VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?
-
No. That has nothing to do with how traffic is routed.
-
@derelict said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
No. That has nothing to do with how traffic is routed.
But then what does setting the DNS Server gateway to my VPN interface do? I was thinking that it is the equivalent of setting Outgoing Network Interface in DNS Resolver.
-
That might work for you but you will break DNS for the whole firewall if the VPN is down.
Honestly, the best way to ensure you don't "leak" DNS is to tell your clients to use the outside DNS providers, policy route that traffic, and forget the on-firewall resolver exists.
Or, again, put an off-firewall DNS resolver together that can be policy routed like the client traffic on its way into LAN.
-
@derelict I am just starting to get your point but what I am getting at is when Quad9 goes via my VPN, dnsleaktest.com reports internet.exchange ip for DNS and not woodynet. Is this normal?
-
You'll have to post real, contrasting "leak test" results. I have no idea what you're trying to ask.
-
This post is deleted! -
I think this thread has strayed off topic. Most VPN services have instructions on how to set up pfSense with their VPN, if they are compatible. There are YouTube videos for PIA. Most of these questions would be answered in the instructions.
Although, I do admit my setup is contrary to what the VPN service recommends, hence, the thread.
I would make sure to follow the VPN service's instructions for pfSense. Make sure your results are as expected and you understand them. Only then, try using a different DNS configuration than recommended by the VPN, as I did here.
-
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
I'd like to add - Early in my testing, I observed the PIA DNS servers responded to TCP 853. So, I thought maybe they enabled DNS over TLS w/o announcing it. I tried using the PIA DNS servers and also pointing the pfSense DNS resolver to PIA. It didn't work. I could only get DNS over TLS to validate outside of a VPN tunnel (OpenVPN).
I still don't know whether VPN services simply choose not to support DNSSEC/TLS or that OpenVPN is incompatible with DNS over TLS. (If someone answered that above, sorry, I missed it.) I found one VPN service advertise that they support both 'VPN' and 'DNS over TLS'. However, it sounded more like 'either / or' -not- both. It just sounded like their DNS servers would support TLS, but it wasn't clear that it was through their VPN service (more like they inferred it was outside their VPN service).
I can see their point (the VPN services). The VPN tunnel makes TLS redundant. Then again, going back to the difference between DNS over TLS and DNSSEC, the VPN tunnel only 'encrypts' the DNS message, it doesn't validate it. Wouldn't that imply that the combination of DNS over TLS (encryption) -and- DNSSEC (validation) trumps VPN (encryption only)?
I could be off my rocker here but thought the conversation is worth having.
I've made a minor change to my configuration. I thought I may as well share it, to keep the explanation of my configuration accurate...
Until now, I configured my DNS Resolver to send DNS request out my WAN / Non-VPN connection. For some reason, I thought if I sent it through my VPN tunnel, it wouldn't work. I tried it and it works fine. So, my DNS requests:
- Use Quad9 & Quad1
- Use and validate to DNSSEC
- Use and validate DNS over TLS
- Are sent out through my VPN tunnel
I was reading there might be ways for an ISP to figure out your DNS requests even if you use DNS over TLS. (Just talking DNS here). Using the VPN tunnel, that won't happen. Another reason I (originally) sent the DNS request out via WAN / Non-VPN was to keep latency as low as possible on DNS requests. The VPN tunnel I'm using is the local PIA, which is the least obscure VPN connection, but a VPN tunnel, non the less. Since I'm using DNS over TLS, even the VPN won't know my DNS request anyway.
I'm feeling really good about this configuration.
-
@talaverde I gotta ask. Does dnsleaktest.com still show woodynet with quad9 and pia? For me it does not show woodynet nor pia but some internet.exchange point.
-
@gjaltemba said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@talaverde I gotta ask. Does dnsleaktest.com still show woodynet with quad9 and pia? For me it does not show woodynet nor pia but some internet.exchange point.
