VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?
-
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@bcruze said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
to answer this question at least: Anyone out there have pfSense configured with both DNSSEC AND a public VPN service, like PIA, NordVPN, ExpressVPN, etc?
i run Airvpn and Mullvad. 2 different tunnels obviously
i use the DNS resolver to 9.9.9.9 and cloudfare. i set it up with these instructions: https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
then statically use Mullvad's server of 193.138.219.228 for the Mullvad tunnels. and they pass DNS leaks and DNSSEC.
Airvpn since you have to use 10.4.0.1 or the gateway for the Tunnel you connect to doesn't pass DNSSEC. but if fully passes all the leaks
you could probably use another provider for the DNSSSEC. but then you would not pass DNS leaks tests. since its "encrypted" it should not matter
this stuff is way over my head. but after a few years of tinkering my setup passes everything i want it to so i have left it alone
I can be a bit dense sometimes. I didn't see this the first time I read it. Rereading your post, you're saying you send your DNS queries THROUGH the VPN, then out the other side to Quad9 or Quad1? What's the latency on that? If it truly works, it kinda seems like you're doubling up (TLS) encryption on top of (VPN) encryption. I have no problem with that, except that I'd think the latency would be horrendous. No?
no i don't think i am that brilliant...
i have dhcp computers going over the default tunnel of Airvpn. it uses 9.9.9.9
then i created rules for certain computers to use Air and others to use Mullvad tunnel
then under services - dhcp server. i am using static dns settings for those clients to resolve over the mullvad DNS servers others using Airvpn DNS servers. so they pass DNS leak tests.
-
@bcruze said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@bcruze said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
to answer this question at least: Anyone out there have pfSense configured with both DNSSEC AND a public VPN service, like PIA, NordVPN, ExpressVPN, etc?
i run Airvpn and Mullvad. 2 different tunnels obviously
i use the DNS resolver to 9.9.9.9 and cloudfare. i set it up with these instructions: https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
then statically use Mullvad's server of 193.138.219.228 for the Mullvad tunnels. and they pass DNS leaks and DNSSEC.
Airvpn since you have to use 10.4.0.1 or the gateway for the Tunnel you connect to doesn't pass DNSSEC. but if fully passes all the leaks
you could probably use another provider for the DNSSSEC. but then you would not pass DNS leaks tests. since its "encrypted" it should not matter
this stuff is way over my head. but after a few years of tinkering my setup passes everything i want it to so i have left it alone
I can be a bit dense sometimes. I didn't see this the first time I read it. Rereading your post, you're saying you send your DNS queries THROUGH the VPN, then out the other side to Quad9 or Quad1? What's the latency on that? If it truly works, it kinda seems like you're doubling up (TLS) encryption on top of (VPN) encryption. I have no problem with that, except that I'd think the latency would be horrendous. No?
no i don't think i am that brilliant...
i have dhcp computers going over the default tunnel of Airvpn. it uses 9.9.9.9
then i created rules for certain computers to use Air and others to use Mullvad tunnel
then under services - dhcp server. i am using static dns settings for those clients to resolve over the mullvad DNS servers others using Airvpn DNS servers. so they pass DNS leak tests.
Oh, I see. I thought you meant you were passing the DNSSEC tests (and leak tests).
-
@derelict said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
Well, that's no different than visiting TLS web sites over the VPN. You have to encrypt the traffic or the VPN provider will spy on you just like your evil, evil ISP.
Well the ISPs blatantly admit they are collecting, logging and selling our each and every move. The (better) VPN services claim they don't and don't appear to be. Nor are the DNS over TLS providers (i.e. Quad1 or Quad4). If you know of any stories/articles where a VPN service handed over user logs, I'd be very interested. Same with the DNS over TLS services.
-
@talaverde With Quad9 and DNS over TLS, how do I verify the server reported in dnsleaktest.com is Quad9 server?
-
@gjaltemba said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@talaverde With Quad9 and DNS over TLS, how do I verify the server reported in dnsleaktest.com is Quad9 server?
When I do an extended test from https://www.dnsleaktest.com/ I get a WHOLE BUNCH of servers listed but they are all either named 'Cloudflare' or 'Woodynet', (which looks to be owned by Quad9, based on Internet searches.) If I ended up with a bunch of random names, I'd be concerned. It seems pretty obvious who they belong to.
