how to improve openvpn performance/ Am I doing this right way
-
Hello
I want to access my local lan from outside. But I have no real ip at WAN. So i buy cheap oepnvz vps and install openvpn server there. I configure pfsense as vpn client. Now I try to reach home lan via vps ip.
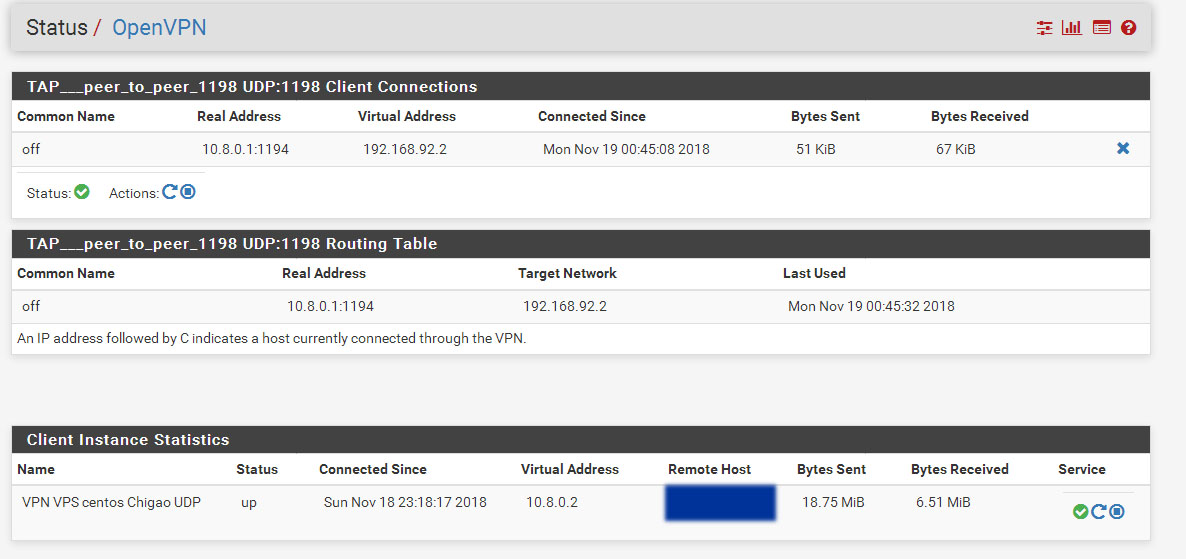
