Suricata 4.1.2_2 Bug Fix Update -- Release Notes
-
I'm also receiving an error message in the WAN Rules of Suricata 4.1.2_1:
The following input errors were detected:
app-layer-events.rules seems to be missing!!! Please verify rules files have been downloaded, then go to the Categories tab and save the rule set again.I've forced an update and still get the message. Not sure why.
-
@newuser2pfsense said in Suricata 4.1.2_2 Bug Fix Update -- Release Notes:
I'm also receiving an error message in the WAN Rules of Suricata 4.1.2_1:
The following input errors were detected:
app-layer-events.rules seems to be missing!!! Please verify rules files have been downloaded, then go to the Categories tab and save the rule set again.I've forced an update and still get the message. Not sure why.
Check the directory /usr/local/share/suricata/rules for that file. It should be there, especially on AMD64 builds. Do you by chance have an SG-3100 appliance or some other non-Intel based CPU box?
-
Hi Bill...I checked the directory you listed and it's not there. I have a custom home built Intel based computer I'm using for pfSense.
-
@newuser2pfsense said in Suricata 4.1.2_2 Bug Fix Update -- Release Notes:
Hi Bill...I checked the directory you listed and it's not there. I have a custom home built Intel based computer I'm using for pfSense.
Let's try a totally clean install of Suricata.
-
Be sure "save settings" is checked on the GLOBAL SETTINGS tab.
-
Next, go to SYSTEM > PACKAGE MANAGER Installed Packages and delete the package from the firewall.
-
When the removal process completes, open a firewall CLI session (shell prompt) and search for any of the following directories:
/usr/local/pkg/suricata
/usr/local/etc/suricata
/usr/local/www/suricata
/usr/local/share/suricata -
Remove any directories and their content you see from the list above with this command:
rm -rf /usr/local/xxx/suricata(where xxx is replaced by the directory name from the list above)
- Return to the SYSTEM > PACKAGE MANAGER page and install Suricata again from the Available Packages tab. Wait for the process to fully complete before leaving the page!
Report back the results and/or any error messages if it does not work then.
-
-
Bill...I followed your instructions. It looks like I'm back in business. Thanks for your support!
-
@newuser2pfsense said in Suricata 4.1.2_2 Bug Fix Update -- Release Notes:
Bill...I followed your instructions. It looks like I'm back in business. Thanks for your support!
How did you install the package upgrade originally? Did you follow the instructions to completely remove Suricata and then install it again, or did you just click the package re-install icon?
-
I actually just clicked the package re-install icon. I guess from now on I'll use your instructions before upgrading to the newest version.
-
@newuser2pfsense said in Suricata 4.1.2_2 Bug Fix Update -- Release Notes:
I actually just clicked the package re-install icon. I guess from now on I'll use your instructions before upgrading to the newest version.
For this update, following the instructions was crucial because some PHP files had to be updated that pfSense will "cache". Thus clicking the "reinstall" icon will cause pfSense to use the "old" cached versions of these critical files. This causes some of the new settings that are required to be updated to get missed. Removing the package dumps the PHP cache, so during installation the new properly updated files get executed and those files will update your saved configuration.
In your case, by not dumping the package first, those cached files were reused during some of the installation and critical parts of your saved configuration did not get updated.
-
@bmeeks Just got the update, installed it:
(
This is on FireFox 64.0.2 (64bit). -
@digdug3 said in Suricata 4.1.2_2 Bug Fix Update -- Release Notes:
@bmeeks Just got the update, installed it:
(
This is on FireFox 64.0.2 (64bit).Hmm...might be an artifact (syntax problem, really) that results from the rule category being managed by SID MGMT. I will test that and post a fix. There are some tests in the logic for various conditions and an appropriate message is loaded into that variable based on the tests. The code is supposed to display the contents of the variable instead of its name, so I will need to see where I screwed up the syntax. Probably missed a quotation mark someplace ...
 .
. -
@bmeeks Not really a problem, you can click it and it also goes to the correct ruleset. Just cosmetic.
-
@digdug3 said in Suricata 4.1.2_2 Bug Fix Update -- Release Notes:
@bmeeks Not really a problem, you can click it and it also goes to the correct ruleset. Just cosmetic.
Yes, it is just cosmetic; but I will get it fixed nonetheless. May wait a day or two to see if any other issues surface, and then put together a package update.
-
Hey Bill...after re-installing Suricata per your instructions yesterday, I just downloaded the alerts to find the tar.gz file is 1.1 MB in size with only one 240.5 kB file inside. There should have been multiple files around 500 kB in size in the tar.gz file. It looks like Suricata is not using the Auto Log Management that I have set to default. Have you seen this by chance?
