2.4.4 ICMPv6 Firewall Rules?
-
There is a good'ol rfc that is still explaining this exactly:
https://tools.ietf.org/html/rfc4890#section-4.3 -
IPv6 relies much more on ICMP than IPv4. Generally you don't need to block much, if anything. As mentioned in that RFC, ICMPv6 includes protections, such as that 255 hop count, that ensure messages don't come from beyond the next device.
-
@sigi said in 2.4.4 ICMPv6 Firewall Rules?:
There is a good'ol rfc that is still explaining this exactly:
https://tools.ietf.org/html/rfc4890#section-4.3Thanks for that source. In my case (just a single site (home) with a few computers and devices on the local network), it looks like I definitely need to allow the following into the WAN interface:
- Echo Reply
- Echo Request
- Parameter Problem (invalid IP header)
- Time Exceeded
- Packet Too Big
- Destination Unreachable
I definitely need to NOT allow the following into the WAN interface:
- Node Information Request
- Node Information Reply
If I had multiple sites that needed to communicate (i.e., if my pfSense were a Firewall/Bridge), I'd need to allow:
- Neighbor Advertisement
- Neighbor Solicitation
- Redirect
- Router Advertisement
- Router Solicitation
That still leaves the following from pfSense's list of ICMP Subtypes:
- FQDN Reply (not mentioned in document)
- FQDN Query (not mentioned)
- Group Membership Query (not mentioned)
- Group Membership Report (not mentioned)
- Group Membership Termination (not mentioned)
- Multicast Listener Done (will be dropped anyway)
- Multicast Listener Report (will be dropped anyway)
- Multicast Listener Query (will be dropped anyway)
- Mtrace Messages (not mentioned)
- Mtrace Resp (not mentioned)
- Who Are You Reply (not mentioned)
- Who Are You Request (not mentioned)
I assume I can safely NOT allow them into the WAN interface.
-
Thinking about this a bit more, the pair of rules I noted in my OP (which I've modified as per the above and am using) are separated into one for traffic going to the LAN and one for the router, itself. Is there any reason for that? In my case, on my SG-4860, my WAN port is going to my cable modem and the internet. Everything else (all my internal stuff) is off my LAN port. Since the two rules are identical except for the destination, I should be able to replace them with one rule with the destination set to anything (i.e., "*"). Right? There's nothing special about including the WAN Address but not the WAN net there, is there?
-
@beremonavabi said in 2.4.4 ICMPv6 Firewall Rules?:
If I had multiple sites that needed to communicate (i.e., if my pfSense were a Firewall/Bridge), I'd need to allow:
Neighbor Advertisement
Neighbor Solicitation
Redirect
Router Advertisement
Router SolicitationIf you block those you will definitely kill IPv6. Neighbor Adversiments & Solicitations are the equivalent of IPv4 ARP. Without them you have nothing. Same for Router Advertisement and Solicitation.
-
@jknott said in 2.4.4 ICMPv6 Firewall Rules?:
@beremonavabi said in 2.4.4 ICMPv6 Firewall Rules?:
If I had multiple sites that needed to communicate (i.e., if my pfSense were a Firewall/Bridge), I'd need to allow:
Neighbor Advertisement
Neighbor Solicitation
Redirect
Router Advertisement
Router SolicitationIf you block those you will definitely kill IPv6. Neighbor Adversiments & Solicitations are the equivalent of IPv4 ARP. Without them you have nothing. Same for Router Advertisement and Solicitation.
From what I can make out of this section:
https://tools.ietf.org/html/rfc4890#page-15
Those are needed within the local network (probably not the correct wording). But, unless we're in a Firewall/Bridge situation, they should never come in (or go out) the WAN interface:
"4.3.3. Traffic That Will Be Dropped Anyway -- No Special Attention
NeededThe messages listed in this section are all involved with local
management of nodes connected to the logical link on which they were
initially transmitted. All these messages should never be propagated
beyond the link on which they were initially transmitted. If the
firewall is a firewall/bridge rather than a firewall/router, these
messages should be allowed to transit the firewall as they would be
intended for establishing communications between the two physical
parts of the link that are bridged into a single logical link.During normal operations, these messages will have destination
addresses, mostly link local but in some cases global unicast
addresses, of interfaces on the local link. No special action is
needed to filter messages with link-local addresses in a firewall/
router. As discussed in Section 4.1, these messages are specified so
that either the receiver is able to check that the message has not
passed through a router or it will be dropped at the first router it
encounters...."So, they don't need to be allowed in a WAN firewall rule (on my simple setup).