I can ping 192.168.1.100. When I try log on server (a) I was hangup at middle point or console did not fully load.
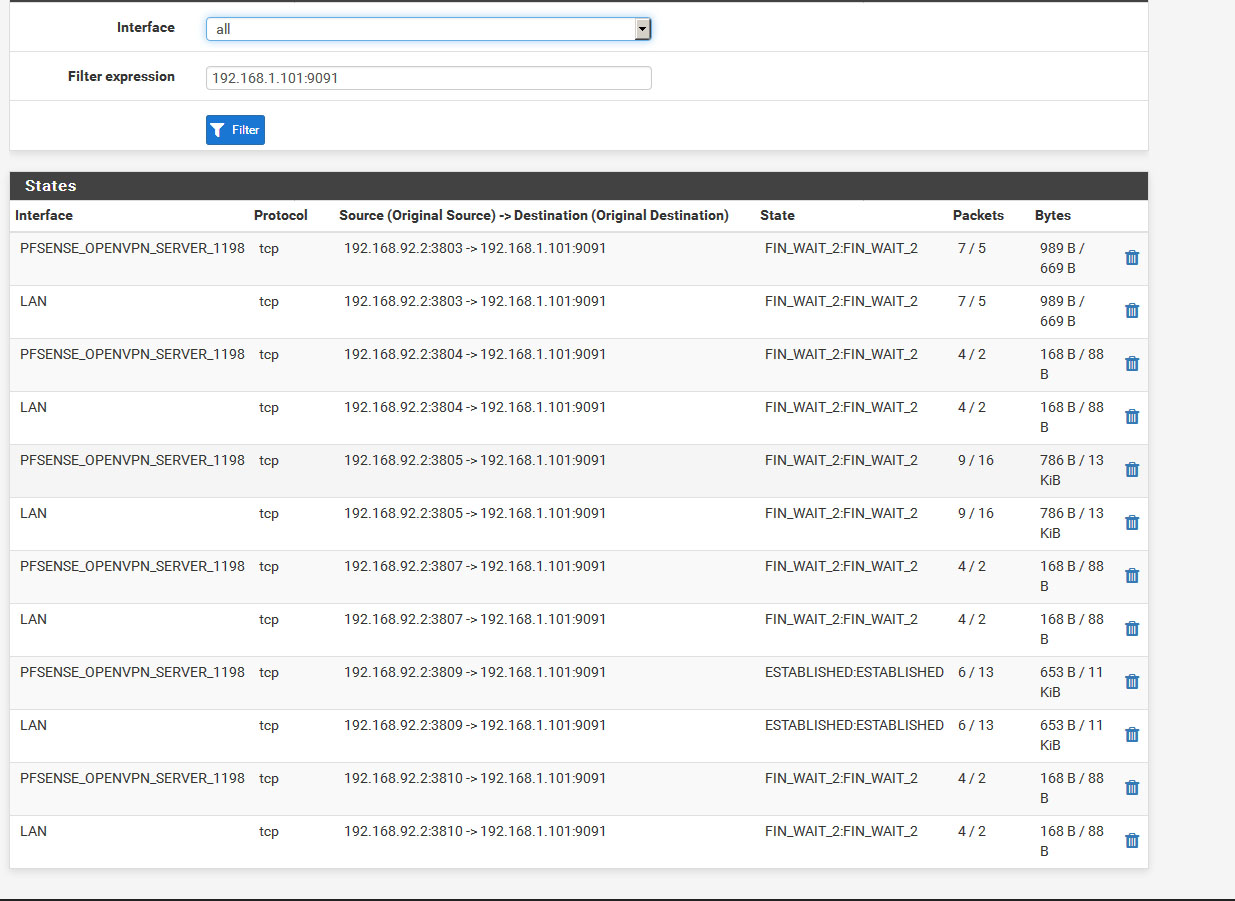
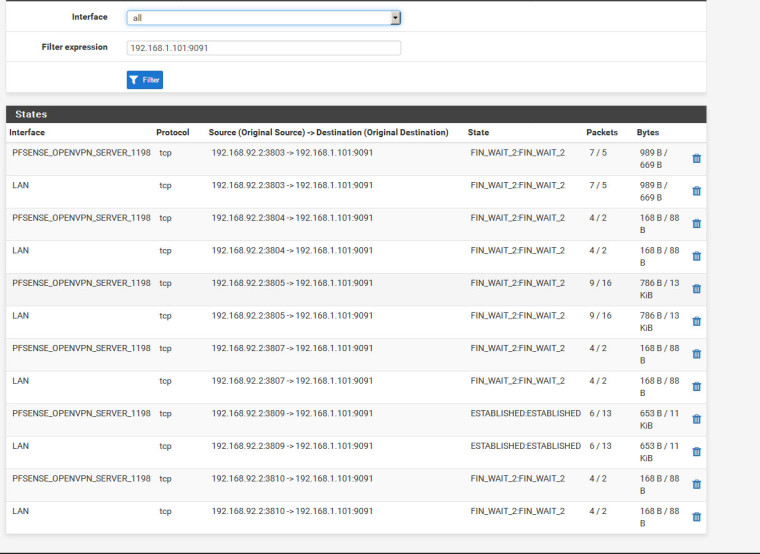
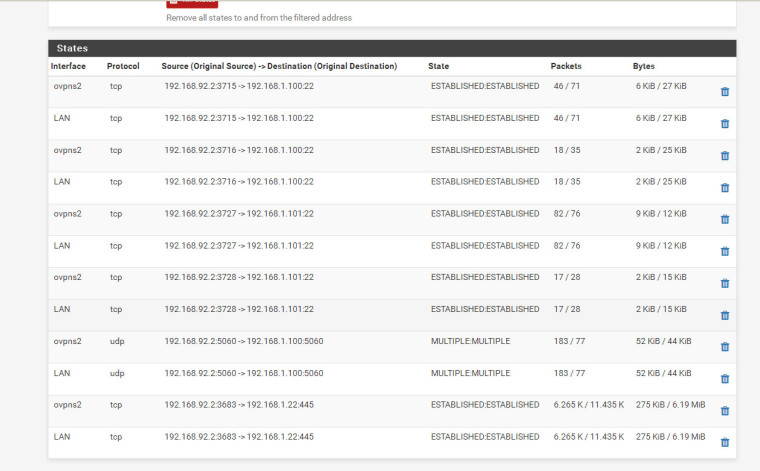
I can access ss server (b) but webpage show FIN_WAIT_2:FIN_WAIT_2 and getting very low speed when try to browse windows share (c).