-
@newuser2pfsense said in Suricata 4.1.2_2 Bug Fix Update -- Release Notes:
Hey Bill...after re-installing Suricata per your instructions yesterday, I just downloaded the alerts to find the tar.gz file is 1.1 MB in size with only one 240.5 kB file inside. There should have been multiple files around 500 kB in size in the tar.gz file. It looks like Suricata is not using the Auto Log Management that I have set to default. Have you seen this by chance?
How many files and of what size are located in the interface's log directory? You will find all the logs in sub-directories (one per interface) under /var/log/suricata. I tested downloading a tarball gzip file of alerts during the last code update, but I don't recall if there were multiple alert files in the sub-directory at the time.
-
I have Suricata pointed to only one interface at present. In the /var/log/suricata directory, there is a suricata_rules_update.log file that's 3.7 KB in size and one directory named suricatat_igb715464. In the suricatat_igb715464 directory, there is only one alerts.log file which is the name of the file in the downloaded tar.gz file that has a size of 242.8 KB. Interestingly, there is only one http.log file, multiple stats.log files, one suricata.log file, and two tls.log files.
-
@newuser2pfsense said in Suricata 4.1.2_2 Bug Fix Update -- Release Notes:
I have Suricata pointed to only one interface at present. In the /var/log/suricata directory, there is a suricata_rules_update.log file that's 3.7 KB in size and one directory named suricatat_igb715464. In the suricatat_igb715464 directory, there is only one alerts.log file which is the name of the file in the downloaded tar.gz file that has a size of 242.8 KB. Interestingly, there is only one http.log file, multiple stats.log files, one suricata.log file, and two tls.log files.
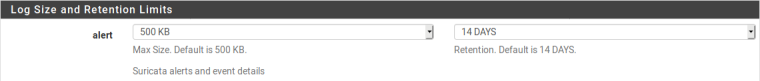
That all sounds fine. Your alerts log is 243 KB in size. What value is set on the LOGS MGMT tab for alerts? If it is less than 500 KB (which I think is the default, but I can't recall for sure), then everything is fine.
igb7 refers to your physical NIC and the number 15464 is a psuedo-random GUID generated by the Suricata GUI code to uniquely identify the interface.
-
I get a boat load of alerts on the interface. The alerts are set to default as seen below. With only one file in the downloaded tar.gz file, I don't think it's fine at the moment. Before the update I would get a Suricata log about every 10 to 15 minutes at around 500 KB in size. There were hundreds and into the 14 day period, there were thousands.
-
@newuser2pfsense
What kind of traffic are you inspecting to generate that much in log data? Are you running this on as a ISP or some very large corporate network?Are you missing alerts on the ALERTS tab itself? The alerts displayed on that tab come directly from reading the alerts.log file in the interface sub-directory. If you have a single file, and that file is below the 500 KB limit, then no log rotation is going to be triggered. If you had rotated logs, they should show up as alerts.log.timestamp where timestamp is the time of day when the log was rotated. Could the aging setting have recently cleared the directory?
-
In the WAN Categories, I have 17 ET Open Rules checked and I have 23 Snort Text Rules checked. I'm just running a home network but I'm in a high density area where the bandwidth is shared. It's awful. I'm running Suricata in Inline IPS mode. The Alerts lists everything in red as far as I can see which means the rule is forced to drop. You are correct about the log rotation, however, it appears I'm getting the same number of alerts now as I have before upgrading but I'm not receiving the rotated logs at all where before upgrading I would get tons of rotated logs just as you showed with the timestamp. In the Logs Mgmt, I have check marked Remove Suricata Logs On Package Uninstall. When I initially upgraded before following your instructions, I only had one rotated log file which I thought was odd. When I followed your installation instructions, I don't even have one rotated log file. The directory was cleared as far as I can tell. Before I upgraded, I had so many rotated logs over a 14 day period that I had to write a Python program to concatenate and dedupe the rotated logs in order to see which particular rules were hitting my WAN. To give you an idea, I currently have 245 dropped rules.
-
Several comments:
-
When you check the box "Remove Suricata Logs on Package Uninstall", that means on each upgrade all of your Suricata log files are deleted (including any previously rotated ones). That box is unchecked by default for this reason. So when you did your upgrade to the latest version, all of your old log files were deleted.
-
With only 40 rules enabled I cannot imagine how you would get so many alerts to fill that many log files in your previous version. You have to be getting a ton of false positives and noise. Otherwise, you would not be able to get to anywhere from your network.
-
If you are a home user, then you should run Suricata on the LAN and not the WAN. By default, pfSense will drop all unsolicited traffic on the WAN already. Suricata does nothing to enhance security much on the WAN in a home network setup. It also means Suricata will see a bunch of garbage and log it all that your firewall is going to drop anyway.
-
Put Suricata on your LAN instead of your WAN for home networks.
-