NordVPN Client only for specific hosts
-
Hello all,
I managed to install NordVPN in pfsense (2.4.5-DEVELOPMENT) following this tutorial: https://nordvpn.com/fr/tutorials/pfsense/pfsense-openvpn/
My problem is all my network is passing trough the VPN, but I don't want that.
I've create an Aliase with the hosts I want to be in the VPN connection.Can you help me please?
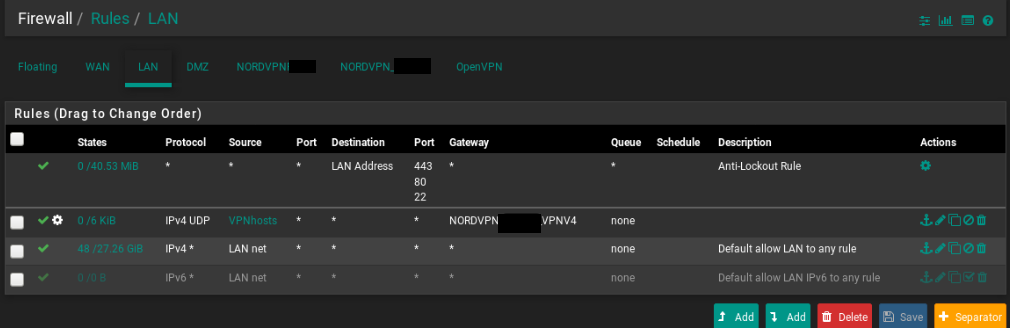
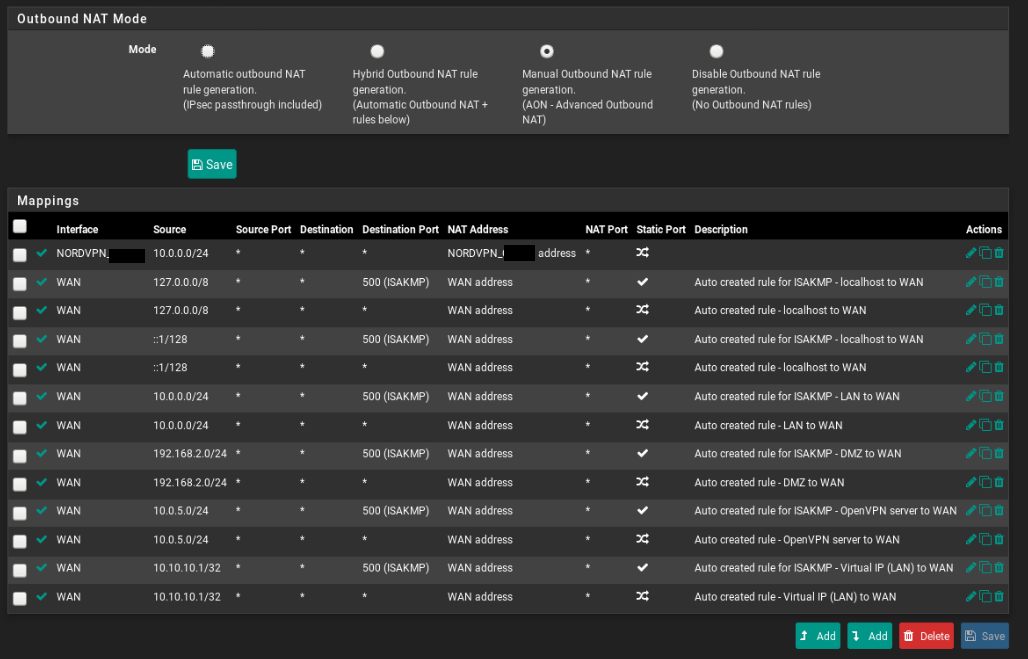
Here my settings:
If you need something else please tell me.
Thanks for your help. -
Why are you only policy based routing UDP ?
Change the protocol to ANY.
Also for testing use an IP address for the source, does it then work ?
-
Changed to Any in the rules and only the host ip, still the same, all my network is passing through the VPN.
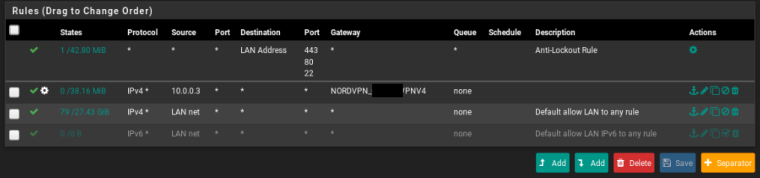
-
@luckyzor said in NordVPN Client only for specific hosts:
I've create an Aliase with the hosts I want to be in the VPN connection.
Can you help me please?
Here my settings:Tried changing the gateway in the two rules below the NORD VPN rule to be the WAN gateway ?
