Vlans No Switch?
-
@jknott looool

Not , really not ideal hardware ;) , you are in truth,
I notice some packets errors under statistic tab, when this bad switch configured only one vlan trunk
Is nice for me, to figure it out why happen this, because it's working fine with few clients talking, and when many clients talking I get network problem.
For sure this kind of hardware is no good for business, SG105E kidding me! : -
@babiz cable costs I have allready put alot of $ into cables and it would be hundreds of feet of wireing my entire property ... and I need to isolate my security systems 3 separate systems then I got smart wifi power switches then I got endless number of computer's and devices that I want to secure ..Just saw that multiple openvpn instances would cost performance so that ideas gone
-
@johnpoz using a single linksys 6350 or something like that in bridge mode and if i need more ports i put another netgear 6300 in wireless access point mode
-
well i want to order a switch which one is capable of vlans alot of the ones i see dont say 802.1q Best buy office depot most likely choices for finding them
-
You want something that says Managed, Smart, WebSmart, etc. The specifications should definitely list 802.1q.
I will never again buy anything that requires some form of client application to configure. Needs to have a web interface.
I like the D-Link DGS-1100-08 for a cheap switch.
-
@telescopedepth said in Vlans No Switch?:
linksys 6350
Is it running something like openwrt or dd-wrt.. I find it highly unlikely that its native firmware has a clue to doing any sort of vlans other than when you create a guest network and it routes.. Its not going to to tag your ssid traffic with the correct vlan, nor does it allow for vlan support on any of its switch ports.
Get switch that does vlans, get an AP that does them... Its that simple and you wont be scratching your head on why this doesn't work, etc.
It says that is $60 on the linksys site... I see the uap-ac-lite for 70 over on newegg. That is a NO Brainer choice!! That dgs-1100-08 that derelict mentions is a good starter vlan switch.. Show it for $35 over at amazon currently
-
Thanks everyone I really appreciate it
-
@johnpoz DDWRT linkys router but I'm just going to try to buy new ap and switch so I can get on with my life
-
@johnpoz I make your saying a reality got my switch and locked myself out of it going to try to find a way in but I'm probably sending it back dlink suggest Ed I do
-
huh? Can you not just factory reset it... How you could have locked yourself out?
"Reset: By pressing the Reset button for 5 seconds the Switch will change back to the default configuration
and all changes will be lost."You got the dgs-1100-08?
-
Yes that is the model i did reset it unfortunately for me i read the instructions manual it didnt say how to reset it so i did a 30-30-30 reset and the only thing i could get it to do after that is upload the firmware unfortunately for me my network isnt allowing me to find the address to download the factory firmware somethings messed up somewhere I have tried the my cellphone network too nothing goes through so i dont know im just sending it back order the same one again...
-
@derelict Would you walk me through just a basic Pfsense and The DGS-1100-08 switch you recommended with a vlan for each port setup and if you just tell me How to do it once i can probably figure out the rest Maybe...Please if not i might not ruin this switch like the last one :)
-
Umm. Not without knowing what you want to do.
-
@derelict well Basically just segregate each port into different vlans besides the two seperate vlans that are for roku and security systems i have multiple roku tv computers etc i bought two of those switchs i have em0 as wan Re0 and Re1 as lan side stuff so i was hopeing hook one switch to the Re0 and one to the Re1 I need a security system vlan with 4 ports all on same vlan i was hopeing if i put a router on that it would work to access my security systems even that would make my life easy... and setup another wireless router and roku tv vlan with 3 ports for that and that seperates my stuff if all other ports are segregated from each other and maybe once i see how thats done i can figure out whats what thanks
-
I'm under testing some kind of vlans configuration for watching if all work good or not work good.
Setup vlans itself is pretty simple, I need to test a lot of vlans subnet , and pfSense almost will manage without issue.

On pic above you can notice at one shot all my vlans testing environment, so you can see;interface tag number,
subnet and mask in cdir notation,
(Indeed I'm done with all other basic interface setting, DNS and DHCP enabled, one basic rule "interface to all" for each vlans)
This is a side note. If some folks not understand enough all background of pfSense
So, last one CDIR netmask is different for each subnet, I will to try, for testing purposes.
I need to known if will be reliable to generate some more much traffich at once and with different netmask. and switch tagging/untagging and last wireless multi ssid access point
For go foward now with vlans setup after this , before you leave from pfsense webui make sure to do everything is needed you need and rebott it

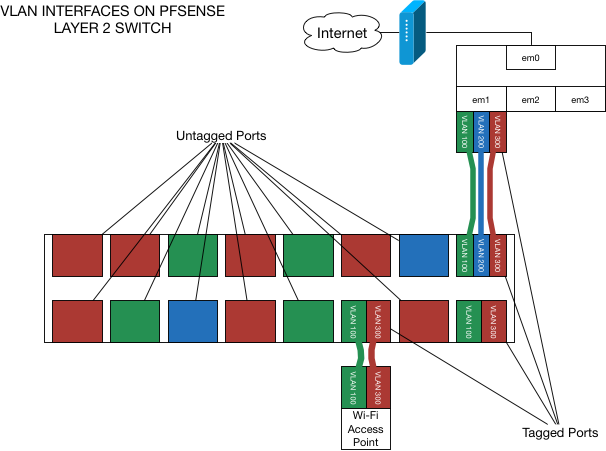
Next to assign tagged and untagged port on your switch*
well, my layout on crappy tl-sg105e as follow:

At this stage you can look a nice layout on the paper, I made this with my network teacher in mind, when he said something like "is better do a full vlans configuration on your device, for avoiding issues"
LOOL, just start with small "seven" tag configuration, this is enough for checking some vlans behaviors.
** My pfSense is connected at port 1 and my wlan ap is plugged at port 2 , other ports go to other devices and I will test later.**
I'm notice no many problem between devices, but because my crappy switch I guess some kind of "overlaps" and missing to get internet access when I'm under testing this only trought my multi ssid wlan ap.
Because this I back to only two ssid broadcasting instead of four available, with more to two ssid my wlan ap give up
I'm pretty sure of this, so next pic show my current multi ssid configuration:

So my test trials is not really done, but I like to show how to is pretty simple, dealing with vlans and pfSense!
Indeed routing trought all this subnet works well like a charm.
Bye
-
If that TP-Link AP behaves the same as my WA-901N, I can guarantee it won't handle VLANs properly.
-
That sg105e doesnt allow you to remove vlan 1.. So your whole attempt at trying to do vlans is moot.. You can not actually do valns with such switch..
If its v3 hardware you should be able to update so you can remove vlan 1 form your interfaces your wanting to put in other vlans.
Yeah their AP are the same lack of understanding design..
-
@johnpoz said in Vlans No Switch?:
Yeah their AP are the same lack of understanding design..
Same with their support staff. When I contacted them, they couldn't understand that VLANs should act as logically separate LANs, with no traffic passing between them. When I was able to reach 2nd level support, they accepted there was a problem, but no fix was forthcoming.
-
@johnpoz Using the Dgs-1100-08 is there a way to make vlans work with pfsense I spent all day messing with stuff I had it easier using ddwrt
-
Of course there is, but you have to understand what you are doing with VLANs in the first place.
In general:
If you assign a pfSense interface (Interfaces > Assignments) to:
igb0 - it will be on the untagged, native VLAN on the switchport it is connected to.
If you create VLAN 10 on igb0 and assign an interface to:
VLAN 10 on igb0 (igb0.10) it will be excpecting the switchport it is connected to to be tagging VLAN 10.