snort team changed the way the rules archive file is named with this latest version, and that change throws off some of the automatic stuff in the GUI package. I fixed two issues, but apparently missed this one. You can be confident the new file versions are downloaded and in use by looking at the Update Log file (you posted its contents). See how it says in there the 29120 file was downloaded and installed?
And what about the RAM eating of snort any experience?
-
@nagel
I have no idea about the RAM usage increase. I've noticed no change on my own firewall running Snort. -
I don't see any block from Snort rules, only from ET.
-
@simbad said in Snort Package Updates Available:
I don't see any block from Snort rules, only from ET.
Depending on which rules you have enabled, that can be perfectly normal. I'm a safe browser, so I see pretty much no alerts from anything except the handful of known malicious IP lists I run from the ET feed. I run those on my WAN just to generate some alerts to look at. The traffic from those IP addresses is blocked by my default WAN rules anyway. With a properly tuned rule set, you should expect to see very few alerts unless you have an actual security problem inside your perimeter.
-
For those of you seeing the "Not Downloaded" message on the UPDATES tab for the Snort Subscriber Rules, that is only a cosmetic problem. I will submit a fix for it, but in the meantime if you want to correct the issue yourself you can make the following edit to the listed file.
File: /usr/local/www/snort/snort_download_updates.php
Open that file in an editor (you can use the DIAGNOSTICS -> EDIT function of pfSense).
Locate this area of code near the top of the file:/* Define some locally required variables from Snort constants */ $snortdir = SNORTDIR; $snortbinver = SNORT_BIN_VERSION; $snortbinver = str_replace(".", "", $snortbinver);Paste the following code immediately underneath it.
// Make sure the rules version is at least 5 characters in length // by adding trailing zeros if required. if (strlen($snortbinver) < 5) { $snortbinver = str_pad($snortbinver, 5, '0', STR_PAD_RIGHT); }Save the change and that's it. Here is how the fixed code should look after you finish:
/* Define some locally required variables from Snort constants */ $snortdir = SNORTDIR; $snortbinver = SNORT_BIN_VERSION; $snortbinver = str_replace(".", "", $snortbinver); // Make sure the rules version is at least 5 characters in length // by adding trailing zeros if required. if (strlen($snortbinver) < 5) { $snortbinver = str_pad($snortbinver, 5, '0', STR_PAD_RIGHT); }Update: a pull request containing this fix has been posted for the pfSense team to review and merge. The request can be viewed here.
-
Fixed with update. Thanks
-
@bmeeks said in Snort Package Updates Available:
@nagel
I have no idea about the RAM usage increase. I've noticed no change on my own firewall running Snort.Back to normal. Changed the version and the matching to "AC" without -"BNFA"
-
@nagel said in Snort Package Updates Available:
@bmeeks said in Snort Package Updates Available:
@nagel
I have no idea about the RAM usage increase. I've noticed no change on my own firewall running Snort.Back to normal. Changed the version and the matching to "AC" without -"BNFA"
So do you mean that after the version change you altered the Fast Pattern Matching algorithm to "AC"? If so, that would definitely have been the problem. I really should take out all of the other options as nothing works better than "AC-BNFA" for the Pattern Matcher. All of the other settings just eat up RAM like crazy for essentially zero performance benefit.
-
Working nice here, the alerts i see is from wan side as i use SCAN and DROP rules from ET.
I did a week or 2 get from LAN side though but i am not sure if it was because of microsoft store or it was malware on that computer.
I did run antispyware and it found trackers not actually malware.
Anyway i hope snort will soon or in 2019/20 support/run on all cores.
This alpha stage has been going on for ages.