How to block all but a few outbound ports for alias
-
Hi,
Even though I have done this with other routers I just cannot figure out how to achieve this in pfSense.
At home I have a few IP cams, I want them to have outbound access on TCP 25, 53, 123 and everything else blocked.
Can someone please point me to documentation which explains how to create such a rule/ rules or give me some tips?
Thanks
-
@chrisbo you could create an alias containing all ip cam ip addresses. Then use this alias in a firewall rule to allow all allowed ports (again, create an alias containing all ports). Below of this rule you create a rule blocking any for the ip cam alias.
Rules are processed from top to bottom.
-
Thank you for your reply.
That's the way I thought it should be but whenever I enable the rule to block any for the IP cam alias, all IP cam traffic is blocked. Just above it, I have an allow rule for the same IP alias which permits to any destination using a port alias containing TCP 25, 53, 123.
For testing I'm using a laptop with an IP in the scope used for my IP cams. With the deny rule off I can browse on TCP 80 or 443 and use nslookup but when the deny rule is enabled the laptop has no outbound access.
I also created another permit rule only for the laptop IP and only port 25, which is placed just above the deny rule but still everything is blocked.
Seems to be ignoring my permit rules before the deny rule.
-
post your rules and we can discuss.. Rules are evaluated top down, first rule to trigger wins and no other rules are evaluated.
-
@johnpoz Thanks, below are the two firewall rules which I expected to allow TCP 53 then block all. The test laptop is 192.168.2.248, the alias IP_Cams is 192.168.2.245 - 254. Is that enough info or do I need to post more like full rules and alias?
<rule>
<id></id>
<tracker>1548431689</tracker>
<type>pass</type>
<interface>lan</interface>
<ipprotocol>inet</ipprotocol>
<tag></tag>
<tagged></tagged>
<max></max>
<max-src-nodes></max-src-nodes>
<max-src-conn></max-src-conn>
<max-src-states></max-src-states>
<statetimeout></statetimeout>
<statetype><![CDATA[keep state]]></statetype>
<os></os>
<protocol>tcp</protocol>
<source>
<address>192.168.2.248</address>
</source>
<destination>
<any></any>
<port>53</port>
</destination>
<log></log>
<descr></descr>
<updated>
<time>1548431689</time>
<username>admin@192.168.2.22 (Local Database)</username>
</updated>
<created>
<time>1548431689</time>
<username>admin@192.168.2.22 (Local Database)</username>
</created>
</rule>
<rule>
<id></id>
<tracker>1548402225</tracker>
<type>reject</type>
<interface>lan</interface>
<ipprotocol>inet</ipprotocol>
<tag></tag>
<tagged></tagged>
<max></max>
<max-src-nodes></max-src-nodes>
<max-src-conn></max-src-conn>
<max-src-states></max-src-states>
<statetimeout></statetimeout>
<statetype><![CDATA[keep state]]></statetype>
<os></os>
<source>
<address>IP_Cams</address>
</source>
<destination>
<any></any>
</destination>
<descr></descr>
<created>
<time>1548402225</time>
<username>admin@192.168.2.22 (Local Database)</username>
</created>
<updated>
<time>1548420963</time>
<username>admin@192.168.2.22 (Local Database)</username>
</updated>
</rule> -
Dude post up screenshot of your rules.. Need to SEE ALL rules on your interface so can see the order you have them in, etc..
