Issue Connecting pfsense as a client to OpenVPN Access Server
-
Hi all,
I have setup an OpenVPN Access Server on AWS using the AMI.
I tried connecting to it via a normal windows client and it worked fine, but when I configured it through pfsense OpenVPN client (Auto login) it constantly shows the following status.ping restart; reconnectingorstatus : downWhen I tailed the logs on the Access server side than the following error was found in the logs.
2019-02-04 09:15:51+0000 [-] OVPN 1 OUT: 'Mon Feb 4 09:15:51 2019 Authenticate/Decrypt packet error: packet HMAC authentication failed' 2019-02-04 09:15:51+0000 [-] OVPN 1 OUT: 'Mon Feb 4 09:15:51 2019 TLS Error: incoming packet authentication failed from [AF_INET]x.x.x.x:40511 (via [AF_INET]x.x.x.x%eth0)' 2019-02-04 09:15:59+0000 [-] OVPN 1 OUT: 'Mon Feb 4 09:15:59 2019 Authenticate/Decrypt packet error: packet HMAC authentication failed' 2019-02-04 09:15:59+0000 [-] OVPN 1 OUT: 'Mon Feb 4 09:15:59 2019 TLS Error: incoming packet authentication failed from [AF_INET]x.x.x.x:40511 (via [AF_INET]x.x.x.x%eth0)' 2019-02-04 09:16:15+0000 [-] OVPN 1 OUT: 'Mon Feb 4 09:16:15 2019 Authenticate/Decrypt packet error: packet HMAC authentication failed' 2019-02-04 09:16:15+0000 [-] OVPN 1 OUT: 'Mon Feb 4 09:16:15 2019 TLS Error: incoming packet authentication failed from [AF_INET]x.x.x.x:40511 (via [AF_INET]x.x.x.x%eth0)'Can someone please help me in this ?
Thanks
-
Without showing what you did or didn't do when you set it up. Ho wae we suppose to help you.
I have openvpn-as running on vps... Click Click to connect to it. Post up your config from your server and your client so we can see what your doing wrong.
-
here is the client configuration.
dev ovpnc1 verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_client1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-256-CBC auth none up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local x.x.x.x tls-client client lport 0 management /var/etc/openvpn/client1.sock unix remote x.x.x.x 1194 ifconfig x.0.0.x x.0.0.x route x.x.0.0 255.255.0.0 ca /var/etc/openvpn/client1.ca cert /var/etc/openvpn/client1.cert key /var/etc/openvpn/client1.key tls-crypt /var/etc/openvpn/client1.tls-crypt ncp-disable comp-lzo no passtos resolv-retry infinite topology subnet key-direction 1 setenv opt tls-version-min 1.0 or highest setenv FORWARD_COMPATIBLE 1 ns-cert-type server setenv PUSH_PEER_INFO -
And how about the Server configuration?
-Rico
-
@Rico Is this what you are talking about ?
As I am not able to find any other configuration files.# # NOTE: The ~ symbol used below expands to the directory that # the configuration file is saved in # remove for production # DEBUG=false # enable AS Connect functionality AS_CONNECT=true # temporary directory tmp_dir=~/tmp lic.dir=~/licenses # run_start retries run_start_retry.give_up=60 run_start_retry.resample=10 # enable client gateway sa.show_c2s_routes=true # certificates database certs_db=sqlite:///~/db/certs.db # user properties DB user_prop_db=sqlite:///~/db/userprop.db # configuration DB config_db=sqlite:///~/db/config.db # log DB log_db=sqlite:///~/db/log.db # wait this many seconds between failed retries db_retry.interval=1 # how many retries to attempt before failing db_retry.n_attempts=6 # On startup, wait up to n seconds for DB files to become # available if they do not yet exist. This is generally # only useful on secondary nodes used for standby purposes. # db_startup_wait= # Node type: PRIMARY|SECONDARY. Defaults to PRIMARY. # node_type= # bootstrap authentication via PAM -- allows # admin to log into web UI before authentication # system has been configured. Configure PAM users # allowed to access via the bootstrap auth mechanism. boot_pam_service=openvpnas boot_pam_users.0=openvpn # boot_pam_users.1= # boot_pam_users.2= # boot_pam_users.3= # boot_pam_users.4= # System users that are allowed to access the server agent XML API. # The user that the web server will run as should be in this list. system_users_local.0=root system_users_local.1=openvpn_as # The user/group that the web server will run as cs.user=openvpn_as cs.group=openvpn_as # socket directory general.sock_dir=~/sock # path to linux openvpn executable # if undefined, find openvpn on the PATH #general.openvpn_exe_path= # source directory for OpenVPN Windows executable # (Must have been built with MultiFileExtract) sa.win_exe_dir=~/exe # The company name will be shown in the UI sa.company_name=OpenVPN, Inc. # server agent socket sa.sock=~/sock/sagent # If enabled, automatically generate a client configuration # when a client logs into the site and successfully authenticates cs.auto_generate=true # files for web server (PEM format) cs.ca_bundle=~/web-ssl/ca.crt cs.priv_key=~/web-ssl/server.key cs.cert=~/web-ssl/server.crt # web server will use three consecutive ports starting at this # address, for use with the OpenVPN port share feature cs.dynamic_port_base=870 # which service groups should be started during # server agent initialization sa.initial_run_groups.0=web_group #sa.initial_run_groups.1=openvpn_group # use this twisted reactor sa.reactor=epoll # The unit number of this particular AS configuration. # Normally set to 0. If you have multiple, independent AS instances # running on the same machine, each should have a unique unit number. sa.unit=0 # If true, open up web ports on the firewall using iptables iptables.web=true vpn.server.user=openvpn_as vpn.server.group=openvpn_as``` -
Hmmm no idea what this is. ;-)
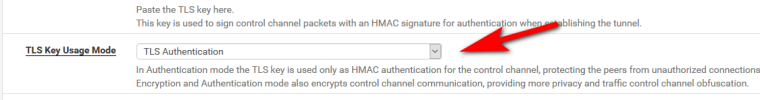
However please try to switch TLS Encryption and Authentication to TLS Authentication in your pfSense Client.-Rico
-
@Rico Thanks a lot!! I was able to to connect after switching TLS Encryption and Authentication to TLS Authentication and than after that Added SHA1(160 bit)
Now I am able to ping the AWS network from pfsense end but not able to ping the remote network (pfsense) side from the AWS end.
I am not able to ping bidirectionally, Is this a normal behaviour in case of OpenVPN our some pfsense configuration needs to be done ?
-
You need to setup your Rules in the Firewall -> Rules -> OpenVPN tab (pfSense WebGUI).
For testing just do any-any and check if everything works.-Rico
-
@shahid3507 said in Issue Connecting pfsense as a client to OpenVPN Access Server:
tls-crypt /var/etc/openvpn/client1.tls-crypt
I am like 99% sure that openvpn-as does not support tls-crypt.. Atleast not current 2.6.1 version..
The AS stores its config in a db, so its a bit harder to show - but there is zero place to turn on crypt for tls in the gui. And do believe reading something about it - they did a while back enable crypt for the connect client (ios and android) but I do not believe the AS server supports it as of yet.
When you setup the client in pfsense - did you download the client config from the AS to validate what you need to set?
example - just download my client config from my AS
Automatically generated OpenVPN client config file # Generated on Mon Feb 4 07:15:51 2019 by ns1 # Note: this config file contains inline private keys # and therefore should be kept confidential! # Note: this configuration is user-locked to the username belowCerts will all be inline
And its just doing auth
key-direction 1 <tls-auth> # # 2048 bit OpenVPN static key (Server Agent) # -----BEGIN OpenVPN Static key V1----- 12303adb7486e4ef9d4dae4742741a22 10f785d43598499de66a7da89ee45221 <snipped> 235863ac6188180030d13ab6481e966c a8bd1f1b1c08bd009430af58ab3e0b88 -----END OpenVPN Static key V1----- </tls-auth> -
@johnpoz I have just downloaded the config from AS and followed this document.
https://www.netgate.com/docs/pfsense/vpn/openvpn/connecting-pfsense-to-an-openvpn-access-server.html -
Seems you didn't follow the part where it says
" pfSense may be configured to use the info in the .ovpn file"
And not encryption and auth. Double check all your other settings.
example here is my client config form pfsense for my openvpn-as server
dev ovpnc3 verb 1 dev-type tun dev-node /dev/tun3 writepid /var/run/openvpn_client3.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-256-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 64.53.<snipped> engine rdrand tls-client client lport 0 management /var/etc/openvpn/client3.sock unix remote <snipped> 1195 ca /var/etc/openvpn/client3.ca cert /var/etc/openvpn/client3.cert key /var/etc/openvpn/client3.key tls-auth /var/etc/openvpn/client3.tls-auth 1 ncp-ciphers AES-128-GCM:AES-192-GCM:AES-256-GCM:AES-128-CBC:AES-192-CBC:AES-256-CBC comp-lzo no resolv-retry infinite route-nopull fast-io sndbuf 524288 rcvbuf 524288 [2.4.4-RELEASE][root@sg4860.local.lan]/var/etc/openvpn:notice
tls-auth /var/etc/openvpn/client3.tls-auth 1 -
-
What are you trying to ping?
-
The tunnel is connecting and I am able to ping the AWS side (Access server subnet) but when I am trying to ping the client side form the access server or the subnet than it's not reachable.
-
Any Idea regarding this connectivity stuff @Rico ??
-
Not atm, I don't have any experience with OpenVPN AS or AWS, sorry.

But my guess is @johnpoz will come back with some ideas.
-Rico
-
Ping what exactly? Can you ping the lan IP of pfsense from your aws side?
-
No I can't @johnpoz
-
What is your routing on your aws side show you how to get to your lan network?
-