NordVPN Client only for specific hosts
-
My LAN to DMZ is working, but only with hosts without the NordVPN gateway.
I wanted to know if it's possible to connect to others subnets (DMZ, ISP modem subnet) with hosta who have NordVPN gateway.
-
@johnpoz You're correct, but in my defense the terminology on the firewall rule config is confusing:
"Leave as 'default' to use the system routing table. Or choose a gateway to utilize policy based routing."So you set the Gateway setting to Default, but that doesn't mean it uses the default gateway.
-
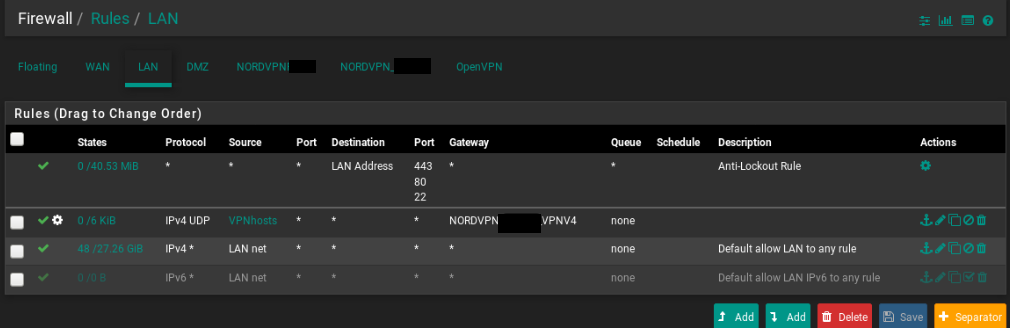
@luckyzor You need to create a LAN firewall rule above your existing rule that routes hosts through the NordVPN gateway. Per johnpoz's post, that rule should have the source set to any (assuming you want any LAN host to be able to access the DMZ), the destination set to the DMZ subnet, and the Gateway setting left at Default.
-
So only have to pull down the nordvpn rule for that... If I'm understanding well.
-
@luckyzor You mean you have an existing LAN-to-DMZ allow rule but it's currently below your NordVPN rule? If so, then yes, simply re-ordering them may be all you need. If that doesn't work, post a screen shot of your LAN firewall rules.
-
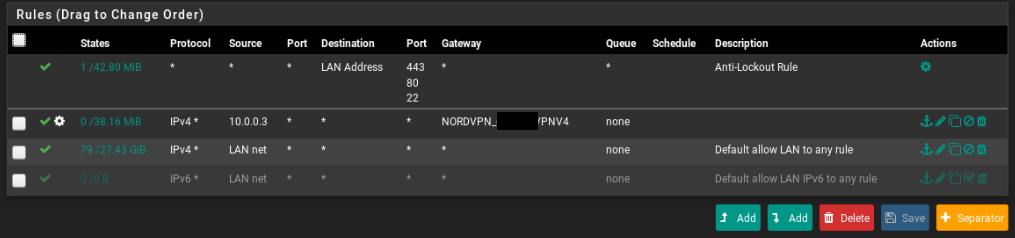
I have this for now
-
@luckyzor Okay so add a new rule at the top that looks like the "Default allow LAN to any rule" but instead of the Destination being set to any (*), set it to "DMZ Address", or more likely "OPT1 Address", whatever corresponds to your DMZ interface. I'd probably also move it below the Anti-Lockout Rule, but that's just for aesthetics; since they'll have mutually exclusive destinations they can't both match the same traffic anyway.
-
@thenarc said in NordVPN Client only for specific hosts:
So you set the Gateway setting to Default, but that doesn't mean it uses the default gateway.
Huh? You leave the gateway at default - ie you don't touch it and then it uses routing.. Maybe its just me doing this stuff for 30+ years and using pfsense for 10 some years. But its pretty freaking clear..
Here is what I will say - pretty much every guide I have seen out there for all these BS vpn services is either just WRONG or not how you should be doing it... I have yet to see one that was good or actually went into the detail that should be setup. But then again they are catering to the people that would use them in the first place.. So they have to want to go over the most basic info - click this and you will use us sort of setups.
What I would suggest is understand how it works before attempting to route traffic out a vpn vs just clicking buttons on some "guide" you found from 3 versions back, etc.
-
This guy knows what he is talking about
 :
:https://www.infotechwerx.com/blog/Creating-pfSense-Connection-VPNBook
But even he hasn't found the time to update it to a current pfSense version. Still relevant though.
-
@johnpoz All I mean is that from this:
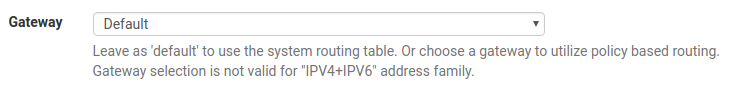
It's not intuitively obvious to me whether "Default" means "use the default gateway." But your point about not needing to touch that setting at all is of course dead on.I enjoy contributing what I can to the forums, and I do my best not to misrepresent my level of knowledge or confidence. I never mind being corrected, and am willing to admit when I'm wrong. I've received and appreciated valuable assistance from you in the past, and I believe I have always deferred to your expertise. But sometimes the tone of responses is discouraging. If there's a concern that forum members below a certain level of expertise are routinely providing dangerous or misleading information, I can respect that. I can even accept if that's an opinion held of me, in which case I'll gladly stop attempting to provide answers and use the forums only when I have questions of my own. But a gentle correction suffices. I admittedly know less than you and many others on the forum, and enjoy learning more, but enthusiasm wanes when I'm made to feel stupid for trying to help others. That said, I may be more sensitive than others in that respect. And I pledge to try to better qualify any advice I give in the future with my relative level of confidence in its accuracy, or to not comment at all if my confidence is not relatively high. I promise that I don't want to give people bad advice just as much as you don't want me to give people bad advice.