example here is one of my vlans
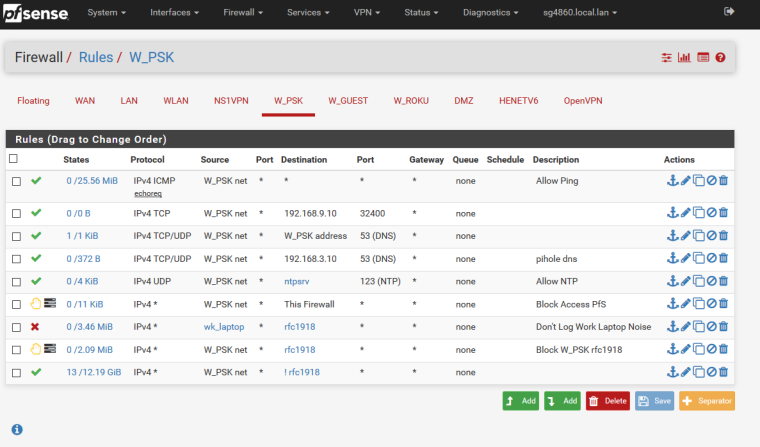
-
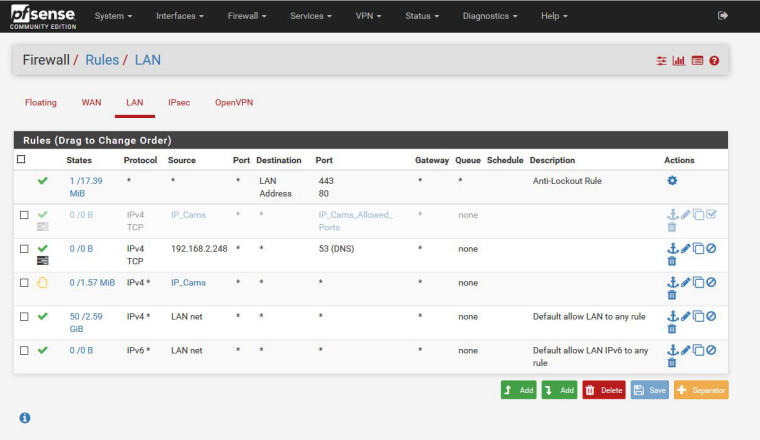
@johnpoz Thanks again, here it is:
-
You need UDP for DNS, not just TCP.
-
@kom OMG, I should know that.... always forgetting.... Thanks so much guys for your time and help!!
-
What is this IP 192.168.2.248? Why are you only allowing it to talk dns on tcp?
I don't see any rules for the 25 and 123 you mentioned. Also you are blocking all IP_cams to anywhere. Other than your antilockout.. Keep in mind when you create a block rule that you have to make sure you kill any active states - once a state is created it will be used to allow traffic. So you either have to wait for the state to expire or reset it for block rules to work, etc.
-
I did something stupid, I based all my testing using nslookup on a laptop (192.168.2.248) but did not include UDP 53 in the pass rule.
To simplify the rules for myself I disabled the rule which included the IP alias for TCP 25, 53 and 123 and I created a new rule for only TCP 53 for 192.168.2.248.
Now I have edited the allow rule for TCP/UDP and things work as expected.
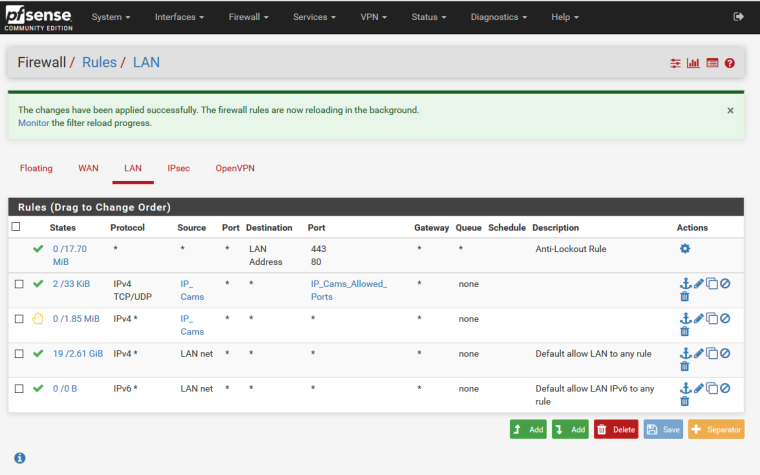
Thanks very much for the info on active states and for helping with my mistake.