Hard to answer fully w/o a screenshot. dnsleaktest.com shows your DNS request hosts, not your VPN tunnel.
-
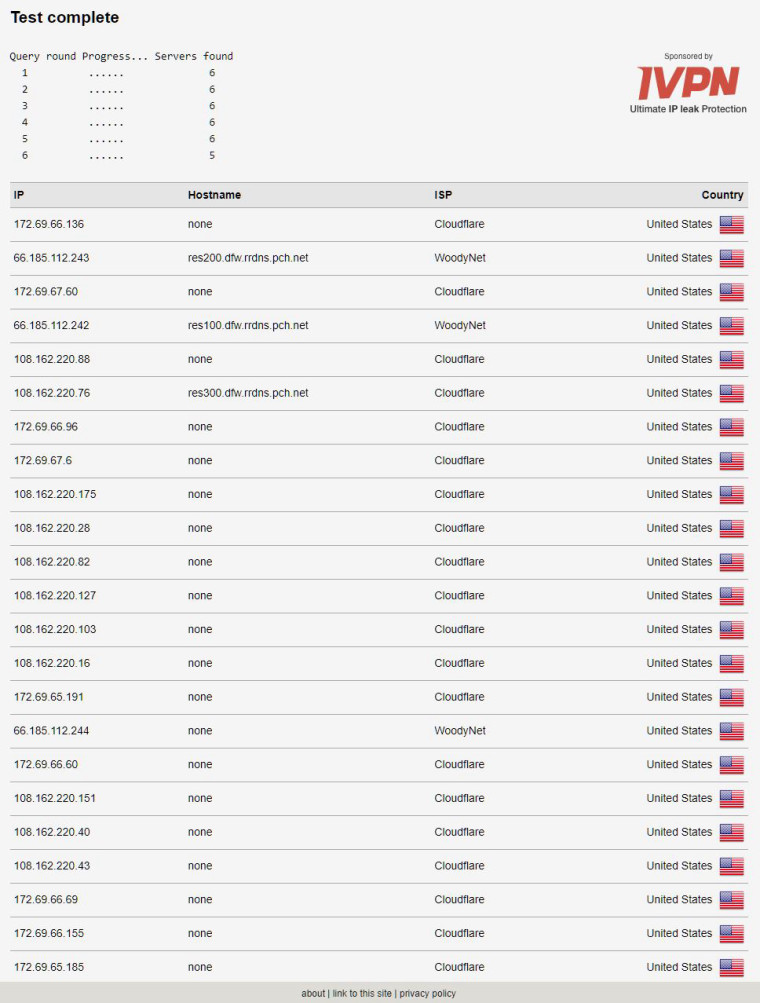
I had multiple users ask me what 'dnsleaktest' looked like when I have Quad9 and Cloudflare (Quad1) configured as my DNS servers. This is is what it looks like. OBVIOUSLY, this is not my IP address, nor my VPN's IP address. This is a list of DNS servers that respond to Quad9 or Quad1. (WoodyNet is obviously Quad1).
-
No one has contributed to this conversation for a while, so I feel like I'm talking with myself. Maybe no one else cares. A few wanted to know how to configure their VPN, but that didn't seem on topic.
At risk of sounding like I'm starting my own blog, I just want to mention this new configuration has been working GREAT!. I'm using multiple VPN providers with pfSense. At the same time, all my DNS requests are going to DNSSEC/TLS enabled DNS servers. No issues of leakage that I'm aware of. DNS requests are much quicker than using the VPN DNS servers. Spreading out the requests makes everything even more anonymous, IMO.
If anyone want more information on how I set this up (using TLS/DNSSEC, I'm open to questions, as I don't know of anyone else trying it this way.
