Sonos speakers and applications on different subnets (VLAN's)
-
I have been looking for a solution to have Sonos speakers and applications work across VLAN's using pfSense and, until now, haven't found a working solution.
I hope this thread helps you ~please keep in mind, this is a bit out of my wheelhouse~, if it does, + my reputation maybe drop a line here with feedback. Please bear in mind, I tried to keep it simple (KISS principle), so that even the "not so tech savy" might stay on board.
maybe drop a line here with feedback. Please bear in mind, I tried to keep it simple (KISS principle), so that even the "not so tech savy" might stay on board.ThreeOnly one"very"important note :
1. You will have to be able to use the CLI (command line interface) for instance use Putty. (~Edit~) As time passes it seems that I forgot about the "edit" possibilities in the GUI of pfSense, as @Vacquah pointed out (see below) and I quote; "I didn't have to use Putty at all. I logged into the pfsense GUI and executed all the commands via diagnostics --> command prompt. This includes copying the pimd conf file over to /var/etc/ and starting it after editing"and het did edit the config file ; "To edit the conf file at /var/etc/pimd.conf, I used diagnostics ---> file edit. You can browse to it. very easy."
2. (~Edit~) Great, that PIMD is now available for users on current 2.5.0 and 2.4.5 snapshots, so using the GUI it will be much easier to setup PIMD.
The use of the multicast routing daemon "pimd" is a package that's not in the pfSense manager, so this could be a risk and IMHO never use something in a firewall environment that's not vigorously tested by the developers of pfSense and certainly not in a corporate environment, so use this "at your own risk” ~~
3. It looks like Sonos will save/store the IP's of their devices, so it's best to quit thedaemon, once you can access the speakers (You'll have to test it).Before I explain the solution that I have found to work, first a bit of background.
Background
Sonos speakers and applications use multicast to find each other and unicast to execute commands. They broadcast there existence using 255.255.255.255 (unicast) and 239.255.255.250 (multicast). Normally these broadcasts/discovery stay on the same subnet and therefore, when you want to control the speakers using an application from a different subnet, they won't find each other. If they did found each other the communication goes via unicast.So what you want is to traverse Multicast 239.255.255.250 (SSPD) across subnets. Only the native igmpproxy (0.2.1) that comes with pfSense won't work (well, this accounts for version 0.2.1, maybe future versions will).
With igmpproxy I got the following error message:"The IGMP message was local multicast. Ignoring."I assume (as running igmpproxy in debug mode didn't reveal what this was) that it doesn't let the discovery (239.255.255.250 SSDP) traverse to the other subnet and hence application and speakers can't locate each other.
So after reading this thread https://forum.netgate.com/topic/138242/dlna-across-vlan-subnets-with-igmp-proxy-not-working ,I thought about trying to use "pimd".
PIMD Protocol Independent Multicast
PIM allows existing networks to route IP multicast, regardless of what unicast routing protocol is in use. Pimd is a lightweight standalone PIM-SM/SSM v2 multicast routing daemon.See:
https://freebsd.pkgs.org/11/freebsd-ports-quarterly-amd64/pimd-2.3.2.txz.html
https://github.com/troglobit/pimd
http://troglobit.com/projects/pimd/Installation
Install it from the Package Manager in the GUI as it is now available for users on current 2.5.0 and 2.4.5 snapshots and using the GUI it will be much easier to configurate PIMD.-.-.-.-.-.-.--.All below is not needed anymore, install it using the Package Manager and setup using the GUI--.-.-.-.-.-.-.
pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/quarterly/All/pimd-2.3.2.txz~~and thanks to @vacquah (read his post from 30 Juli) there is also a ARM version
pkg add http://pkg.freebsd.org/FreeBSD:11:armv6/quarterly/All/pimd-2.3.2.txzif for some reason you want to remove it, use:
pkg remove pimdAfter installation it is best to logout of pfSense and login again, so you can use pimd from anywhere (path)
I copied the default pimd.conf file to /var/etc/ (Keep in mind that with an update of pfSense it will be gone!!!)
cp /usr/local/etc/pimd.conf /var/etc/pimd.confand then edit it.
vi /var/etc/pimd.confIf you start pimd, by default, it will work on all interfaces and I don't think you want that, so first edit the config file before starting it.
Pimd uses a config file called pimd.conf and the only thing I changed is that I added the interfaces I don't want to use. By default PIM is activated on all interfaces. Use
phyint disablefor every device than you don't use.(If you don't know how, take a look at the igmpproxy.conf file (well if you, as I had configured it using the GUI from pfSense and tried using it ;) ) and copy them from the igmpproxy.conf, just remember to remove the "d" as pimd uses disable instead of disabled.)
