VPN for specific clients + kill switch
-
Good day,
I'm new with pfsense, but not firewalls in general. I'm attempting to allow specific hosts VPN only access to the internet, while the remainder of hosts continue to use the default gateway to the ISP. Currently I have an alias with the list of hosts, and a LAN Firewall Rule sending all traffic onto the VPN. This is successful.
However, if the VPN disconnects all traffic from the VPN_hosts switches back to the default gateway.
I've attempted adding the following rules:
a floating rule that blocks all traffic from the VPN_hosts to the WAN.
a WAN rule that blocks all traffic from the VPN_hosts to the WAN
a LAN rule below the VPN allow rule that blocks traffic from the VPN_hosts to any WAN netI'm a bit at a loss at the moment as to why this isn't working.
-
OpenVPN Kill Switch: https://forum.netgate.com/topic/67692/openvpn-kill-switch/6
-Rico
-
@zxarr
Hey
You can try to implement this scheme
We assume that the tunnel is for OpenVPN
firewall/rules/lan / pbr rule for vpn_hosts
Add tag vpn_hosts
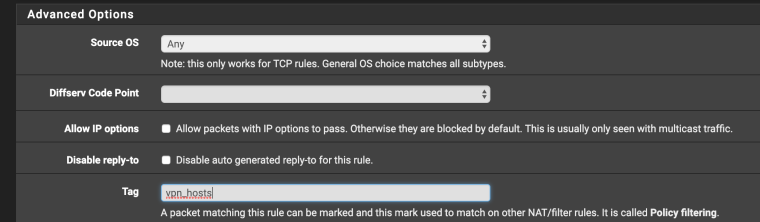
save/exit
firewall/rules/floating
Firewall > Rules, Floating tabAction: Reject or Block
Disabled: unchecked
Quick: checked
Interface: WAN
Direction: out
TCP/IP Version: IPv4
Protocol: any
Source: any
Destination: any
Destination port range: any
Advanced options
Tagged: vpn_hostsThus , all traffic tagged vpn_hosts through the openvpn interface leaves no restriction .
and if the traffic tagged vpn_hosts gets to the wan interface, it is blocked -
@konstanti Looks like tagging the traffic did the trick. Disconnecting from OpenVPN kills internet connectivity to the hosts in VPN_hosts alias, while all other hosts have normal ISP connection.
Thanks!!
-
Hello.
When I build tunnel in tunnel with OpenVPN clients
For example:
VPN1 (Remote IP 10.10.10.10) Remote Network(s): 11.11.11.11/32
VPN2 (Remote IP 11.11.11.11) Remote Network(s): 12.12.12.12/32
VPN3 (Remote IP 12.12.12.12)How do I set up a KillSwitch that first lets VPN1 through, then VPN2 and finally VPN3?
Greetings
John