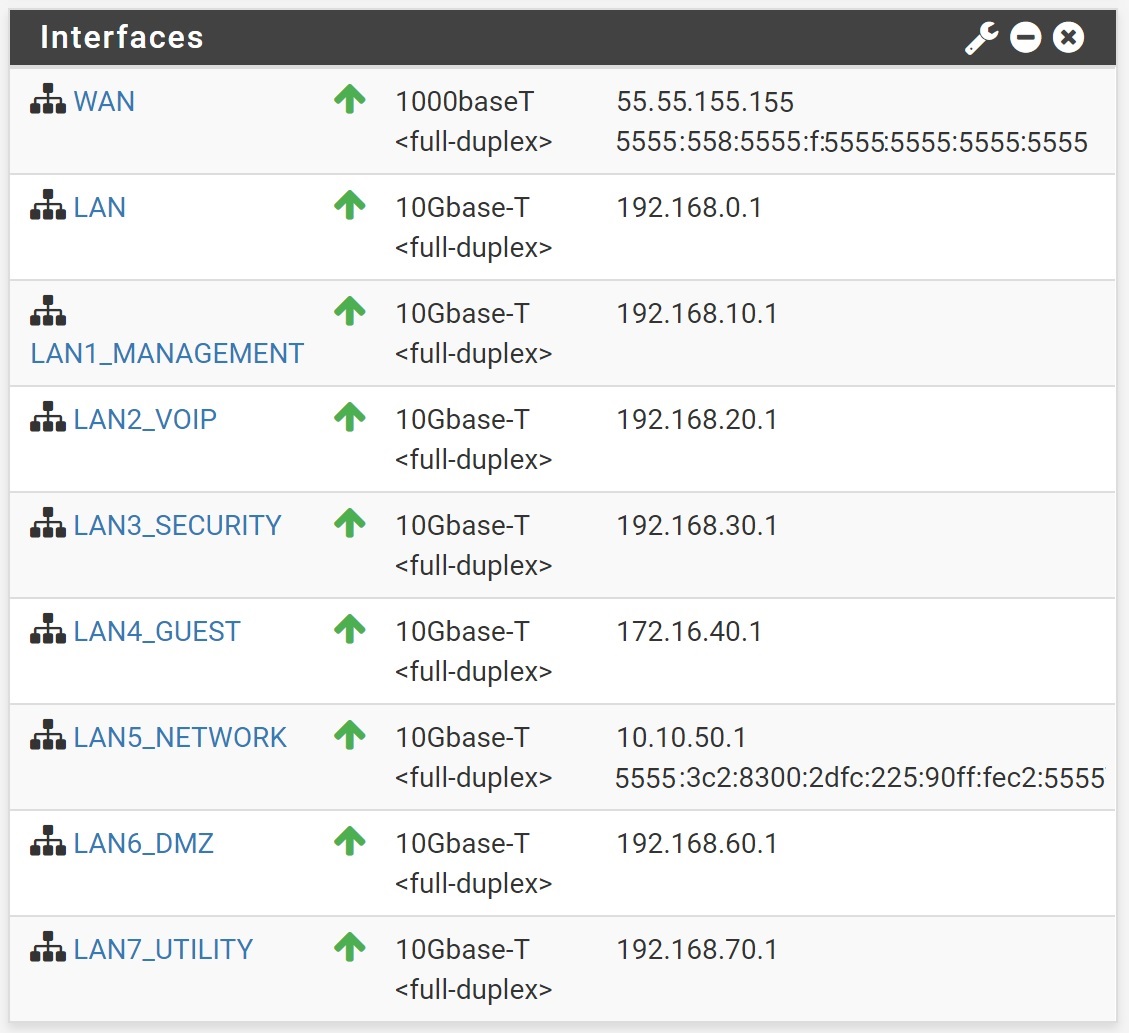
Interfaces for LAN vs VLAN
-
I'm currently running pfSense on a stick with multiple VLANS into a 10GbE switch. Currently, I have my VLAN trunk on the same interface as my LAN. I've read where in the past, it wasn't done for cross VLAN traffic considerations. I've seen where some have disabled the LAN interface all together and others have just left it. The only rule I have on my LAN right now is the anti-lockout. Or, just a simple separation from the VLAN interface.
Any suggestions?
-
Huh?
What exactly are you asking? Vlans on the same physical interface share the bandwidth of the physical interface.. So yeah any intervlan traffic will be a hairpin..
Do you not have any other interfaces?
Are you asking if you should disable that lan if not using it, or put a vlan tag on it?
At a loss to actual question here? You can for sure use a native untagged network on an interface that has vlans on it. Some like to only do vlans vs native on such interfaces. But that is more personal preference. A native untagged vlan on a physical interface along with tagged vlans is normal and used all over the place.
BTW where are you getting 5555 for ipv6? Are you wanting to obfuscate your IPv6 address? 5555 is currently not allocated IPv6 space.. You can't just pull address space out of range that is not allocated and use it. 55/8 is also a DOD space - which I find it highly unlikely your actually part of the USAISC, so this is also an obfuscation - which really nicely done can not tell that its a paste? Or you just making UP IPs you don't think will be used an using them on your own network.. Which is just BORKED!!
-
Apologies, it was 3AM local when I wrote the question, and after rereading it (after a couple hours sleep), I can see it's not very clear at all. I think you did answer my question though. I don't plan to use the lan for anything. I have several more interfaces...four more 1G and one more 10G (and space for another card if needed). But yes, should it be disabled? Or moved to another interface? Is there a reason or an advantage of doing one thing over another other than just personal prefrence?
-
If you have multiple physical interfaces - then sure you can spread your vlans across the physical interfaces and use different uplinks fro your switches to remove the sharing of vlans on a physical interface to remove the possible bottleneck of traffic that is either intervlan on the same physical and a hairpin.
Or just shared bandwidth. If you have a 10ge interface and your interface traffic is all say gig then you prob won't have a bottleneck issue.
Without understanding your local network, and its data flow either between vlans or to and from the wan(s) of the router is hard to say would be the optimal solution.
So curious minds want to know about these 55 and 5555 address space - is it obfuscation? Or you actually using that space - if your actually using it that is pretty borked and I would about fixing that before worried about what physical interfaces to put your vlans and should they be tagged or not tagged ;)
Running all traffic through 1 interface does put all your eggs in 1 basket if that interface fails everything is down vs spread out if say you loose interface on switch or router its not all traffic.
-
LOL. Just chopped it for the screen shot...It really has no "5"s in it.
-
its a good obfuscation then - looks like actual screen shot!
Better to mention you obfuscated or use documented example networks and mention that ;)
192.0.2/24
198.51.100/24
203.0.113/242001:DB8::/32
Just saying ;) You would be surprised at some of the stuff you see around here people doing for real ;)
Or just block out part of the actual address so its clear is obfuscation..