Example
-.-.-.-.-.-.-.-.-.-.-.below part of pimd.conf-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.# By default PIM is activated on all interfaces. Use `phyint disable` # on interfaces where PIM should not run. You can also use the `-N, # --disable-vifs` command line option along with `enable` to get the # inverse behavior. # phyint pppoe0 disable phyint igb1.1001 disable phyint igb1.1002 disable phyint igb1.1003 disable phyint igb1.1004 disable phyint igb0 disable phyint igb1.1006 disable phyint igb1.1007 disable phyint igb1.1008 disable phyint igb1.1009 disable # The routing protocol admin distance (or metric preference per the RFC) # is used in PIM Assert elections to elect the forwarder of multicast. # Currently pimd cannot obtain distance and metric from the underlying # routing protocols, so a default distance may need to be configured per # interface. If left out, the default-route-distance is used for the # phyint. In PIM assert elections the router advertising the lowest # preference (distance) will be selected as forwarder (upstream router) # for that LAN. An admin distance of 101 should be sufficiently high so # that asserts from Cisco or GateD routers are prefered over poor-little # pimd. #-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.
So in my case (see above), pimd is not disabled on igb1.1005 and igb1.1010 and these are the VLAN's I want to use. 1005 holds the Sonos speakers and 1010 the Sonos applications.
Start pimd with -c is for the configuration file.
pimd -c /var/etc/pimd.confYou can see it running in the pfSense GUI goto status->system logs or type
topIf all goes well, it can take up to a 20-30 seconds before your can access the speakers.
Note: I noticed that once the Sonos application(s) have found the speakers the IP's are somehow "saved" or "stored" (btw You'll have to test this) and you can stop pimd, which seems best, because as I mentioned earlier it is better/safer to not use anything that has not been vigorously tested by the pfSense developers, as pimd is not an official package of pfSense (as far as I know)!
So quit pimd with
pimd -q-.-.-.-.-.-.--.All above is not needed anymore, install it using the Package Manager and setup using the GUI--.-.-.-.-.-.-.
pfSense firewall rules configuration
Below are the the rules that worked during the test. Currently, I am working on them to narrow them down, why else use a VLAN for Sonos and if you want I can post them ASAP.
and if you want I can post them ASAP.Ports can be found here https://support.sonos.com/s/article/688?language=en_US&utm_medium=firewall&utm_source=cr-care&utm_content=english-cr-care-firewall
Note 1: you don't have to enable the Allow IP options in the Advanced Options of the rules, as is sometimes mentioned using igmp proxy.
Note 2: below is reported that on Android devices "Allow IP options" in the Advanced Options of the firewall rules is needed to enable to make it work, so if you don't have success, please try to enable it.

I hope this helps, success.
Cheers Qinn
-
Hey Qinn,
I am trying to accomplish the same thing as detailed here
https://forums.lawrencesystems.com/t/inter-vlan-routing-multicast-help-pfsense-igmp-proxy-sonos/540/7
Did you get this working successfully ? -
@thewitten Yes, it does work. IGMPproxy and Avahi did not, as they don't seem to traverse the 239.255.255.250 (SSDP) across the VLAN's. So follow my "guide" above to get it working, from the tumbs up it seems that others have tried it successfully.
Now (time is a challenge at current) I am fine-tuning the firewall rules for the ports needed, as the current rules suggested in the guide above, are not much of security.
Cheers Qinn
-
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
I am fine-tuning the firewall rules for the ports needed, as the current rules suggested in the guide above, are not much of security.
Hi Qinn
Thanks for the detailed writeup and pointing me to this. So pimd replaces the need to have Avahi and igmpproxy? How stable is pimd daemon? Waiting to see what final rules you come up with for your vlans then I'd take a stab as well.
-
@vacquah said in Sonos speakers and applications on different subnets (VLAN's):
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
I am fine-tuning the firewall rules for the ports needed, as the current rules suggested in the guide above, are not much of security.
Hi Qinn
Thanks for the detailed writeup and pointing me to this. So pimd replaces the need to have Avahi and igmpproxy? How stable is pimd daemon? Waiting to see what final rules you come up with for your vlans then I'd take a stab as well.
Well, I have not replaced them. In my setup IGMPproxy is not running, but Avahi is. Avahi is used here to let iOS devices, that are in several VLAN's, to access the one VLAN that contains all printers. So Avahi is used to traverse Apples "Bonjour" service over these VLAN's to make printing possible to iPad's and iPhones that are on different VLAN's than were the bonjour printers are.