(Setting up your VPN, there are many resources for that)
-
as i posted most of this is way over my head. i read/ try a few changes and use the basic tests i know to do.
i have 2 tunnels setup. neither are leaking per the providers tests.
my connection only drops with mullvad. (never with Air) but i have it configured to reconnect.
i am always curious how others are setup. but since my works near flawlessly i really don't want to tinker with it.
-
@talaverde Can you please share screenshots how u setup pfsense to use vpn provider and dns over tls.
I currently have dns over tls setup but i would like to add vpn tunnel to thisBTW have you hard about perfect privacy vpn which uses dns over tls but like you said then they can spy on you. Your method seems better. Please share. Thank you in advance.
Google this article
DNS-over-TLS: Now we offer encrypted DNS
Perfect Privacy, 7. September 2018@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
No one has contributed to this conversation for a while, so I feel like I'm talking with myself. Maybe no one else cares. A few wanted to know how to configure their VPN, but that didn't seem on topic.
At risk of sounding like I'm starting my own blog, I just want to mention this new configuration has been working GREAT!. I'm using multiple VPN providers with pfSense. At the same time, all my DNS requests are going to DNSSEC/TLS enabled DNS servers. No issues of leakage that I'm aware of. DNS requests are much quicker than using the VPN DNS servers. Spreading out the requests makes everything even more anonymous, IMO.
If anyone want more information on how I set this up (using TLS/DNSSEC, I'm open to questions, as I don't know of anyone else trying it this way.
(Setting up your VPN, there are many resources for that)
-
@rango said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@talaverde Can you please share screenshots how u setup pfsense to use vpn provider and dns over tls.
I currently have dns over tls setup but i would like to add vpn tunnel to this
BTW have you hard about perfect privacy vpn which uses dns over tls but like you said then they can spy on you. Your method seems better. Please share. Thank you in advance.It's difficult to provide screenshots on relevant pages w/o sharing my personal configuration/info, but we can try talking through it.
The screenshot higher on this page with Quad9 dns servers is pretty much how I have it, but I also added quad 1 as well.
As far as the rest of the configuration, it's exactly how Private Internet Access says to configure it (on their website), except that I'm not using their dns servers. I'm using the DNS SEC servers. Also, I have DNS SEC enabled in the dns resolver settings.
PIA has very good instructions. It's many steps, so it makes more sense to direct you there than me trying to re-write their instructions.
As far as Perfect Privacy, I considered it. I already have two VPN subscriptions. I might check them out, if I get bored. I would be curious what their log policy is. I would think a VPN provider would be less likely to keep logs than a public service like Quad9, but you just never know (who's not being honest). With the public providers, I can set up multiple providers, spreading my DNS requests out among many. If I used a VPN service, I would have to use that one only (though I did here hints that pfSense can be configured with multiple resolvers, but I wouldn't know how to do that at the moment.)
So, again, check out PIA instructions. Follow them to the letter. Only AFTER it's working correctly, go in and enable DNSSEC and change the DNS servers to Quad9/Quad1. Once it's working, check out the validation websites mentioned higher in this thread. If you have any specific questions, let me know.
https://www.privateinternetaccess.com/archive/forum/discussion/29231/tutorial-setup-pia-on-pfsense-2-4-2
-
So, I had to rebuild my pfSense server(s) for various reasons. Anyway, even beforehand, I noticed PIA wasn't performing as well as it did when I first implemented it. Initially, I was getting upwards of 850 MB/s of a 1GB fiber connection over VPN. As it it got worse, I ended up going with NordVPN. Because NordVPN uses actual IP addresses instead of a URL (which points to multiple IP adddresses), I would set up multiple VPN feeds and set up a gateway group. There were definitely diminishing returns with each additional connection but it did help.
Upon rebuilding my server, I couldn't even get pfSense to work with PIA anymore. The reliability was horrendous and speeds even worse. IMHO, PIA went the way of over-growth. I've had decent luck with iVPN. All the reviews rave about ExpressVPN but I've tried the twice and both times were a complete failure. If ProtonVPN had more domestic connections, I'd give them a try, but they're too small.