-
@beremonavabi said in 2.4.4 ICMPv6 Firewall Rules?:
@jknott said in 2.4.4 ICMPv6 Firewall Rules?:
@beremonavabi said in 2.4.4 ICMPv6 Firewall Rules?:
If I had multiple sites that needed to communicate (i.e., if my pfSense were a Firewall/Bridge), I'd need to allow:
Neighbor Advertisement
Neighbor Solicitation
Redirect
Router Advertisement
Router SolicitationIf you block those you will definitely kill IPv6. Neighbor Adversiments & Solicitations are the equivalent of IPv4 ARP. Without them you have nothing. Same for Router Advertisement and Solicitation.
From what I can make out of this section:
https://tools.ietf.org/html/rfc4890#page-15
Those are needed within the local network (probably not the correct wording). But, unless we're in a Firewall/Bridge situation, they should never come in (or go out) the WAN interface:They are required on every link. If you look at the packets with Wireshark, you'll see many of them, such as those advertisements and requests, have a hop limit set to 255. This means it's impossible for them to have come from anything other than an adjacent device. Any other hop limit makes those ICMPv6 messages invalid and will be discarded Those ICMPv6 messages are NEEDED for IPv6 to work.
-
The icmpv6 rules that are required for IPv6 to work are allowed but hidden, just like dhcp is when you enable dhcp.. There is no need to worry about setting rules to allow the required stuff for IPv6 to function.
They do this from keeping users from shooting themselves in the foot..
-
I agree. Those ICMP packets are needed within the local network. All I'm doing is not allowing them to come into the WAN interface from the outside (which, for me, is the internet (only)). I've got no rule anywhere that blocks ICMP packets within the network (on my sole active, LAN, interface).
-
@beremonavabi said in 2.4.4 ICMPv6 Firewall Rules?:
All I'm doing is not allowing them to come into the WAN interface from the outside
What part of essential do you not understand? They're used on the WAN link just as on the LAN. There is already protection to keep them from coming from beyond an adjacent device through the hop limit, which must be 255 on a valid ICMPv6 message. Fire up Wireshark or Packet Capture on the WAN port to see them. You'll see they are intended for your firewall and have a hop limit of 255. The way that works is if the packet has a hop limit of 255, it can't have come from any other than the adjacent device. For it to have passed through a router, it would have entered the router with a hop limit of 0, which the router would then discard. If a packet with any other hop limit makes it through the router, it would have a value other than 255, which would also caused it to be discarded as invalid. You're trying to protect against a problem that doesn't exist.
-
Neighbor Advertisement
Neighbor Solicitation
Redirect
Router Advertisement
Router SolicitationAs far as I can see, all of those are solely of use on the local network (one, single segment -- which is all I have):
https://www.computernetworkingnotes.com/networking-tutorials/ipv6-neighbor-discovery-protocol-explained.html
AFAIK, they're used on the WAN link only if I have other subnets that communicate through that interface,
I don't. To me, the outside of the WAN interface is just the internet. And, nothing on the internet should legitimately be sending those to enter my WAN link (again, that I know of). And, as you've said, if something did, it should be discarded by pfSense as it entered. Nothing of mine is on anything but the LAN. AFAIK, the only adjacent devices I care about are internal to the LAN and will happily send those ICMP packets across the LAN without interference. Why would I want to add rules to my WAN's firewall so those packets can come in when I could more easily just leave them off and, with no effort on my part, ensure they never get in regardless of whether or not pfSense should drop them anyway because of the 255 hop limit?Can you give me a concrete example of how my not allowing those ICMP subtypes into my WAN interface from the internet is breaking anything? That's a real question. I honestly can't think of anything on the internet that would need "a set of messages and processes defined in RFC 4861 that determine relationships between neighboring nodes" (from that link, above) on my local network. But, I'm not an expert.
-
Perhaps we're focusing on different elements. I'm focusing on what's allowed into the LAN. Are you worried about what's happening at the pfSense level? Here are my current rules:
WAN:
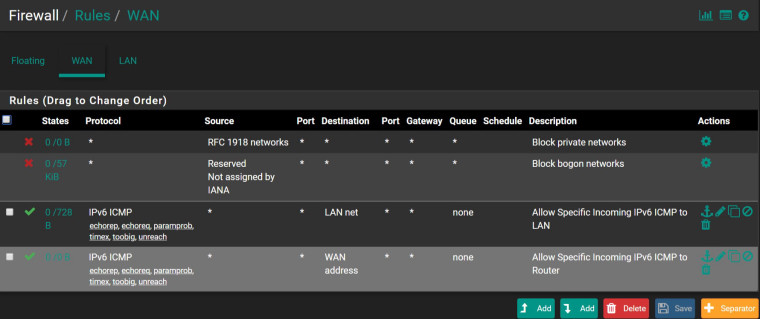
I can't see why any of those Neighbor Discover subtypes should be allowed into LAN net (the first rule). But, are you saying they need to be allowed into the WAN address (the second rule)? By blocking them there, am I preventing pfSense from finding external neighbors and routes?