Is the state count going up on the two rules below the NORD VPN ?
-
Is the state count going up on the two rules below the NORD VPN ? - what do you mean with this?
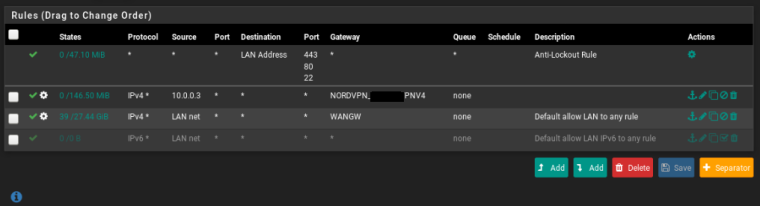
Like that it worked. Should I change the gateway in another rule?
I have this problem too:
VPN host - I can't access my DMZ zone (I have one VM in there) when I try to ssh to this VM I got access denied.
Other host, I can't access the VM and there is no internet (can't ping 8.8.8.8 for example) -
@luckyzor said in NordVPN Client only for specific hosts:
Like that it worked. Should I change the gateway in another rule?
You need to establish which firewall rules are being matched, add logging to the other two rules and then look in the logs.
The rule at the bottom is IPv6, if you don't use IPv6 nothing will hit the rule.
Maybe then do packet captures on the DMZ interface and see if traffic is even hitting the DMZ.
-
I'm struggling how to do it.
Do you have any hint, how to do it?I turned on the log in the 2nd rule and why I tried to ssh to the VM in the DMZ and I can't find anything in the log, maybe i'm doing something wrong

-
@luckyzor said in NordVPN Client only for specific hosts:
I'm struggling how to do it.
Do you have any hint, how to do it?I turned on the log in the 2nd rule and why I tried to ssh to the VM in the DMZ and I can't find anything in the log, maybe i'm doing something wrong

The NordVPN rule or the rule below it ?
I've never done this but as I said previously you need to figure out what rule it hits and then go from there.
If you hold your mouse over the X or tick in Status System -> LogsFirewall -> Normal View you'll see the rule numbers, ditto over states in the firewall rules page.
-
Well, with logs I didn't find anything.
With some testes I have this:
Disabled OpenVPN client: VM in DMZ - OK (have internet ping 8.8.8.8 / I can SSH from LAN interface)
Enable OpenVPN client: Can't ping 8.8.8.8 / but I can SSH if - NO specific gateway which means all my network is in the VPN :
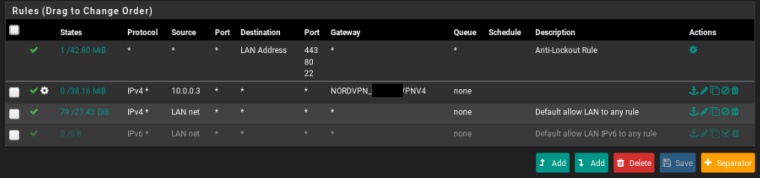
If I put the gateway like this:
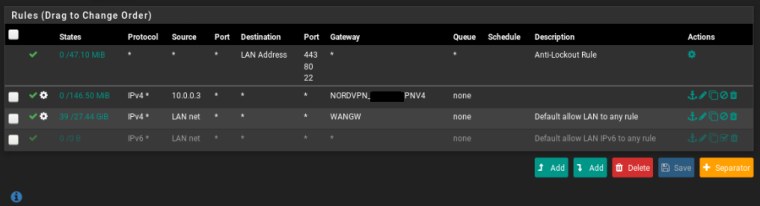
Only the host 10.0.0.3 have VPN (which is my intention) but I can no longer ssh my VM in DMZ / no internet in the VM DMZ.
I'm lost, because I don't know what to do

edit: the WANGW is the IP of my ISP modem :/
-
The guide you followed does not allow for policy routing; it assumes you want all traffic to go through the VPN. If you want to use policy routing, go into your VPN client configuration and check the box for "Don't Pull Routes". When that box is checked, a static route is pulled that directs all your traffic through the VPN. You don't want that; you want no traffic to go through the VPN unless you have a firewall rule that directs it to.
Also note that the guide directs all DNS requests through the VPN. Generally, that shouldn't be a problem. But you can override it for specific clients on your LAN using static DHCP mappings. For example, you could use a static mapping to ensure that a specific client always gets the IP 192.168.1.10 and always gets assigned Google's DNS servers (8.8.8.8 and 4.4.4.4) instead of being assigned the pfSense box itself (192.168.1.1) as its DNS server.
-
@thenarc WOW it's solved ;) thank you :D
One last question, how can I have access to my DMZ VM with a host in the VPN?
example:
[root@vmservers ~]# ping 192.168.2.2
PING 192.168.2.2 (192.168.2.2) 56(84) bytes of data.