-
It says it right there. use the system routing table
-
@derelict Yeah so basically, if you select anything other than "Default" in that drop-down, you're overriding the system routing table and saying "use only this one specific gateway (or gateway group) that I specify" (i.e. policy routing), right? And when you select a default gateway (in System > Routing), you're selecting the gateway used for the default route in the system routing table. Just trying to get my terminology straight.
-
https://www.netgate.com/docs/pfsense/book/
-
This post is deleted! -
waking an old thread but are you still using this method?
I've done exactly what you have initially done but only want one local IP to use the VPN.
I'm pretty new to this all and can't quite work out how to get only one device to use the nord gateway and the rest of the network to stay as normal.
-
@jordo_6 Only policy route the source address(es) you want to shove out the VPN gateway like this https://forum.netgate.com/post/820908
You probably also need to enable "Don't Pull Routes" in the OpenVPN client so if they are sending you a default route (Really two routes, 0.0.0.0/1 and 128.0.0.0/1), you don't install it/them.
-
Thank you for the response.
I clearly don't understand it enough to get it working without it being all or nothing.
Following the guide on nord's website will get it working for the whole network but I just can't seem to work out how to define it like you say.
I feel like there must be something else I'm not understanding that I shouldn't be following to get it to work as suggested.
I'm pretty sure I enabled to 'don't pull routes' as you mention and I see was also mentioned earlier on that fixed it for the OP but I just seem to break the whole thing when I try to do it as described.
to clarify, this is the guide i followed which works, but obviously isn't how I want it to be set haha
https://support.nordvpn.com/hc/en-us/articles/20382523899281-pfSense-2-5-Setup-with-NordVPN
-
@jordo_6 You really can't be "pretty sure" about these things. Look at the client configuration and see.
-
@jordo_6 that guide is pretty lame to be honest.. The client cert, using your web cert is gibberish.. That should pretty much say to set it to none and use username and password, or it doesn't matter.. Not that you should leave it on the web gui cert and your numbers might be different. They have you set a username and password, so the client cert should be set to none to be honest.
They have you do dnskey prefetch, but turning off dnssec - which yeah when you forward to their dns it you should have dnssec disabled. But if you do then there is zero use to try and prefetch the dnskey..
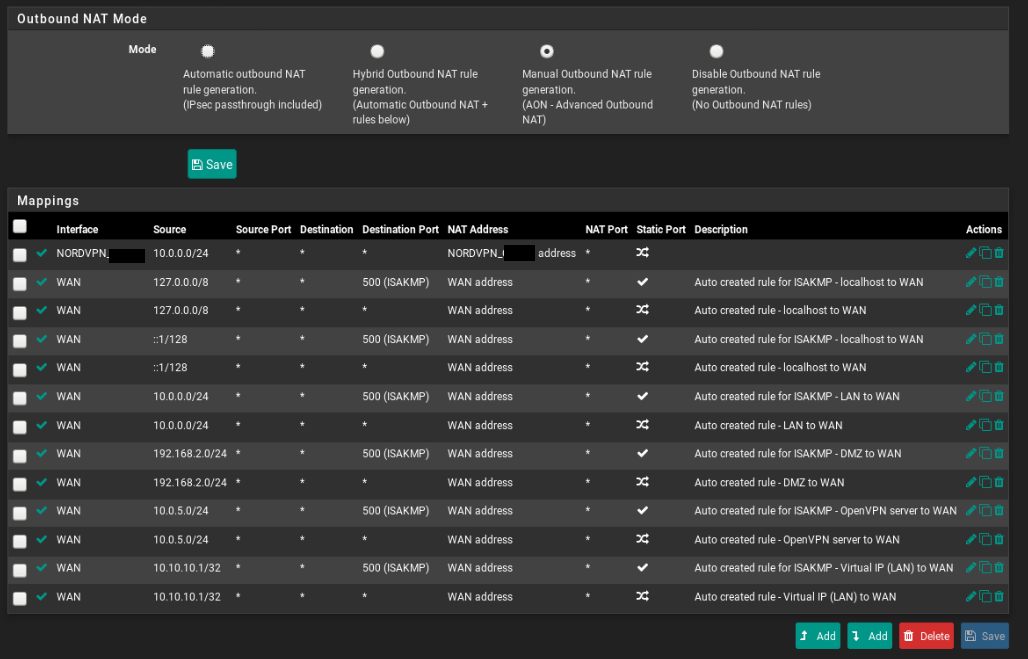
The whole nonsense of going manual outbound nat is horrible suggestion on their part. Also they say to set a cbc cipher, which to be honest has been dead a really long time..
Just a few of the problems I see in that guide with a 20 second read through.
I would setup the client, don't pull routes.. Don't change your outbound nat from automatic.. And then setup a hybrid nat to use the nordvpn interface gateway you setup. Then just create a policy route, firewall rule that sends traffic out your nord gateway.
-
@johnpoz said in NordVPN Client only for specific hosts:
I would setup the client, don't pull routes.. Don't change your outbound nat from automatic.. And then setup a hybrid nat to use the nordvpn interface gateway you setup. Then just create a policy route, firewall rule that sends traffic out your nord gateway.
Hi, I'm new here and having the same problem respectively the same goal, to rout only specific hosts trough NordVPN. I have set up everything linke in the NordVPN tutorial, so all ztrafics goes trough NordVPN
Can you be more detailed about how to turn it back respectively change it so that only specifics hosts are going trough?
What I already did was to create an alias (with one host) as source in the NAT outbound rule and in the Firewall rule but it did not work. (rest like in the tutorial).
Maybe you can create a kind of tutorial for this topic, since it is for sure a use case for everyone? That would be highly appreciated!


Thanks