Route some IP's/traffic through pfsense gateway
-
Hi All,
Looking for some help, we have staff that connect to our openvpn to access internal resources. This is a split tunnel the gateway is not redirected.
Some staff need access to external servers via remote desktop, which is locked down to our IP address/Gateway on our pfsense router.How can I create a list of IP's staff can access via openvpn thats redirected through the pfsense gateway while keeping the gateway not redirected for all other traffic.
Many THanks
Steve
-
Read your post twice. As I understand it now, that concerns only road-warrior clients.
So to route the client traffic to the concerned external servers over the vpn, add all these server to your access server settings to "Local Network/s" in CIDR notation. E.g. 1.1.1.1/32
Add on outbound NAT rule for your clients (Firewall > NAT > Outbound). If it is in automatic mode switch to hybrid at first.
Then add a rule:
interface: WAN
source: <the access server tunnel network>
dest: any
tranlation: interface addressIf you have resticted the vpn client access, ensure to add a firewall rule to allow the access.
-
I'm afraid you can't do it with one OpenVPN tunnel. You can create second OpenVPN tunnel or use IPsec RA with Pre-Shared Keys option which allows you to assign different IP-subnets to different clients and then aplly different firewall rules for each of them:
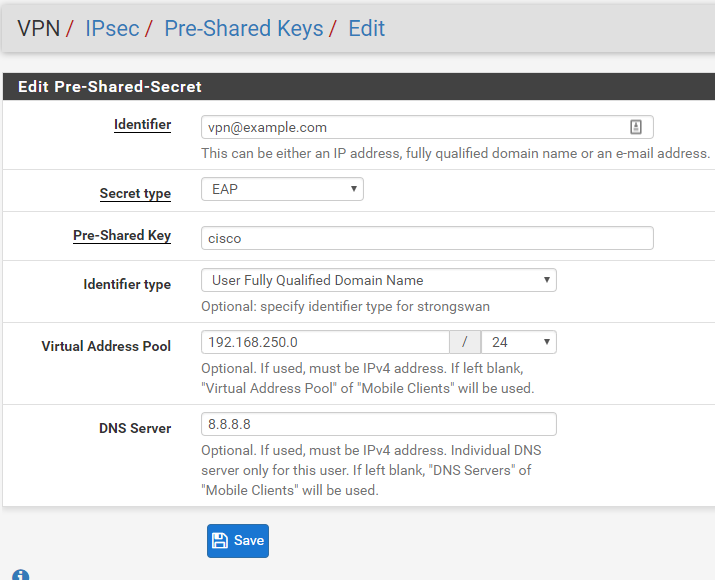
- https://www.netgate.com/docs/pfsense/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html#set-up-mobile-ipsec-for-ikev2-eap-mschapv2
-
@viragomann do you have a working setup where you could post some screen shots of the config. Thanks
-
@stevetoza
Read your post twice and edited my answer above. -
@viragomann Thanks very much, that works perfectly :)