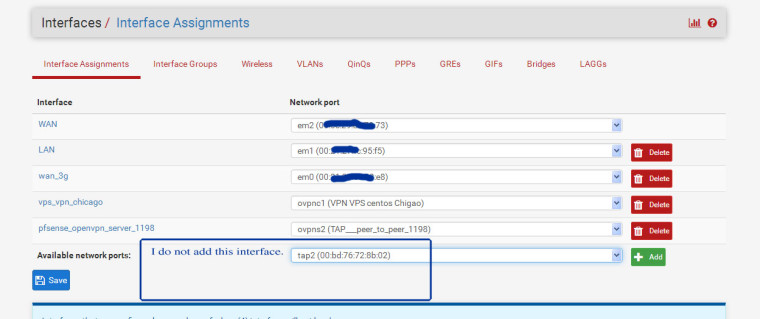
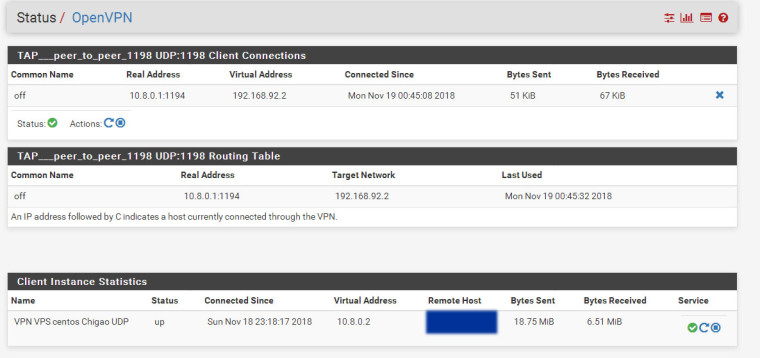
There are a unknown interface (tap2). I do not understand where does it come from.Lan Subnet : 192.168.1.0/24 Wan : 192.168.25.40 cent os vpn server subnet : 10.8.0.0/24 Pfsense vpn client : 10.8.0.2 Target ssh/asterisk server (a) : 192.168.1.100 ssh server (b) : 192.168.1.101 Windows share folder (c) : 192.168.1.22------ Centos 6.9 (vps server) ----------- Iptables rules for port forward iptables -t nat -A PREROUTING -j LOG --log-prefix "PREROUTING:" --log-level 6 iptables -t nat -I PREROUTING -d "VPS Real IP" -p tcp --dport 1196:65535 -j DNAT --to-destination 10.8.0.2:1196-65535 iptables -t nat -A PREROUTING -d "VPS Real IP" -p udp -m udp --dport 1196:65535 -j DNAT --to-destination 10.8.0.2:1196-65535 iptables -t nat -A POSTROUTING -j LOG --log-prefix "MASQUERADE:" --log-level 6 iptables -t nat -I POSTROUTING -d 10.8.0.2 -p tcp --dport 1196:65535 -j SNAT --to-source 10.8.0.1 iptables -t nat -I POSTROUTING -d 10.8.0.2 -p udp --dport 1196:65535 -j SNAT --to-source 10.8.0.1 iptables -A FORWARD -j LOG --log-prefix "FORWARD:" --log-level 6 iptables -I FORWARD 1 -d 10.8.0.2 -p tcp --dport 1196:65535 -j ACCEPT ------------- Openvpn Server Conf (From centos VPS) port 1194 proto udp dev tun user nobody group nobody persist-key persist-tun keepalive 10 120 topology subnet server 10.8.0.0 255.255.255.0 client-to-client push "route 192.168.1.0 255.255.255.0" ifconfig-pool-persist ipp.txt push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4" push "redirect-gateway def1 bypass-dhcp" crl-verify crl.pem ca ca.crt cert server_g9hq31FXVL3AsXq0.crt key server_g9hq31FXVL3AsXq0.key tls-auth tls-auth.key 0 dh dh.pem auth SHA256 cipher AES-128-CBC tls-server tls-version-min 1.2 tls-cipher TLS-DHE-RSA-WITH-AES-128-GCM-SHA256 status openvpn.log verb 3Pfsense Openvpn server dev ovpns2 dev-type tun tun-ipv6 dev-node /dev/tun2 writepid /var/run/openvpn_server2.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp cipher AES-256-CBC auth SHA512 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 10.8.0.2 tls-server server 192.168.92.0 255.255.255.0 client-config-dir /var/etc/openvpn-csc/server2 username-as-common-name auth-user-pass-verify "/usr/local/sbin/ovpn_auth_verify user TG9jYWwgRGF0YWJhc2U= false server2 1198" via-env tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'pfsense_openvpn_server_Certificate_1198' 1" lport 1198 management /var/etc/openvpn/server2.sock unix push "route 192.168.1.0 255.255.255.0" push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4" client-to-client ca /var/etc/openvpn/server2.ca cert /var/etc/openvpn/server2.cert key /var/etc/openvpn/server2.key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server2.tls-auth 0 comp-lzo adaptive passtos persist-remote-ip float topology subnet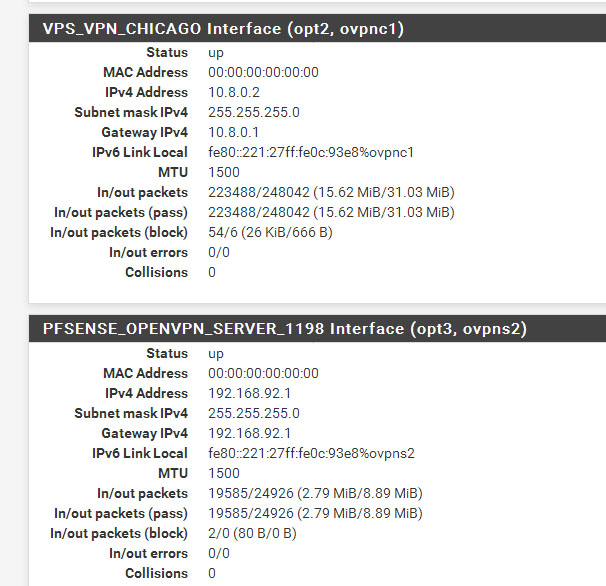
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.