Azure - Marketplace - Virtual Appliance pfSense environment
-
Hi there,
we are currently setting up our new environment in azure. So we have now the opportunity to implement a firewall in front of the virtual machines.
pfSense has now a virtual appliance on the azure marketplace. Is it recommended to use this version?
I had created a marketplace vm and added a secondary LAN Interface, because this is not possible in the first steps.We would like to have the following Azure environment:
1x pfSense Firewall with Public IP
1x Virtual Network with Subnet 100.100.10.0/24 -> WAN Network
1x Virtual Network with Subnet 100.100.1.0/24 -> LAN Network
several VM´s inside the LAN Subnet 100.100.1.0/24 but with public IP´s to reach the VM´s directly.All Network Traffic from LAN Network routed through the pfSense.
My local environment:
2x pfSense HA with 3x Subnets and 3x WAN Interfaces- Subnet = 10.10.10.0/24
- Subnet = 10.10.20.0/24
I have tested this with this resources:
1x Virtual Network Gatway on Azure IPSEC -> Azure to Local Environment Connection
1x Virtual Appliance with 2 NICs:
- WAN = 100.100.10.5 (Gateway WAN = 100.100.10.1)
- LAN = 100.100.1.5 (Gatway LAN = 100.100.1.1)
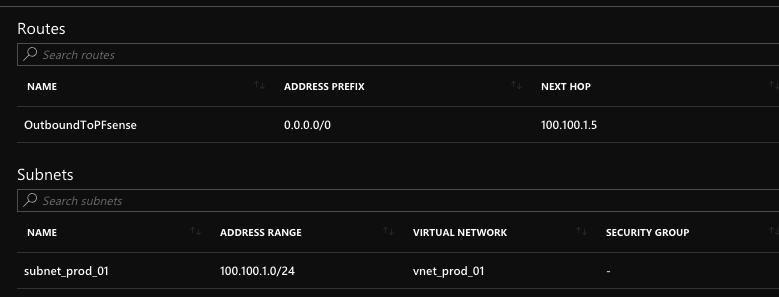
i added a route in azure:
On pfSense in Azure i can access my local network and my lan network:
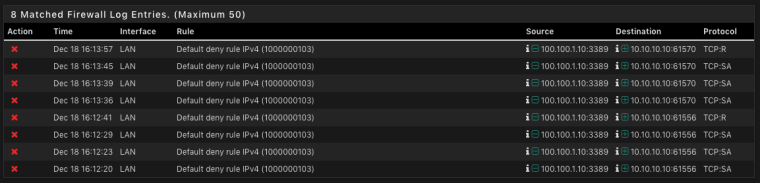
- Port test to host: 10.10.10.10 Port: 443 successful. (Local)
- Port test to host: 100.100.1.10 Port: 3389 successful. (Azure LAN)
On my local network i can access:
- Port test to host: 100.100.10.5 Port: 443 successful (Azure pfSense)
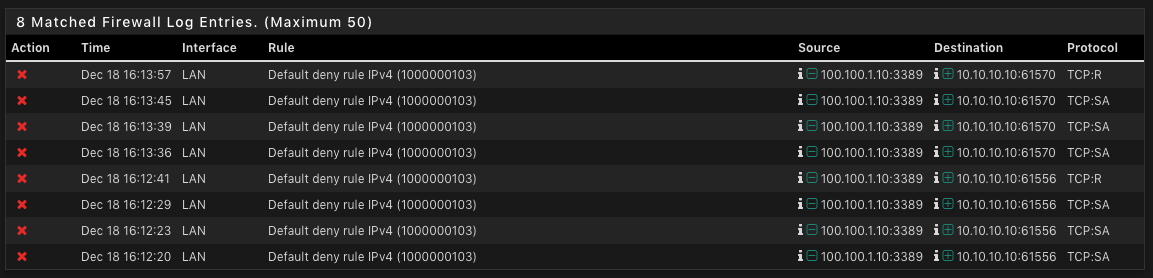
- but can´t access my LAN Network 100.100.1.10 Port: 3389 failed
In the firewall log there are following entries:
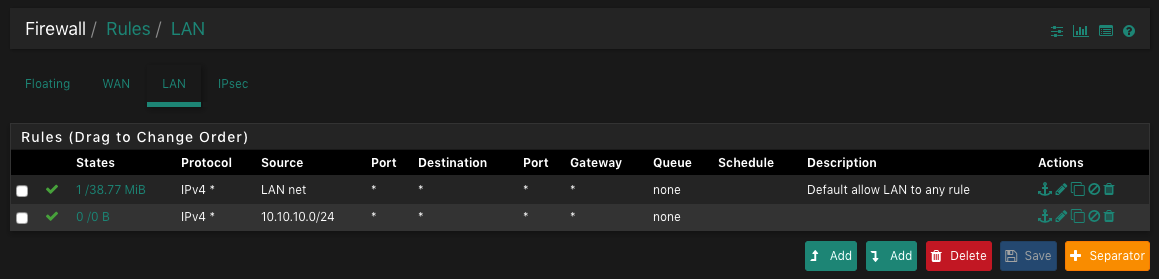
This is my pfSense firewall configuration:
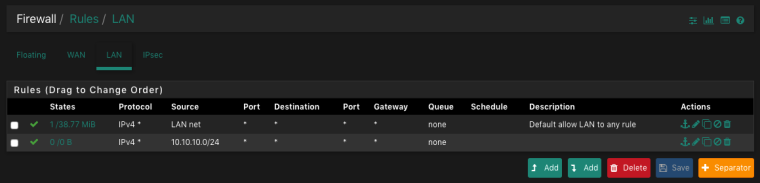
I think there is a mistake which i cant see right now. Can you please help me?
Thanks and kind regards,
David -
Stay within RFC1918 space for local networks.
-
but for local network im staying in this space?
Local Network: 10.10.10.0/16
- Subnets: 10.10.10.0/24, 10.10.20.0/24, 10.10.30.0/24
Azure Network: 100.100.0.0/16
- Subnets: 100.100.10.0/24, 100.100.1.0/24, 100.100.2.0/24
-
@genesis_mp said in Azure Virtual Appliance pfsense:
Azure Network: 100.100.0.0/16
Nope. https://tools.ietf.org/html/rfc1918
-
This post is deleted! -
@grimson Do you mean i have to stay in both local networks between the space? 10.0.0.0 - 10.255.255.255
Azure and my local network?
-
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16-Rico