Suricata SID Management ruleset enable: Enables the default disabled rules
-
If I enable an entire ruleset by checking the boxes on the CATEGORIES tab, the default disable rules (the ones commented out) will not be enabled. However, if I enable a ruleset using SID Management file like this:
# enablesid.conf emerging-dnsthen all of the rules in that category are enabled, even the default disabled ones. I would have expected the same behavior as checking the box in the GUI. Is this the correct behavior?
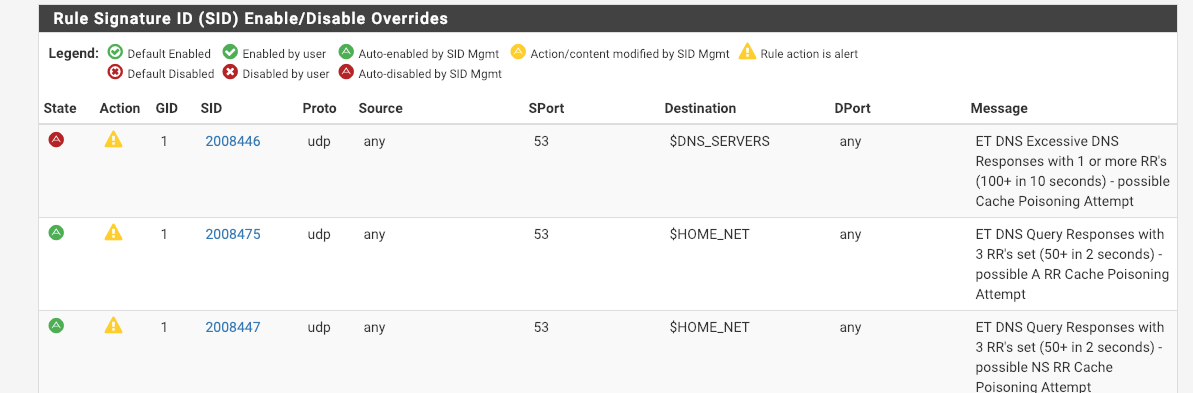
The first three rules in the ET dns set are disabled by default:
# emerging-dns.rules ... #alert udp any 53 -> $DNS_SERVERS any (msg:"ET DNS Excessive DNS Responses with 1 or more RR's (100+ in 10 seconds) - possible Cache Poisoning Attempt"; byte_test:2,>,0,6; byte_test:2,>,0,10; threshold: type both, track by_src, count 100, seconds 10; reference:url,doc.emergingthreats.net/bin/view/Main/2008446; classtype:bad-unknown; sid:2008446; rev:9; metadata:created_at 2010_07_30, updated_at 2010_07_30;) #alert udp any 53 -> $HOME_NET any (msg:"ET DNS Query Responses with 3 RR's set (50+ in 2 seconds) - possible A RR Cache Poisoning Attempt"; content: "|81 80 00 01 00 01 00 01|"; offset: 2; depth:8; threshold: type both, track by_src, count 50, seconds 2; reference:url,infosec20.blogspot.com/2008/07/kaminsky-dns-cache-poisoning-poc.html; reference:url,doc.emergingthreats.net/bin/view/Main/2008475; classtype:bad-unknown; sid:2008475; rev:4; metadata:created_at 2010_07_30, updated_at 2010_07_30;) #alert udp any 53 -> $HOME_NET any (msg:"ET DNS Query Responses with 3 RR's set (50+ in 2 seconds) - possible NS RR Cache Poisoning Attempt"; content: "|85 00 00 01 00 01 00 01|"; offset: 2; depth:8; threshold: type both, track by_src,count 50, seconds 2; reference:url,infosec20.blogspot.com/2008/07/kaminsky-dns-cache-poisoning-poc.html; reference:url,doc.emergingthreats.net/bin/view/Main/2008447; classtype:bad-unknown; sid:2008447; rev:7; metadata:created_at 2010_07_30, updated_at 2010_07_30;) ...You can see they're enabled by SID Mgmt. I then have to disable them one-by-one in my disablesid.conf.
-
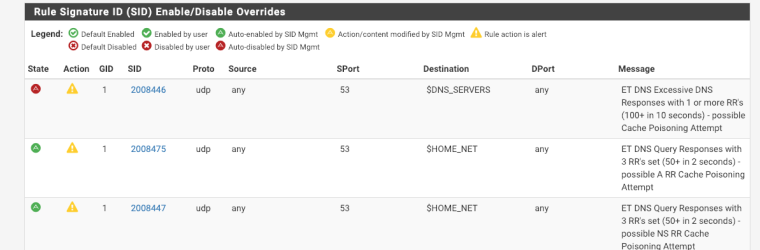
That is by design. I assumed, when writing the SID MGMT logic, that admins choosing to enable a category via SID MGMT wanted all the rules enabled in that category. You can still turn individual rules off via GID:SID pairings in disablesid.conf. If you want to use the category as it comes from the rules vendor (i.e., with "default disabled" rules disabled), then make the category selection on the CATEGORIES tab instead.
The CATEGORIES tab and the SID MGMT tab are complimentary and work together. So you can use a combination of settings on each tab to accomplish just about anything.
-
Not a huge deal, more of an annoyance. Thank's for confirming.