ath0_wlan0 Clients Get DHCP, but can't do anything more
-
Despite having a WiFi card installed directly in my APU is not a recommended configuration, it is listed as "supported," so I want to get this working, if only to understand how it works.
I have the wireless interface added (no IPv4 or IPv6 configuration), configured in Access Mode, and bridged to the LAN port, and I have a Firewall rule for WiFi set up to pass all TCPv4 traffic.
WiFi clients receive an IP address, but that's it. They can't get out to the internet, and they can't even get to the management interface on the LAN port's IP address.
Am I missing a step? Thanks!
-
This post is deleted! -
Hi, for my modest opinion, first of all you can get to "standard" configuration, for "testing" purpose.
So, you need to un-bridge ath0_wlan0 interface,
For configure "correctly" ath0_wlan0, follow usuals steps below:
.1 Go trough assignment of new interface "ath0_wlan0" with usual OPTx interfce name.
.2 Go to OPTx interface tab and setup it with proper static IP address fitting subnet you want like (ex. 192.168.x.0/24)
.3 Configure dhcp server propely for this new subnet
.4 Starting with basic rule "any to any" with default gateway "*" assigned, to new OPTx interface name appear on Firewall/Rules tab.Apply all configuration and you are done.
If you additional go to Advanced / Nat Firewall ,and for enable Auto Generating rules of some kind, please check your current Auto rules configuration for allowing "talking" between lan and opt subnets, it's for "proper" easy working!
Finally optional you can better restart pfsense
That's is very easy way for get wlan interface to work! :D
Goodbye. -
Thanks! I tried this, but I still can't get it to work as I expect:
- LAN is set up as 192.168.4.1/24
- WiFi is set up as 192.168.5.1/24
- DHCP server is active on both LAN and WAN, on their respective subnets.
- Firewall rules are set up to pass all WiFi/TCPv4 traffic.
WiFi clients still can't get out to the internet. Do I need to set up a route for the .5 network?
Questions:
- I tried setting up the WiFi interface as 192.168.2.1/24, but pfsense wouldn't let me. Why not?
- Other pages have suggested setting up LAN and WiFi as a bridge, and then assigning that bridge the 192.168.4.1. address. But they warn against locking out the management interface at 192.168.4.1. If I experiment with this, how can I recover if I lock myself out?
I just want this box to behave like a typical WiFi router, e.g. serve WiFi clients just as if they were connected via Ethernet.
Is there a guide for this type of typical setup? The pfsense "how-to" page just describes setup of the physical interface, not of the routing.
-
@thewaterbug Hello my friend.
Yes , absolutley ! pfSense with defaults setting loaded and with every single interfaces configured with correct settings, is able to do auto routing and easy internet access.nitial configuration trought a finished job and "standard router feature" accomplished.
This is just a few minutes of work (if you can start from defaults, no need to make additional configuration,)
Simply add WAN interface (PPPoE or DHCP usually)
Second configure your LAN IP subnet (192.168.x.0/24) and dhcp, allowing to manage others interfaces trought web ui.
Thrid step, add your ath0_wlan0 wireless and assign as OPTx interface IP settings, (192.168.y.0/24) please pay attention, you cannot allowed to assign same subnet on all lan/wlan interface, and please make sure to set one different subnet.Standard configuration for lans and wlans interface , well I mean assign STATIC IP under interfaces tab and enabling dhcp pool as well (other settings like gateway and dns ip server is no required for proper initial dhcp configuration, only setup pool address range-
Fourth step is checking default LAN rule "Allow any to any", and copy it , of course with change its interface name from LAN to OPTx and other related entry like "LAN net"to "OPTx net".
Apply all and recheck your Wireless settings on OPT tab for configure as HostAP mode and so on....
Is very easy to do this for me, but I'm sorry if I'm not explained this very clear. I do my best, cheers. -
I went back to my original configuration, e.g. with the WiFi unconfigured for TCPv4 and bridged to the LAN interface, for some additional testing:
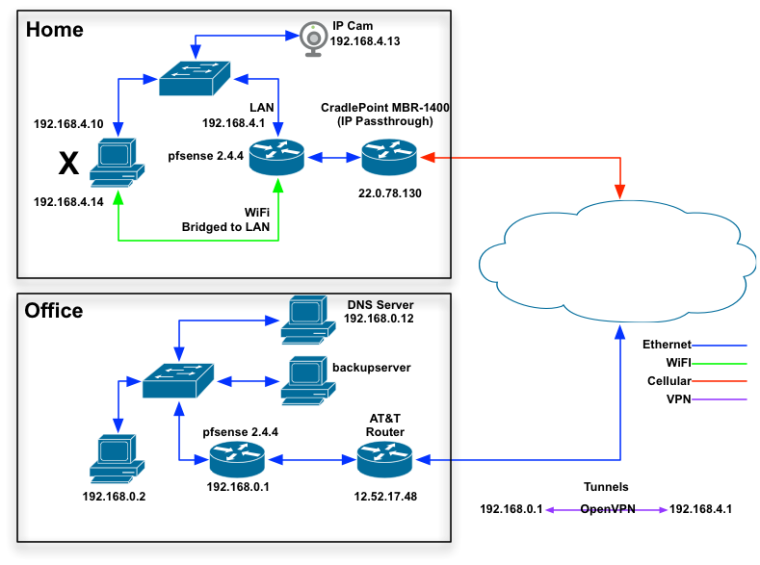
- My pfsense box at 192.168.4.1/24 is set up with an OpenVPN tunnel to another pfsense box at 192.168.0.1/24.