I really don't thinnk VPNs are 'snake oil' as they provide a clear and defined benefit. I admit, the service level can vary, but that's just the way of the world.
I'm hoping I can find another quality VPN service and would even consider setting up a VPS, as long as it was anonymous like a VPN is.
-
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
i was not a fan of PIA over openvpn either. their service dropped more than any provider i have used. and i have used several... you can use the nslookup command and type in the PIA server and it will display all of the servers it connects you too. and if your client is properly configured it WILL reconnect to what you tell it to... Nordvpn is not doing ANYthing special there
there are several vpn's out there that allow free trials. a couple days even
IMO nord was worst than PIA. and yes i tried them 2 times and both times laughed at their support and canceled my subscription.keep trying. as you can imagine it will vary by your location and provider
good luck -
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
as they provide a clear and defined benefit
Where? Other then slowing down your connection... You are just handing over your money and your trust to some other guy because you believe your ISP is spying on you.. And doing what with it exactly - handing it over to the NSA?
The only benefit they provide that is not snake oil is geo circumvention.. People that think is makes them more secure are really just drinking the koolaid they are selling you for $X a month..
-
@johnpoz said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
Where? Other then slowing down your connection... You are just handing over your money and your trust to some other guy because you believe your ISP is spying on you.. And doing what with it exactly - handing it over to the NSA?
The only benefit they provide that is not snake oil is geo circumvention.. People that think is makes them more secure are really just drinking the koolaid they are selling you for $X a month..What?? Okay, snake oil. We get it. You don't like VPNs. You don't have to use them.
I was kinda hoping you'd give some constructive instruction on how to use a VPS rather than an VPN, or prove why you think VPNs aren't secure, but I guess it's just more of the same.
-
Who says I don't like VPNs? I use vpns all day every day... I use them to get into the work network, I use them to get into my home network from work ;)
I have multiple vps around the globe that I can vpn into if I need to make sure traffic routes one way or the other to test something.. Or sure if want to geo circumvent some sort of geoblock, etc. etc.
Everyone of my VPS I can vpn into and route whatever traffic I need to route through them..
It takes 30 seconds to fire up openvpn access server on a vps.. If you need instructions on how to apt-get install something.. Or use yum or whatever your vps is running to install openvpn-as then you should get with the OS support forums, etc.
What I don't buy off on is handing of $X a month to some snake oil company that says they don't log... Trying to hide xyz from my ISP ;) Its nothing but a bunch of koolaid.. If you need to pay for xyz service to geo circumvent so you can watch netflix in the US or BBC from the US, etc.. that sure have fun... But please don't try to blow smoke up anyones ass that your doing it to protect your privacy or such nonsense... Its a all a bunch of nonsense snake oil..
Saying to use cloud or quad for multiple dns so that neither of them get all your queries... WTF!!! Really... The one advantage of using say quad is it might block some bad site.. But then if your going to also ask cloud which doesn't filter you just through away all the good you might of gotten out of handing over quad everywhere you want to go..
You have the blind leading the blind asking the retarded for help.... That is why I try and stay out of these conversations because its all a bunch freaking koolaid nonsense... Sorry for the RANT... But ARRGHHH
Some these threads - I would think I some how ended up on pfsense facebook group ;)
My Gawd dude you don't even understand the difference between dnssec and doh and or dot, etc. But you have multiple vpn services providers your handing over cash to per month so your more secure...
Even if you hide your dns queries form player X, you know once you make the even https connection through player X network the can see where you going because of the SNI is in the clear..
If you want to hide where you go from your ISP, because they are in league with Satan... Then use a VPN and resolve through it.. Your just handing all your dns queries to exactly the the people that want them... Why and the F do you think they spun up such services in the first place.
Derelict gave the correct solution for routing your dns queries where you want to route them - and that is run it off pfsense so you can then easy policy route the traffic.