-
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
When I do an extended test from https://www.dnsleaktest.com/ I get a WHOLE BUNCH of servers listed but they are all either named 'Cloudflare' or 'Woodynet', (which looks to be owned by Quad9, based on Internet searches.) If I ended up with a bunch of random names, I'd be concerned. It seems pretty obvious who they belong to.
Maybe I am not setup correctly. In my General Setup for DNS I have 9.9.9.9 and the gateway is my VPN.
In DNS Resolver I check
Enable DNSSEC support
Enable Forwarding Mode
Use SSL/TLS for outgoing DNS Queries to Forwarding ServersWhen I look in dnsleaktest.com it shows internet.exchange points as DNS. What is wrong?
-
How are you routing out the VPN? Policy Routing?
As I have already explained, you cannot policy route traffic generated on the firewall, which is why the single, best solution is a caching DNS resolver (or two or three) inside the firewall so the queries they make can be policy routed like the rest of the traffic. But nobody wants to make that effort.
Set your client to use 9.9.9.9 as its DNS server (either static or in DHCP for that inside network (you can only set it for one client with a static entry)) and you will see it works fine.
-
@derelict I tried routing out VPN in System->General Setup->DNS Server Settings. No good?

-
No. That has nothing to do with how traffic is routed.
-
@derelict said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
No. That has nothing to do with how traffic is routed.
But then what does setting the DNS Server gateway to my VPN interface do? I was thinking that it is the equivalent of setting Outgoing Network Interface in DNS Resolver.
-
That might work for you but you will break DNS for the whole firewall if the VPN is down.
Honestly, the best way to ensure you don't "leak" DNS is to tell your clients to use the outside DNS providers, policy route that traffic, and forget the on-firewall resolver exists.
Or, again, put an off-firewall DNS resolver together that can be policy routed like the client traffic on its way into LAN.
-
@derelict I am just starting to get your point but what I am getting at is when Quad9 goes via my VPN, dnsleaktest.com reports internet.exchange ip for DNS and not woodynet. Is this normal?
-
You'll have to post real, contrasting "leak test" results. I have no idea what you're trying to ask.
-
This post is deleted! -
I think this thread has strayed off topic. Most VPN services have instructions on how to set up pfSense with their VPN, if they are compatible. There are YouTube videos for PIA. Most of these questions would be answered in the instructions.
Although, I do admit my setup is contrary to what the VPN service recommends, hence, the thread.
I would make sure to follow the VPN service's instructions for pfSense. Make sure your results are as expected and you understand them. Only then, try using a different DNS configuration than recommended by the VPN, as I did here.
-
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
I'd like to add - Early in my testing, I observed the PIA DNS servers responded to TCP 853. So, I thought maybe they enabled DNS over TLS w/o announcing it. I tried using the PIA DNS servers and also pointing the pfSense DNS resolver to PIA. It didn't work. I could only get DNS over TLS to validate outside of a VPN tunnel (OpenVPN).
I still don't know whether VPN services simply choose not to support DNSSEC/TLS or that OpenVPN is incompatible with DNS over TLS. (If someone answered that above, sorry, I missed it.) I found one VPN service advertise that they support both 'VPN' and 'DNS over TLS'. However, it sounded more like 'either / or' -not- both. It just sounded like their DNS servers would support TLS, but it wasn't clear that it was through their VPN service (more like they inferred it was outside their VPN service).
I can see their point (the VPN services). The VPN tunnel makes TLS redundant. Then again, going back to the difference between DNS over TLS and DNSSEC, the VPN tunnel only 'encrypts' the DNS message, it doesn't validate it. Wouldn't that imply that the combination of DNS over TLS (encryption) -and- DNSSEC (validation) trumps VPN (encryption only)?
I could be off my rocker here but thought the conversation is worth having.
I've made a minor change to my configuration. I thought I may as well share it, to keep the explanation of my configuration accurate...
Until now, I configured my DNS Resolver to send DNS request out my WAN / Non-VPN connection. For some reason, I thought if I sent it through my VPN tunnel, it wouldn't work. I tried it and it works fine. So, my DNS requests:
- Use Quad9 & Quad1
- Use and validate to DNSSEC
- Use and validate DNS over TLS
- Are sent out through my VPN tunnel
I was reading there might be ways for an ISP to figure out your DNS requests even if you use DNS over TLS. (Just talking DNS here). Using the VPN tunnel, that won't happen. Another reason I (originally) sent the DNS request out via WAN / Non-VPN was to keep latency as low as possible on DNS requests. The VPN tunnel I'm using is the local PIA, which is the least obscure VPN connection, but a VPN tunnel, non the less. Since I'm using DNS over TLS, even the VPN won't know my DNS request anyway.