-
You can put the rules there all you want - the hidden rules are hidden ;) And are going to happen before you..
How exactly is your firewall going to talk to the internet via IPv6 on the wan if you do not allow those - so its gateway can be found.. Um you do not need to allow anything other then echo through to your lan from the internet.. etc..
-
@beremonavabi said in 2.4.4 ICMPv6 Firewall Rules?:
As far as I can see, all of those are solely of use on the local network (one, single segment -- which is all I have):
I just ran Packet Capture on my WAN interface and saw NS & NA messages. They are there because they are needed. As Johnpoz says, you can't block them anyway. So, what exactly is it you're trying to do? IPv6 relies much more on ICMP than IPv4 and quite frankly won't work without it. Perhaps you need to learn a bit more about IPv6. I can recommend O'Reilly's IPv6 Essentials.
-
Just at a loss to understanding what he is attempting to do..
The required icmpv6 stuff for ipv6 to work on wan - is there!!! Same goes for lan side for clients to find pfsense as their ipv6 gateway.. There is NOTHING you need to add..
All other to wan would be blocked out of the gate - if you want to allow actual ping response.. Then you can add that.. Same sort of thing goes if you want to allow into your lan from outside..
Example I allow echoreq into my my ntp server IPv6 address from internet.. And to ping pfsense IPv6 wan side IP, etc. There is little reason to add any other rules..
-
According to:
https://www.netgate.com/docs/pfsense/book/network/ipv6-subnets.html?highlight=icmpv6#neighbor-discovery
"...pfSense automatically adds firewall rules on IPv6 enabled interfaces that permit NDP to function. "
Am I supposed to be able to see that rule in my Firewall rules (I don't)? Or is it just an implied rule like the default deny on incoming traffic? Does that statement imply we don't need to add any special ICMPv6 rule at all?
-
@beremonavabi Maybe you should go once to cli or "Diagnostics / Command Prompt" and execute
"pfctl -s rules" this will help you understand about hidden rules.. -
@beremonavabi said in 2.4.4 ICMPv6 Firewall Rules?:
"...pfSense automatically adds firewall rules on IPv6 enabled interfaces that permit NDP to function. "
You have ZERO add which is what have been telling you ;)
-
@sigi said in 2.4.4 ICMPv6 Firewall Rules?:
@beremonavabi Maybe you should go once to cli or "Diagnostics / Command Prompt" and execute
"pfctl -s rules" this will help you understand about hidden rules..Thanks. According to that:
Shell Output - pfctl -s rules ... pass quick inet6 proto ipv6-icmp all icmp6-type unreach keep state pass quick inet6 proto ipv6-icmp all icmp6-type toobig keep state pass quick inet6 proto ipv6-icmp all icmp6-type neighbrsol keep state pass quick inet6 proto ipv6-icmp all icmp6-type neighbradv keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type echorep keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type routersol keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type routeradv keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type neighbrsol keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type neighbradv keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type echorep keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type routersol keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type routeradv keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type neighbrsol keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type neighbradv keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type echoreq keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type routersol keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type routeradv keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type neighbrsol keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type neighbradv keep state pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type echoreq keep state pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type routersol keep state pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type routeradv keep state pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type neighbrsol keep state pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type neighbradv keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type echoreq keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type routersol keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type routeradv keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type neighbrsol keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type neighbradv keep state pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type echoreq keep state pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type routersol keep state pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type routeradv keep state pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type neighbrsol keep state pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type neighbradv keep state ...That makes much of this discussion moot. It looks like fSense defaults to allowing (with various restrictions):
Packet Too Big
Destination Unreachable
Echo Reply
Echo Request
Neighbor Advertisement
Neighbor Solicitation
Router Advertisement
Router SolicitationOddly, of the Neighbor Discovery subset, it doesn't default to allowing Redirect. I wonder why? Of course, if it defaults to allowing those ICMPv6 subtypes into the system, why not those other "must pass" subtypes:
Parameter Problem (invalid IP header)
Time Exceeded? -
@johnpoz Sorry for bumping this but is there a way to see "hidden" rules? The ICMPv6 "hidden" doesn't seem to allow echo reply so when it's said that pfSense has automatic rules for things to work, but things like echo doesn't work. This ambiguity is a source of some frustration.