- There is a DNS server at 192.168.0.12
- There are servers on the far side of the tunnel, e.g. at http://backupserver/connect/
- The WiFi client on this side of this pfsense box receives a DHCP address of 192.168.4.14, with the DNS server of 192.168.0.12.
- When connected only by WiFi (e.g. if that Ethernet cable is disconnected) that WiFi client cannot connect to devices out on the internet, e.g. www.yahoo.com.
- That Wifi client can connect to http://backupserver/connect/.
- Therefore I believe DNS is not the problem, as otherwise my WiFi client would not be able to load a web page at http://backupserver/connect/.
- That Wifi client can connect to 192.168.0.1.
- That Wifi client cannot connect to the pfsense box's management interface at 192.168.4.1.
- But if I RDP from that Wifi client into the box at 192.168.0.2 (on the other side of the OpenVPN tunnel) a browser running on 192.168.0.2 can connect to the pfsense box's management interface at 192.168.4.1. Therefore that management interface is up and working.
- That Wifi client cannot connect to the IP camera at 192.168.4.13.
- The box at 192.168.0.2 can connect to the IP camera at 193.168.4.13.
- I do not see any Firewall Log entries of anything being denied from 192.168.4.14 address when the WiFi client at 192.168.4.14 attempts to connect to 192.168.4.1, to 192.168.4.13, or to www.yahoo.com
- If I turn off WiFi and connect from the PC to the pfsense box at 192.168.4.1 by Ethernet, I get an IP of 192.168.4.10, with a DNS server of 192.168.0.12, and everything works as I expect.
Firewall rules are set up as follows:
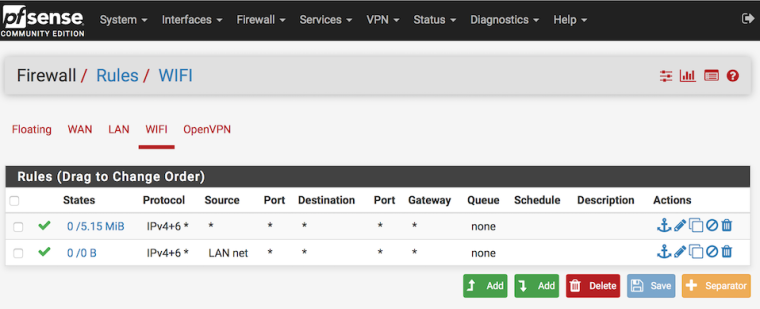
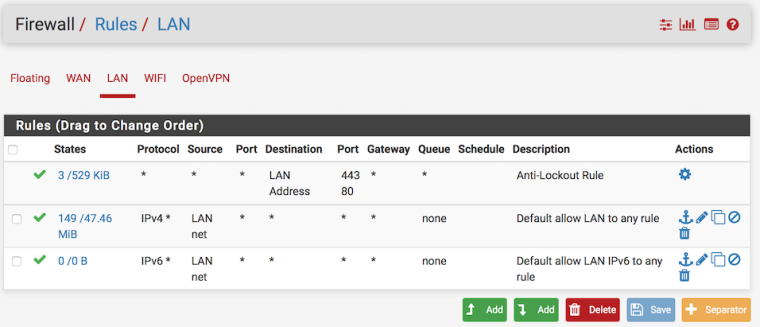
What have I done incorrectly?
-
I just fixed this. I followed these instructions:
https://www.cyberciti.biz/faq/howto-configure-wireless-bridge-access-point-in-pfsense/
which instruct me to assign the IP address to the BRIDGE0 interface instead of to the LAN interface, and now everything works as expected.
-
^^
But it doesn't survive a reboot of the firewall.
If I follow those instructions, everything works as expected. I can disconnect my client from Ethernet and connect to the WiFi on the pfense box, and everything works. But if I reboot the firewall, then everything stops working again.
-
Test. Is this thread locked?
-
Damn, now it's work!
So well, just in short, I write two thing about.
Thankfully your nice layout diagram I understand more better your scenario.First thing I notice is about firewall rules on WIFI, but and LAN as well, something is wrong.
Step one , if you dont'use IPV6 you may will to blocking/disabling this protocol trought System / Advanced / Networking

Or if you will use IPV6 protocol, please take apart for now and disabing the rules related. Or atleast do the same logic trought interfaces, (ex. if in your lan here ipv4 and ipv6 is detached , why you make ipv4+ipv6 in one at WIFI? this is not consistent according to me)
Step two , You know after restoring pfSense default's rule "Allow LAN to any" under LAN tab, well you need to respect same logic as LAN to WIFI
and set it according, you need to changhe LAn net to WIFI net for this job, and delete your top rule at WIFI "any to any" because this overlaps the right rule below. (right rule if you change it as described above)
for example look my rule below:

Well after this, now hottest topic, your configuration needs ovpn review according to me.
For avoid some kind of your last problem i advice you to forget bridging at all and set interfaces properly with respective subnet address , dhcp server pool and add "other" routing path under ovpn tunnel configuration, this last done by editing your current tunnel or add new one.
After this I'm absolutley sure you can go trought on internet-
At this stage maybe you miss routing instruction, and bridges will fail under some kind of special scenario like yours.Because is better live within standard configuration if knowdledge isn't enough.
Unfortunatley I "hate" ovpn's at all :D hehe it's more complex and full of mistery for me, and my defaults in mind is ipsec based protocol, allow me all kind of routing I need between interfaces / wan / interfaces and work easy with easy setup, so if you can do, better forgive ovpn and setup ipsec.
If you love ovpn's stuffs so go to learn more about and find your way.