pfsense bypasses firewall rule
-
Hi. I won't detail exacly the background on what i'm trying to accomplish because that's a complicated story.
my issue is: i have setup openvpn server in pfsense. it is working and clients can connect. i'm using certificate auth.
i need to block a certain IP address from connecting, even with valid authentication, and for that i was expecting that creating a rule before my allow vpn rule would do it. somehow, pfsense is bypassing the rules i set for the vpn traffic.
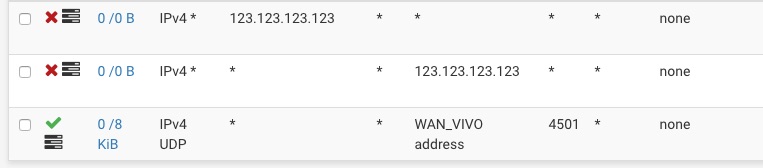
my vpn server listens on 4501 port. (you can ignore the 0 states on the bottom pass rule)
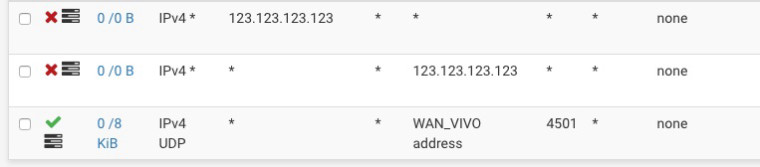
my expectation is that client from 123.123.123.123 (sample ip) wouldn't connect, but they do
-
are those your WAN rules?
-
yes
-
If the connection is active when you hit save you may have to flush your states to take down the connection..
-
i went as far as rebooting pfsense entirely to ensure the new rules would take place. but they didn't affect the traffic. i also went advanced settings and under "Firewall & NAT" i have checked the option "Disable all auto-added VPN rules."
-
This client is coming in via the WAN right?
-
yes... so client hits the WAN interface, which is listening on 4501/udp. they should hit the firewall rule in the order i displayed
-
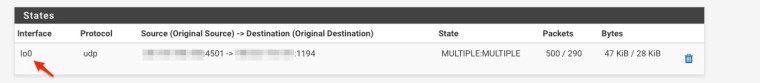
what is interesting is that when i check states, the connection is shown on the loopback interface. maybe this has some correlation
-
This post is deleted! -
I just killed all my VPN traffic off to test this. The firewall seems to initiate the state and when that happens the connection opens up.
Go to status/openvpn and stop the service. Then go to diagnostic/states and kill the states.
Go back to openvpn and restart the service.
-
@chpalmer thanks! it worked as you described!
however, in the event of a reboot, do you know how would i prevent this issue from happening? (i'm assuming it's the order things are loaded, first vpn then filters... if that even makes sense)
-
@thenmanbr said in pfsense bypasses firewall rule:
@chpalmer
however, in the event of a reboot, do you know how would i prevent this issue from happening? (i'm assuming it's the order things are loaded, first vpn then filters... if that even makes sense)I do not.. I comes as a little bit of a surprise to me as well. I use separate VPN servers for each of my tunnels and Im the only road warrior connection here. If I was to stop a connection to a site I would first go to that site and delete the client.
Can you try a "reject rule" and see if that does it?..