Pfsense block ICMP echo reply from WAN to OPT1
-
First, you might want to put your router in bridge mode - hand off your public IP to your pfsense WAN interface. Second, try running packet capture on the WAN interface. It could be your ISP router blocking ICMP echo replies. Running it that way I think you are, you will have double NAT.
-
@tmedtcom said in Pfsense block ICMP echo reply from WAN to OPT1:
11:12:06.795326 IP 172.16.0.12 > 172.16.0.1: ICMP echo request, id 3097, seq 1922, length 8
You list pfsense wan as .11, why is your sniff showing from .12
Did you setup a vip on your wan? Did you mess with outbound nat?
-
Yes Normally I have a double Nat, since I have a Cisco router that is NAT and has a single public IP WAN then I have in my VMWARE ESXI the PfSense which is NAT too.
Does double nat not work?
A solution? -
double nat will work just fine.. Not optimal choice - but works for pretty much everything.. But again you state pfsense wan is .11 and your sniff of pings shows source of .12
-
Double NAT works, unless of course it doesn't... I was just pointing that out in case you weren't aware. Have you checked the Cisco router if it's blocking the reply? Try pinging the WAN interface of the Cisco device.
-
LAN interface 172.16.0.11
WAN interface 172.16.0.12
OPT1 interface 192.168.10.1
Virtual machine connected to pfsense have Ip address 192.168.10.99
The PFSENSE graphical interface accessible from the LAN ip 172.16.0.11
Also I ping from the pfsense to 8.8.8.8 it passes well through the CISCO router
-
So pfSense can ping 8.8.8.8 but not your device at 192.168.10.99? I'm assuming you have no other connectivity issue from this device - you can browse and stuff? Is there a firewall service running in this VM?
-
Ping from INTERNAL (OPT1) to 8.8.8.8:
The result:
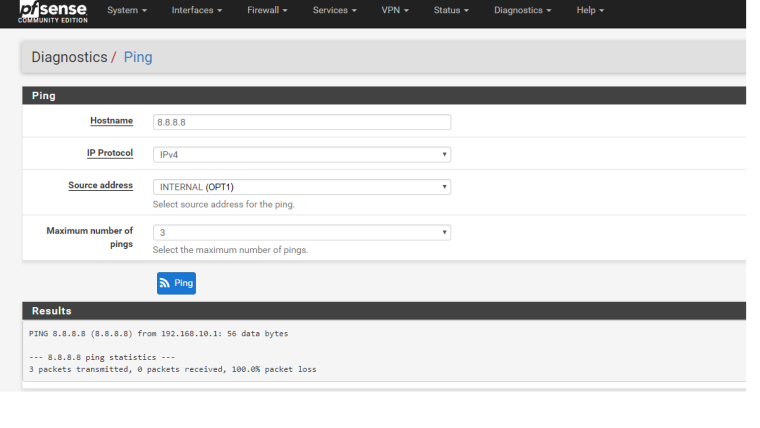
Ping from WAN to 8.8.8.8:
The result:
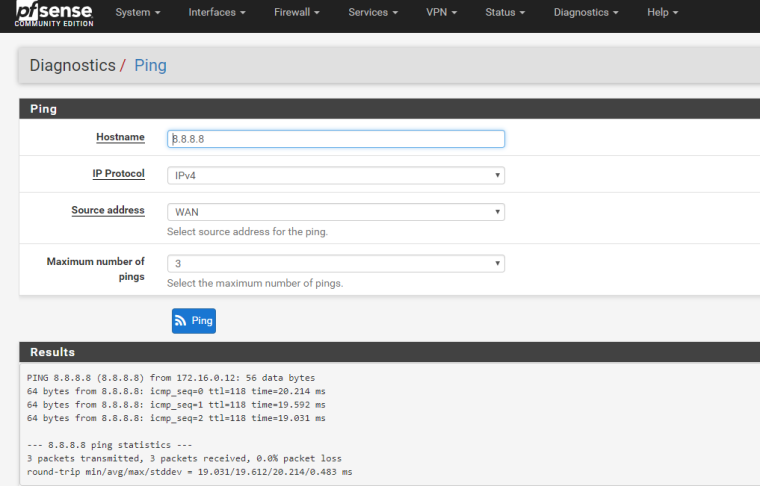
-
@tmedtcom
Interface rules? Floating rules? -
@bhjitsense said in Pfsense block ICMP echo reply from WAN to OPT1:
Interface rules
The interface is INTERNAL (OPT1)
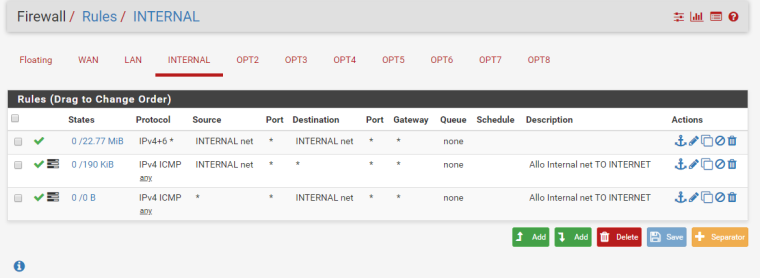
FLOATING RULES/
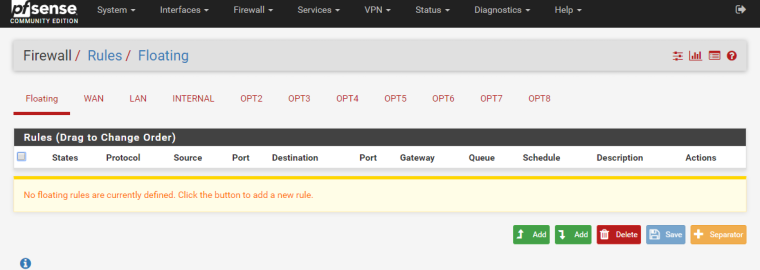
-
@tmedtcom said in Pfsense block ICMP echo reply from WAN to OPT1:
LAN interface 172.16.0.11
WAN interface 172.16.0.12What? Sorry it doesn't work that way you can not have the same network on wan and lan interface..
