OpenVPN to Target LAN resource Firewall Rule Set up
-
Hello all,
I successfully added an OpenVPN user through the wizard on pfSense.
I did the certificates authority and certificate server set up. I selected for server mode Remote Access(SSL/TLS + User Auth) as these are external WAN clients operating remotely in different time zones.
I exported the client package executable.
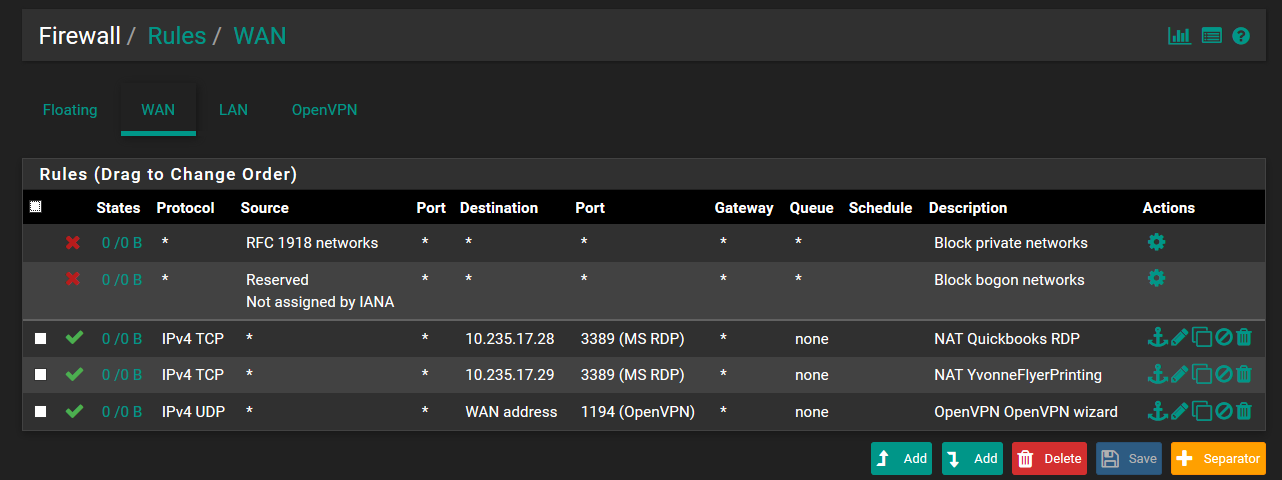
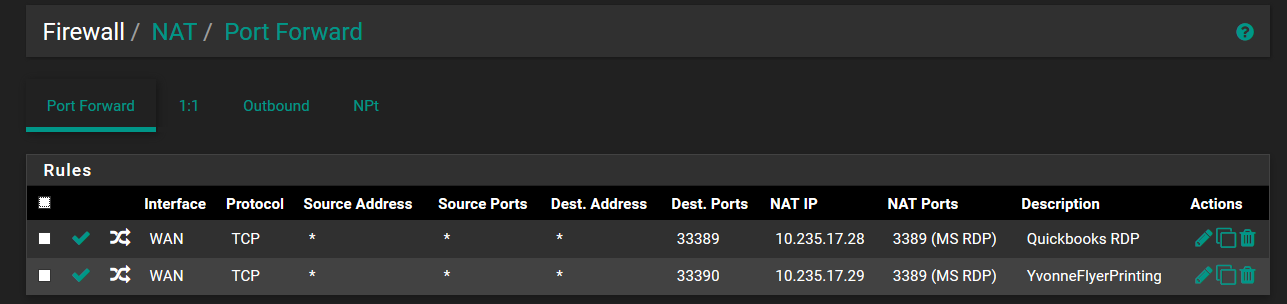
My question is in order to get LAN target resource .28 and .29 off of MS RDP and make them OpenVPN tunnel destinations I must set up the Firewall Rule correct?
Do I have to configure anything in NAT as well?
This is my first time working with VPN so I want to ensure I do this correctly.
Here is the Firewall scheme I have currently:
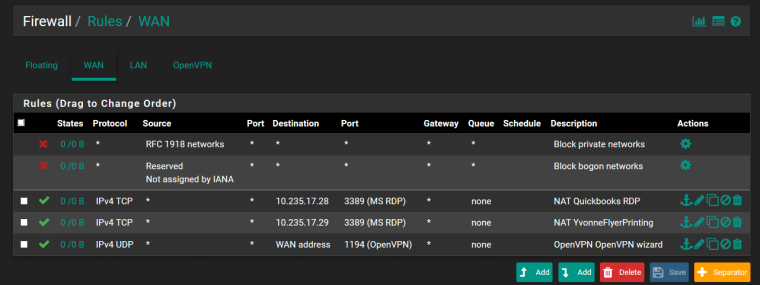
I also get a TLS handshake failure when trying to connect the VPN from external network device with the current client executable so I must troubleshoot that as well.
Thank you.
-
@virtuousmight
Hey
Hosts. 28 and .29 are in a lan network ? -
Konstanti,
Yes IP ...28 and .....29 are computers that have been DHCP static mapped on our local area network.
So previously the two employees were getting into our LAN remotely via MS RDP, but that is not optimal since it is not secure.
So I am trying to get them to connect to those to destination computers in our LAN with OpenVPN instead.
-
@virtuousmight
https://www.netgate.com/resources/videos/openvpn-as-a-wan-on-pfsense.html
https://www.netgate.com/docs/pfsense/vpn/openvpn/openvpn-remote-access-server.html -
@VirtuousMight
Right decision
Look for links, there are answers to all questions
How to configure remote access using OPENVPN
All errors can be viewed /Status / system logs/openvpn -
Hmmm double posting?

https://forum.netgate.com/topic/139808/openvpn-direct-connection-to-static-ip-desktop-mac-address-Rico
-
Very much not well-versed in this so trying to be more specific and post in the OpenVpN board and not general discussion.
-
I've posted right in the other thread and then saw this one here.
Maybe my posting there can help you...check it out.-Rico