"Default Deny" from My Computer to Multicast Log Entries [SOLVED]
-
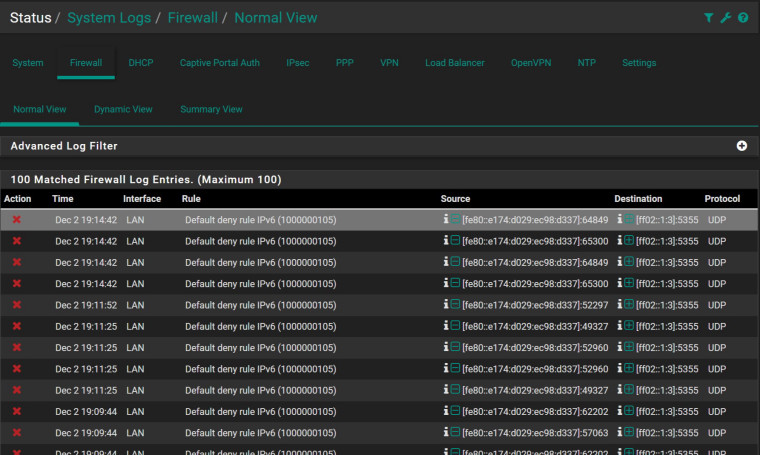
I keep getting these "Default Deny" entries in my firewall and I don't understand why/how they're being denied:
Dec 2 07:44:50 LAN Default deny rule IPv6 (1000000105) [fe80::e174:d029:ec98:d337]:52993 [ff02::1:3]:5355 UDP Dec 2 07:44:50 LAN Default deny rule IPv6 (1000000105) [fe80::e174:d029:ec98:d337]:51969 [ff02::1:3]:5355 UDP Dec 2 07:44:50 LAN Default deny rule IPv6 (1000000105) [fe80::e174:d029:ec98:d337]:51969 [ff02::1:3]:5355 UDP Dec 2 07:44:50 LAN Default deny rule IPv6 (1000000105) [fe80::e174:d029:ec98:d337]:52993 [ff02::1:3]:5355 UDPI'm pretty sure that's blocking IPv6 multicasts from my own computer on the LAN to other things on my LAN. I have no blocking Firewall rules of my own on my LAN at all, so these have got to be coming from the default deny rules (as stated). But, I don't see anything with pfctl -s rules that would explain this. The only things showing there with that label are the expected:
block drop in log inet6 all label "Default deny rule IPv6"
block drop out log inet6 all label "Default deny rule IPv6"Here are my LAN firewall rules:
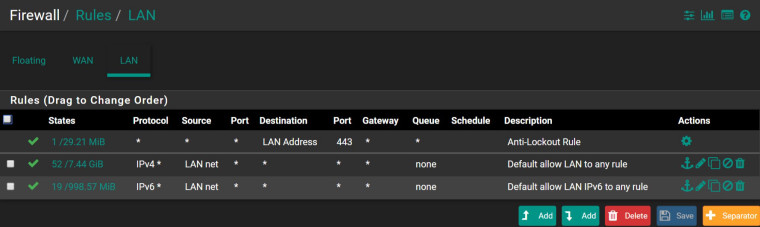
Is that multicast address not considered to be part of LAN net?
-
fe80:: != LAN net add a firewall rule
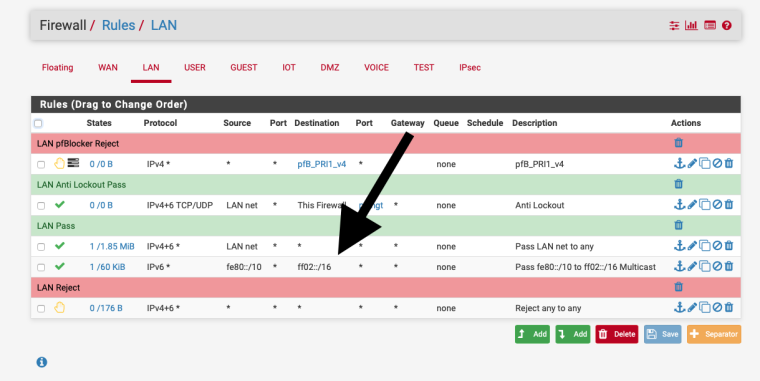
-
Thanks.
[I've deleted a whole bunch of stuff here because it was wrong and huge]
EDIT: I've added a rule just like yours and I still get the default denies in my Firewall log.
-
Since I can't figure out why this is still happening, I'll put in some screenshots just in case my eyes are playing tricks with me on what I'm seeing and what I've done. The Firewall rule is on my LAN and should cover everything with a link local address on my LAN being sent to the link local multicast address on the LAN. As far as I can see, that's what those default denies are saying. Yet, that rule isn't even firing (evaluations, packets, bytes, states, and state creations are all 0 -- and I've reset my States):
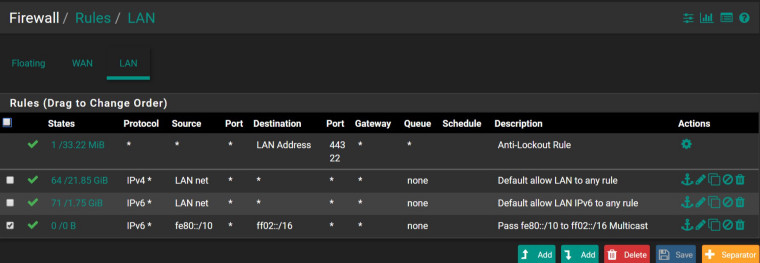
-
Try killing the firewall states.
-
I had reset my states and also rebooted pfSense, but that didn't help. I updated to 2.4.4_1 and it all seems to be working properly now, though.
-
I didn't check in 2.4.4, but in 2.4.4_1, I see the following with pfctl -s rules:
... pass quick on igb0 inet6 proto udp from fe80::/10 to ff02::/16 port = dhcpv6-client keep state label "allow access to DHCPv6 server" pass quick on igb0 inet6 proto udp from fe80::/10 to ff02::/16 port = dhcpv6-server keep state label "allow access to DHCPv6 server" ...It's specific to "port = dhcpv6-server", so I don't know if 2.4.4_1 automatically fixes this. I'll disable my rule for a bit and see what happens.
EDIT: I don't think those default rules will fix this since the dhcpv6 ports are 546 and 547, while I was getting these default denies on ports 5355 and 27036.
-
Nope. That manual rule is definitely needed.
-
port 5355 is multicast DNS
https://en.wikipedia.org/wiki/Multicast_DNS
-
BTW: Please inform yourself about "what is IPv6 link local addressing" and when is it needed. And then multicast: Even when you allow this: Multicast over L3 is another story. When this thread only is about "do not log rules" it is ok too.