I'm feeling really good about this configuration.
-
@talaverde I gotta ask. Does dnsleaktest.com still show woodynet with quad9 and pia? For me it does not show woodynet nor pia but some internet.exchange point.
-
@gjaltemba said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@talaverde I gotta ask. Does dnsleaktest.com still show woodynet with quad9 and pia? For me it does not show woodynet nor pia but some internet.exchange point.
Hard to answer fully w/o a screenshot. dnsleaktest.com shows your DNS request hosts, not your VPN tunnel.
-
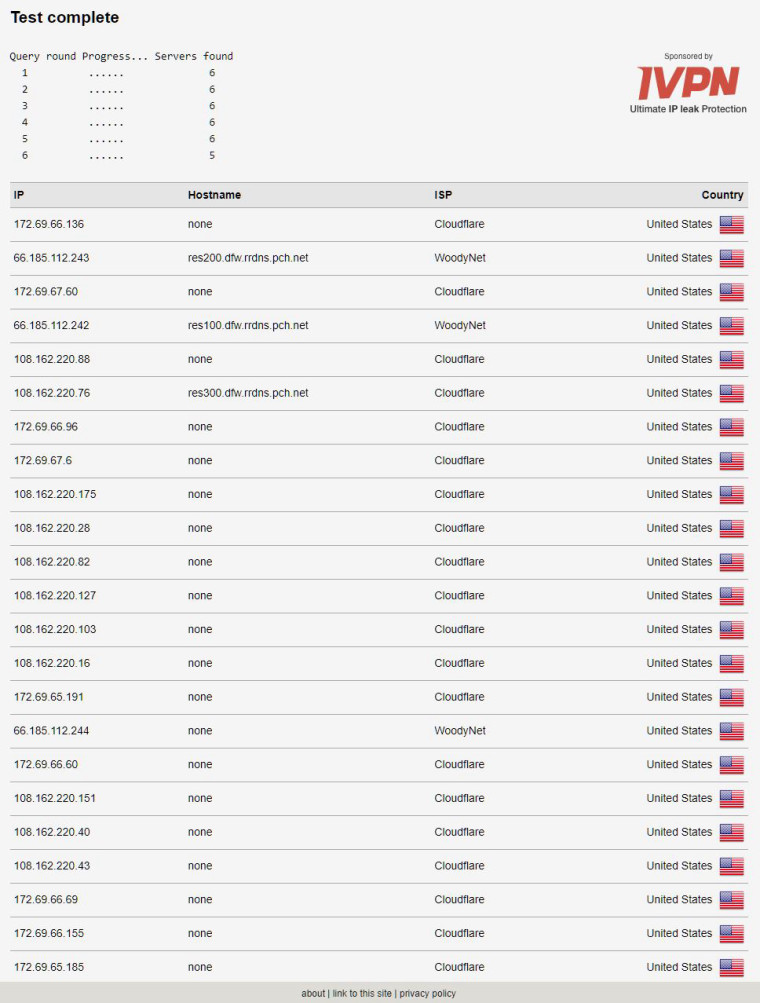
I had multiple users ask me what 'dnsleaktest' looked like when I have Quad9 and Cloudflare (Quad1) configured as my DNS servers. This is is what it looks like. OBVIOUSLY, this is not my IP address, nor my VPN's IP address. This is a list of DNS servers that respond to Quad9 or Quad1. (WoodyNet is obviously Quad1).
-
No one has contributed to this conversation for a while, so I feel like I'm talking with myself. Maybe no one else cares. A few wanted to know how to configure their VPN, but that didn't seem on topic.
At risk of sounding like I'm starting my own blog, I just want to mention this new configuration has been working GREAT!. I'm using multiple VPN providers with pfSense. At the same time, all my DNS requests are going to DNSSEC/TLS enabled DNS servers. No issues of leakage that I'm aware of. DNS requests are much quicker than using the VPN DNS servers. Spreading out the requests makes everything even more anonymous, IMO.
If anyone want more information on how I set this up (using TLS/DNSSEC, I'm open to questions, as I don't know of anyone else trying it this way.
(Setting up your VPN, there are many resources for that)