Setting up Suricata on pfSense in Virtual Machine -> Custom Rule Problem
-
Hello dear community,
Im doing a project work at the university and need to implement an IDS in a small network. I stuck at implementing custom rules and don't get any further with the informations I find on the internet. I hope to find some help here :-)
At the moment I just want to get used to work with suricata and set up some Virtual Machines in Virtualbox. My problem is, that I dont get alerts for "simple" rules.
First VM: pfSense (2.4.4) running suricata -> WebConfigurator, Rule sets (ET open/Snort) have been downloaded, so it seems to work fine so far.
Second VM: Ubuntu (18.10) running nothing special, i want to use it to generate some network traffic to check if suricata is working
The two VMs are connected via "Internal Network" in Virtualbox
The pfSense VM has an additional NAT and Host-only for the WebConfigurator
The Host-System runs Windows 10.I tried two different protocols as follows:
alert tcp any any -> any any (msg:"TCP-Test"; classtype:web-application-attack)
and same wit ICMP instead of TCP.
I used the ping from Ubuntu VM to pfSense VM with the rule for ICMP set in the "Custom rules" in the WebConfigurator. The ping worked fine but no alert showed up in the WebConfigurator.
Same thing, when I used telnet to open a TCP connection.I allowed all TCP/ICMP connections in the firewall.
Im running out of ideas. Im totally new to IDS and haven't much experience with networks in general either, but really want to figure out, where the problem is.
Maybe I've got a wrong syntax or similar in my rule? Or need to enable the custom rules to alert? Also some standard rules are enabled in suricata but it does not seem to me like there is a rule, which somehow "disables" my custom rule, all ET open /Snort packages are disabled.
Sorry if Im missing any information. Tell me if it helps to know anything more
Thanks in advance,
Finchen -
pfSense is a router/firewall. Suricata running on the firewall can only alert on traffic it actually sees. Do you have Suricata on the pfSense box running on the WAN or LAN interface? For your setup, it should be set up and running on the LAN if I understand your setup correctly.
The first troubleshooting step you should take is to use the packet capture command in pfSense to be sure your traffic is entering the interface where Suricata is actually running.
-
Thanks bmeeks for your answer :-)
I didn't know the packet capture function yet. It works fine. I can see both the ICMP and the TCP packages. The Interface is a LAN, thats correct, running DHCP (because i plan to add more VMs to this virtual network, once it works).
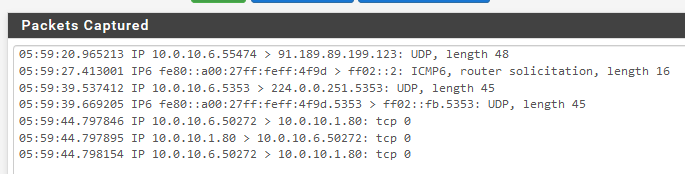
In my alerts I find this: The IPv6 rule is one of the default rules of suricata if i got that right (Im not sure why it is sent, because only IPv4 should be enabled, but maybe its part of the "telnet" tcp command?). My custom rule is not listed.
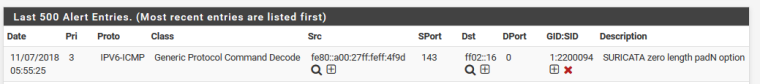
For me, it means that I got some mistake in my custom rules. Can I check anything to see if the rules are actually applied? Or maybe I got some mistakes in the syntax.
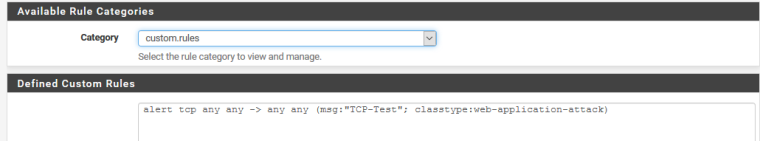
That is how it looks like at the moment.
Thank you very much! :-)
Finchen -
Sorry I did not catch this mistake earlier, but your rule contains no SID or GID (Signature ID and Generator ID). Every rule must have a GID:SID identifier pair, and the SID must be unique. No two rules can have the same SID. For Suricata the GID is always "1", but the SID must be a unique number. To be sure you don't conflict with the SIDs from vendor-packaged rule sets, most folks use SID values starting at 2000000 and work up from there for their custom rules.
Go read up on Suricata rule syntax here.
-
Thank you for you help!
I managed the rule to work, when I use a real physical network with an APU-Board and my Laptop.
In my virtual Network I didn't managed to get the alerts but now i know, that my syntax is correct.This worked for me:
alert icmp any any -> any any (msg:"ICMP-Test"; classtype:trojan-activity; sid:1000500; rev:1;)if I can manage, that this works in my Virtualbox too, I will post the solution. :-)
-
It seems, there was just some mistakes in my syntax, now it works on my VM too.
I missed the rev-number and the ";" at the end of the rule.