And those rules on your internal are just BORKED..
When would internal need to talk to pfsense to talk to other internal?
-
@johnpoz
LAN interface: this interface it is configured to just connecting to pfsense (ssh/web interface) just for admin.
WAN interface to allow users to connect to many VMs via NAT.
INTERNAL OPT1 this network is reserved to VMs servers on my VMware ESXI HOST. -
And AGAIN you can not have the same network on 2 different interfaces... This basic routing 101... I don't even think pfsense will let you do that..
-
@tmedtcom
You don't nee the third rule if you have that first rule. Also, change the first rule to be INTERNAL net > INTERNAL address. Or ANY > INTERNAL address.Also, post your WAN rules.
-
WAN interface to allow users to connect to many VMs via NAT.
Huh? Why would you be natting between local rfc1918 networks or vm networks?
I have run pfsense on esxi for many years through multiple versions of esxi going back to 4.. Before that even ran it on the old school vmware server 1 and 2..
Please draw up how you have this stuff connected in esxi with your vswitches and connected to pfsense and how your vswitches are connected to your physical network.. Port groups, are you doing any vlan tagging anywhre or different vswitches - are they standard or distributed switches, etc. etc.
-
My bet is on NAT being borked. You are allowing the ICMP traffic out of INTERNAL, but it doesn't know its way back for the reply.
-
@bhjitsense said in Pfsense block ICMP echo reply from WAN to OPT1:
@tmedtcom
You don't nee the third rule if you have that first rule. Also, change the first rule to be INTERNAL net > INTERNAL address. Or ANY > INTERNAL address.Also, post your WAN rules.
WAN Rules:
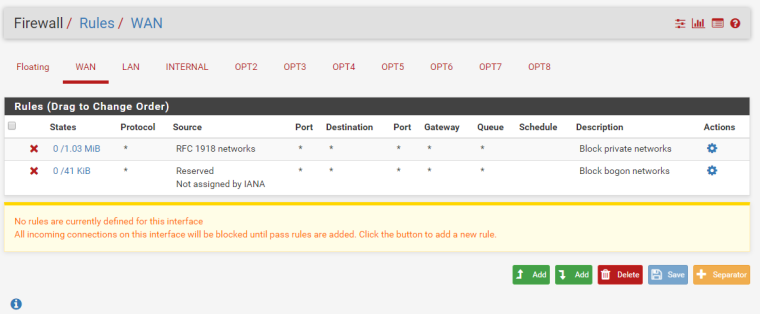
-
@johnpoz said in Pfsense block ICMP echo reply from WAN to OPT1:
Huh? Why would you be natting between local rfc1918 networks or vm networks?
In the internal Network I have multiple web servers and in the WAN network I have a users on laptop connected to Cisco for Internet and I would like to allow users to access to my Web servers via NAT on WAN: 172.16.0.12:8080
So pfsense it is the intermidiate router between 2 network 172.16.0.0/24 (WAN) and 192.168.10.0/24Also in ESXI 6.5 I have a standard virtual switch with 2 group port:
- VM network bridget to phisical card
- VLAN 10 => this is my Internal network
-
@bhjitsense said in Pfsense block ICMP echo reply from WAN to OPT1:
My bet is on NAT being borked. You are allowing the ICMP traffic out of INTERNAL, but it doesn't know its way back for the reply.
Yes I also see that there is no return in the logs:
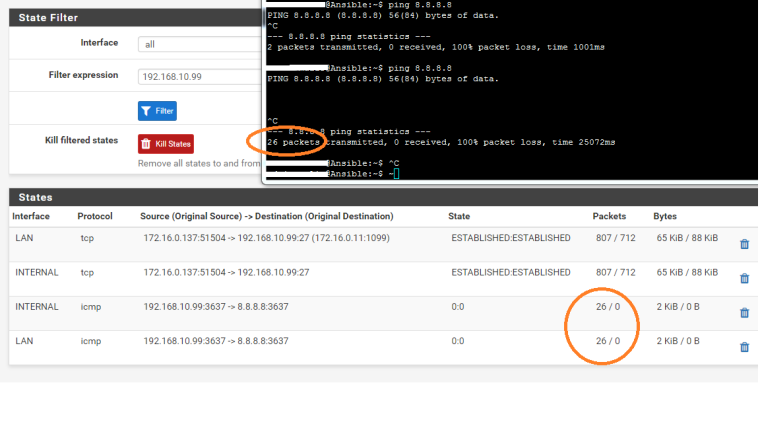
But why and how to solve it? -
well if you want to access from rfc1918 to networks behind pfsense via your going to have to remove that rfc1918 block for starters.
If you want to use pfsense as a downstream network from your cisco then there should be a transit network and nat should only happen then talking to the internet and your cisco should nat all your downstream networks, etc.
Or you should just double nat everything behind pfsense, etc.
Why are you using vlan 10? Are you setting the vlans up in pfsense - what does your vswitch/port group do with the vlan(s) what do you have set on this port group, etc. etc..
But you do NOT put the same network on multiple interfaces... And if your wanting to nat from rfc1918 to rfc1918 you going to have to remove that rfc1918 block.