Issue Connecting pfsense as a client to OpenVPN Access Server
-
Seems you didn't follow the part where it says
" pfSense may be configured to use the info in the .ovpn file"
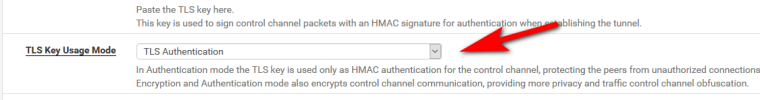
And not encryption and auth. Double check all your other settings.
example here is my client config form pfsense for my openvpn-as server
dev ovpnc3 verb 1 dev-type tun dev-node /dev/tun3 writepid /var/run/openvpn_client3.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-256-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 64.53.<snipped> engine rdrand tls-client client lport 0 management /var/etc/openvpn/client3.sock unix remote <snipped> 1195 ca /var/etc/openvpn/client3.ca cert /var/etc/openvpn/client3.cert key /var/etc/openvpn/client3.key tls-auth /var/etc/openvpn/client3.tls-auth 1 ncp-ciphers AES-128-GCM:AES-192-GCM:AES-256-GCM:AES-128-CBC:AES-192-CBC:AES-256-CBC comp-lzo no resolv-retry infinite route-nopull fast-io sndbuf 524288 rcvbuf 524288 [2.4.4-RELEASE][root@sg4860.local.lan]/var/etc/openvpn:notice
tls-auth /var/etc/openvpn/client3.tls-auth 1 -
-
What are you trying to ping?
-
The tunnel is connecting and I am able to ping the AWS side (Access server subnet) but when I am trying to ping the client side form the access server or the subnet than it's not reachable.
-
Any Idea regarding this connectivity stuff @Rico ??
-
Not atm, I don't have any experience with OpenVPN AS or AWS, sorry.

But my guess is @johnpoz will come back with some ideas.
-Rico
-
Ping what exactly? Can you ping the lan IP of pfsense from your aws side?
-
No I can't @johnpoz
-
What is your routing on your aws side show you how to get to your lan network?
-