The beauty with the PIM deamon/iOS is that once the Sonos applications (iPad and iPhones) have located the Sonos speakers they "remember" there IP's, so somehow.
IP's addresses seem to be saved or stored by the Sonos applications (I can't check it, as the Sonos applications are closed source). But it's been 2 weeks since I have been running the PIM daemon (once and quit it) and I can still access the Sonos speakers from a different VLAN.So practically I have started the PIM daemon only once, then waited for the applications (that are in a different VLAN then the Sonos speakers) to get access to the speakers (all Sonos speakers are in one VLAN) and then quit the PIM daemon (as described in my guide above).
Only running PIMD once and then quiting it minimizes the theoretical risk of running an package that has not been tested by the pfSense developers.
Cheers Qinn
-
On the subject of security, my preliminary investigation suggests the following:
To let the Sonos speakers access the Sonos applications (iPad and iPhones), they need to be able to access the VLAN that holds the Sonos applications on UDP port 1901 and TCP ports 3400 and 3401.
To let the Sonos applications access the Sonos speakers they need to be able to access the VLAN that holds the Sonos speakers on TCP/UDP ports 1400 and 1443
It's is of course best practice to create these rules only for the ip's of Sonos speakers and the Sonos devices that hold the Sonos applications.
Sorry, time is a challenge at the moment, but in time I will place a detailed rule set.
Cheers Qinn
-
Btw to anyone, if you are happy with my guide and it helped you, maybe also vote on the thread below and add a comment, maybe the pfSense developers might consider to add the PIMD package to pfSense....
https://forum.netgate.com/topic/139352/pimd-a-lightweight-standalone-pim-sm-ssm-v2-multicast-routing-daemon
-
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
Btw to anyone, if you are happy with my guide and it helped you, maybe also vote on the thread below and add a comment, maybe the pfSense developers might consider to add the PIMD package to pfSense....
https://forum.netgate.com/topic/139352/pimd-a-lightweight-standalone-pim-sm-ssm-v2-multicast-routing-daemon@Qinn See comment by @jimp in this thread:
https://forum.netgate.com/topic/99211/multicast-with-pfsense
-
@vacquah said in Sonos speakers and applications on different subnets (VLAN's):
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
Btw to anyone, if you are happy with my guide and it helped you, maybe also vote on the thread below and add a comment, maybe the pfSense developers might consider to add the PIMD package to pfSense....
https://forum.netgate.com/topic/139352/pimd-a-lightweight-standalone-pim-sm-ssm-v2-multicast-routing-daemon@Qinn See comment by @jimp in this thread:
https://forum.netgate.com/topic/99211/multicast-with-pfsense
Thanks for pointing that one out to me, I was aware, but I thought it was useless to reply on a thread that old and at that time there were (as memory serves) more issues with IGMP proxy https://redmine.pfsense.org/issues/6099
btw did you got it working on your Sonos setup?Cheers Qinn
-
Hi Qinn I'll try to using your guide with pim to configure a similar problem in my network with google devices and Logitech Media server, I hope that this works.
Thanks.
Bull -
@bull said in Sonos speakers and applications on different subnets (VLAN's):
Hi Qinn I'll try to using your guide with pim to configure a similar problem in my network with google devices and Logitech Media server, I hope that this works.
Thanks.
Bulldid it work?
-
@qinn No, at the moment I don't have any positive results, it's quite frustrating, I don't know if I have a problem with netgear GS110TP switches or with pfsense I have it configured in a vmware environment with vlan(4096) and this may be blocking multicast to the router in vmware. I don't know how to continue I'm absolutely blocked, I've been trying and testing for a couple of weeks and starting over.
I need a rest, think so.
-
@bull said in Sonos speakers and applications on different subnets (VLAN's):
@qinn No, at the moment I don't have any positive results, it's quite frustrating, I don't know if I have a problem with netgear GS110TP switches or with pfsense I have it configured in a vmware environment with vlan(4096) and this may be blocking multicast to the router in vmware. I don't know how to continue I'm absolutely blocked, I've been trying and testing for a couple of weeks and starting over.
I need a rest, think so.
Did you turn the port to "promiscuous mode" in VMware for pfSense? That bit me in the butt once, a lesson I will not forget.
-
@tim-mcmanus In my setup(s) I do not use VMware at the moment, so I cannot advise. In theory the switch should not play a part, when it is in the private (RFC1918) subnet(s) and pfSense is controlling these subnets. So IGMP snooping should not be needed, the IGMP proxy or PIMD should do that part.
