connected but cant access vpn lan after upgrade to 2.4.4 p1
-
@ariban99 try removing 192.168.3
.0 from remote networks on the working config.
Remember to clear states and restart openvpn. -
Hi
thank you. that works now.
however, now i can not access between the 2 remote locations. so from each remote i can access the main server. but between remote locations, i cant access each other.
is there a way to talk to the 2 remote locations. so in this example
from 192.168.3.0 (tunnel 10.0.3.0)
to 192.168.2.0 (tunnel 10.0.1.0)thank you
-
Assign ovpn interfaces ( if you havent done already) and policy route among the two is probably the way to go.
Put roules on openvpn tab sending traffic with specific source and destination to relevant openvpn interfaces respectively.
It should work -
hi
so i am lost, how do i do all the above? sorry i dont know this stuff very well.
any tutorials to follow? -
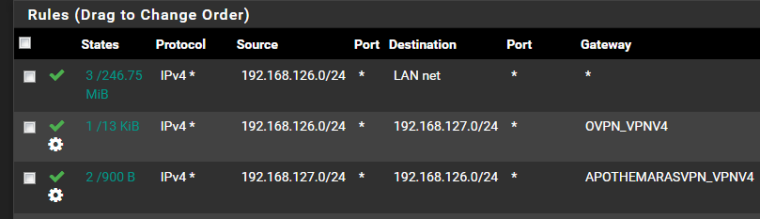
Here is an example.
There are two tunnels 192.168.126.0/24 and 192.168.127.0/24 with two interfaces
One rule specifies source 192.168.126.0/24 target 192.168.127.0/24 and send packets to 192.168.127.0 assigned gateway.
a second rule does the opposite
All this under firewall rules openvpn. -
i will try that, thank you for all your help
-
Tunnel addresses are usually in the same subnet..
-
so i dont think i am doing it correctly.
i assigned OPT1 and OPT2 for the openvpn
so OPT1 is for 192.168.2.0
and OPT2 is for 192.168.3.0then enabled them.
under rules, OPENVPN tab.
i create a new rule.
interface, WAN
IPV4
ANY
source, i selected OPT1
destination OPT2and i did the reverse for the second openvpn but its still not working.
what am i doing wrong? -
Your "Tunnel" networks.. put both sides of the VPN tunnel in the same subnet.
tunnel 10.0.3.0/30 When you do this each box will take an address in this subnet.
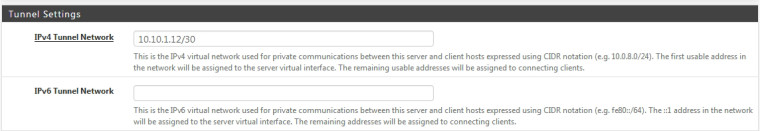
-
@chpalmer
On your second VPN tunnel use a different subnet.. -
I never assign my own OpenVPN sessions to an interface on the box. So you might be seeing another issue that I wouldn't see but the information above is correct either way. IP Tunnel network on each side should be in the same subnet.
Remote network is the network(s) of the box on the other side.
-
@ariban99 said in connected but cant access vpn lan after upgrade to 2.4.4 p1:
so i dont think i am doing it correctly.
i assigned OPT1 and OPT2 for the openvpn
so OPT1 is for 192.168.2.0
and OPT2 is for 192.168.3.0You do not number OpenVPN assigned interfaces. You simply assign them then enable them then bounce that OpenVPN instance. You do not specifically number them in the interface configuration. Might be misunderstanding what you're doing but that's what I read.
-
Just assign interfaces to openvpn tunnels.
DON'T put ip's there, it will happen automaticaly by openvpn. -
@netblues said in connected but cant access vpn lan after upgrade to 2.4.4 p1:
Just assign interfaces to openvpn tunnels.
DON'T put ip's there,Just like Derelict said..
What does assigning tunnels to interfaces get over just building the tunnel on the router and not assigning them to interfaces? Just curious..
-
@chpalmer said in connected but cant access vpn lan after upgrade to 2.4.4 p1:
Just assign interfaces to openvpn tunnels.
DON'T put ip's there,It creates the interfaces so you can policy route, add rules, monitor traffic, etc...
-
Thanks!
From your list the only thing it seems I don't have is the ability to monitor with the graphs.. you would have to elaborate on the ect..
But just curious..
-
@chpalmer https://www.netgate.com/docs/pfsense/book/openvpn/assigning-openvpn-interfaces.html
-
@netblues said in connected but cant access vpn lan after upgrade to 2.4.4 p1:
https://www.netgate.com/docs/pfsense/book/openvpn/assigning-openvpn-interfaces.htmlThanks! Ive been wondering but never asked.
Adds a firewall tab under Firewall > RulesWe have this. Maybe past incarnations did not..??
Adds reply-to to rules on the VPN interface tab to help with return routing Adds a Gateway entry for the far side of the VPN for policy routing Allows the interface to be selected elsewhere in the GUI and packages Allows more fine-grained control of Port Forwards and Outbound NAT for the VPNGood to know.
-
@chpalmer said in connected but cant access vpn lan after upgrade to 2.4.4 p1:
Adds a firewall tab under Firewall > RulesWe have this. Maybe past incarnations did not..??
Now you have one for each tunnel.
If you are just using one tunnel, then you can get away without assigning an interface
(it will be happening dynamicaly behind the scenes).
In more complex scenarios an assigned interface comes handy.
Say, remote client with no split tunnel accessing specific site using nat which happens at another remote client connected via another openvpn tunnel.
One use for that is geolocation bypass.
Another is using a vps host in a datacenter as a static ip gateway. -
Thanks!
On my OpenVPN tab I simply make a rule for each VPN subnet Im controlling. I have ten different tunnels coming into this location alone besides a roadwarrior setup..
I do think the OP could simplify his setup a bit in this fashion.
from one of our spur sites..
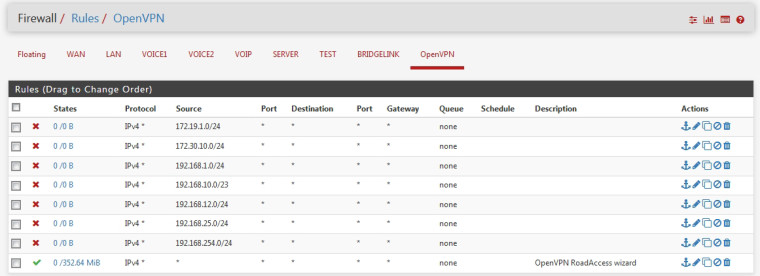
Ive since tightened up the road warrior rule and thus done away with all the blocking rules.