From 10.8.0.1 icmp_seq=1 Destination Port Unreachable
From 10.8.0.1 icmp_seq=2 Destination Port Unreachable
From 10.8.0.1 icmp_seq=3 Destination Port Unreachable10.8.0.1 is the ip of the VPN Client
Thank you
-
Glad to hear that worked. I may be of less use with respect to a DMX though; I've never configured one on pfSense. But it's an OPT interface, right? Did you set up the appropriate policy routing firewall rules for it? How do you want it to behave?
-
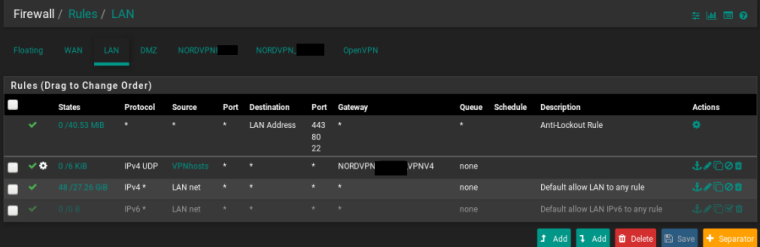
yes the DMZ is an OPT interface.
This are the rules in DMZ.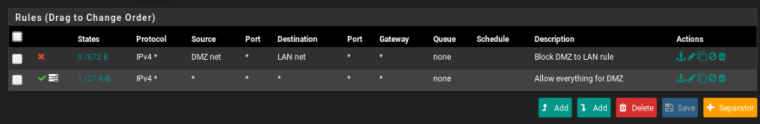
Rules in the VPN interface:
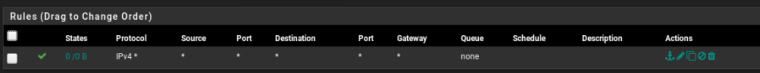
the problem is the connection between the hosts in the VPN and the DMZ. (diferent subnet) / I can't even ping my ISP modem with the host in the VPN.
hosts in the VPN with hosts not in the VPN - OK (same subnet)
thanks for your help :)
-
When you say "hosts in the VPN", do you mean hosts in the LAN for which you have the gateway set to your VPN using policy routing firewall rules? As you say, the DMZ and your LAN are two separate networks, and the block rule you made explicitly prohibits any hosts on the DMZ from communicating with hosts on the LAN. Typically, this is what you would want, I believe. Are you saying that it's not what you want? Or that you want hosts on the DMZ to also be routed through your VPN? I'm still not clear on the goal, but if the firewall rules are configured to allow DMZ hosts to communicate with LAN hosts, then I don't believe it would be a DMZ at all, right?
-
Yes, I want to be able to access all my subnet's (DMZ, ISP subnet ) with the hosts (in Lan interface) who have the gateway NordVPN
For now, the hosts with the gateway NordVPN only have access to there subnet (10.0.0.0)The hosts in the DMZ will not have the NordVPN gateway and I don't want them to have access to anything else then WAN interface
thanks for your help
-
These resources may be useful:
https://www.slideshare.net/NetgateUSA/creating-a-dmz-pfsense-hangout-january-2016
https://www.netgate.com/docs/pfsense/config/example-basic-configuration.html
However, I believe that allowing access to the DMZ from the LAN is breaking the whole idea of the DMZ. As I said, I've never configured one myself, but I think generally the whole purpose is to have complete isolation from the LAN.
-
But the DMZ is isolated. The DMZ only have access to WAN, nothing more than that.
I have access to DMZ from LAN, for example if I want to update my website, etc...
-
@thenarc said in NordVPN Client only for specific hosts:
However, I believe that allowing access to the DMZ from the LAN is breaking the whole idea of the DMZ.
NO... So you allow the whole public internet to access a DMZ... But you think accessing it from the LAN would be bad?
You can even allow access from DMZ into lan with specific pinholes and understanding, etc. Its best to not do that - but its done all the time.
All of the guides from these sites want any and all traffic to go to them... This is NOT what normal people would want... So you DO NOT PULL routes, and then just policy route out the vpn what you want to use the vpn.
-
Okay, and you're saying your LAN-to-DMZ access is already working, or that's what you're trying to get working? Because if it's not working, I think you'll want to add a firewall rule on your LAN interface allowing access to the DMZ subnet via the default gateway.
-
@thenarc said in NordVPN Client only for specific hosts:
DMZ subnet via the default gateway.
No you would not call out a gateway - this is where you run into problems.. You just allow the traffic you want and do not call out a gateway - since now your policy routing, and you wouldn't be going out your wan or vpn to get to another segment off pfsense.
You just allow the rule above where you force out traffic via a policy route "setting gateway" in the rule.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.