Have you checked what multicast is send (wireshark)? That's how I analyzed that 239.255.255.0 was used by Sonos and that native IGMP proxy used by pfSense did not traversed it over the subnets. -
@tim-mcmanus yes, promiscuous mode is enable on vmware NIC, anyway I haven't problems with unicast, I can ping and have conectivity across vlans inside and outside of the vmware. So I don't understand were the multicast cannot be routed
-
@qinn thank you, I'll try to disable IGMP on these switches later on, I let you know if it's work.
-
@bull said in Sonos speakers and applications on different subnets (VLAN's):
Hi Qinn I'll try to using your guide with pim to configure a similar problem in my network with google devices and Logitech Media server, I hope that this works.
Thanks.
BullBtw could you give a description of your setup?
-
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
Btw could you give a description of your setup?
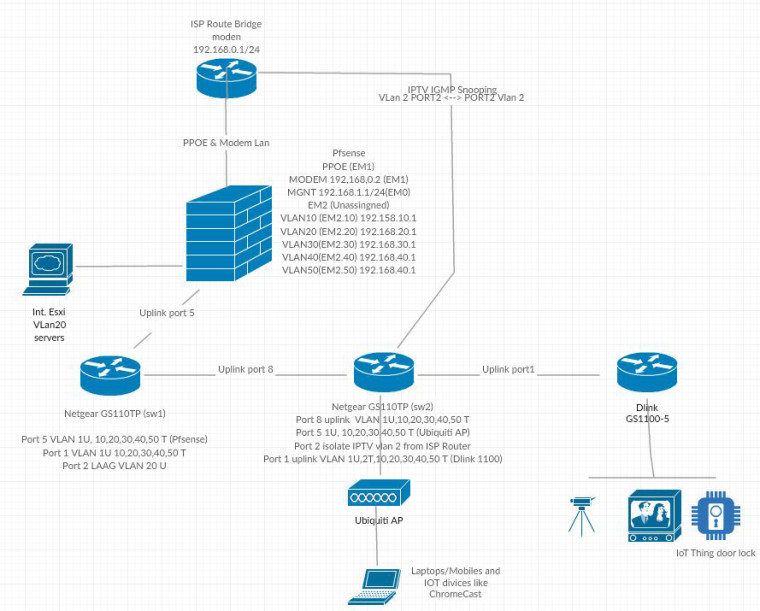
I have a ISP router on bridge mode conecting directly to a vmware nic (MODEM LAN 192.168.0.1/24) this interface works as PPPOE and route to modem network. (EM1)
the other nic i have created to vnic both in vlan 4095, the first one EM0 is de MGMT Lan (192.168.1.1/24) and the other vnic EM2 is configured as vlan 4095 and I've been created 5 port in the following tagged Vlan (10,20,30,40 and 50) from 192.168.10 to 50.1 subnet.
this nic is connected to a Netgear GPT110PT in port 6 vlan 10,20,30,40,50 as tagged an 1 untagged, I have a LAGG vlan 20 too connected to a NAS. from this switch is connected another one in port 1 vlan 10,20,30,40,50 as tagged an 1 untagged to port 8.
In port 5 from this second switch, I have a Ubiquiti AP with some wifi ssid configured with vlans 30,40,50, this port also configured with vlans as 10,20,30,40,50 as tagged an 1 untagged
both swicthes have IGMP Snooping enabled, configured IGMP vlan configuration for vlan 1,30,50 (testing at the moment) with querier enable and queriers enable and configured with vlan 1,30 and 50 pointing to each router ip subnet address 1,1 for vlan 1 30.1 for vlan 30...
May be this is a little confuse without a diagram but I don't have any software to have a grafical view of my network.
Many thanks
Bull -
@bull said in Sonos speakers and applications on different subnets (VLAN's):
I don't have any software to have a grafical view of my network.
There is plenty of free software or even just websites that would allow you to draw your network.
Here are 2 you can do it in pure ascii
https://textik.com/
http://asciiflow.com/Here is decent one
https://www.gliffy.com/
another
https://creately.com/lp/network-diagram-software-onlineActual download software
https://www.yworks.com/products/yed
http://dia-installer.de/Lets not forget the office type apps that are free, openoffice, LibreOffice that have drawing - even google draw ;)
Or you take out a crayon and and a napkin and then snap a photo of it with your phone!
-
@johnpoz said in Sonos speakers and applications on different subnets (VLAN's):
Or you take out a crayon and and a napkin and then snap a photo of it with your phone!
Thanks for the suggestions, I tried to do the best I know.
 W
W

