help setting the Public Key Pinning in HAProxy
-
Why would you not just use the acme package to get your certs, then they get put right into the certmanager in pfsense and you can just select it for your ha proxy setup?
I just did this took all of like 5 minutes to get working ;)
-
hi. @johnpoz
I have done that exactly....
Why In the report here https://www.ssllabs.com/ssltest/analyze.html?d=enlinea.bicsa.cu i see an alert about Incomplete No chains pinned; check backup pins...
i have to repeat the extraction of public key each time when issue my cert and add it to http-response add-header Public-Key-Pins??? it is not clear to me... or this is an alert that I do not have to worry about??
Thanks
Sorry my english -
Tell you what - let me move my site to 443 so I can test it.. And we can work through this together. I currently have on my to do list to work out how to use haproxy to allow me to run openvpn on 443 while also doing sites behind on 443... I currently have it setup on 8443 and openvpn on 443 so I can hit it from work off a proxy.
Your post will just accelerate my timeline ;) is all.. Was planning on playing with this this weekend. But since I am home an don't need access to openvpn... I can just move to 443 without the need to share..
Will play with this tmrw and let you know what the test shows ;)
edit: ok I just disabled my openvpn server on 443 and setup a frontend using the same cert to send to my backend and tested... I would think out of the box just clicking go a B is pretty good.
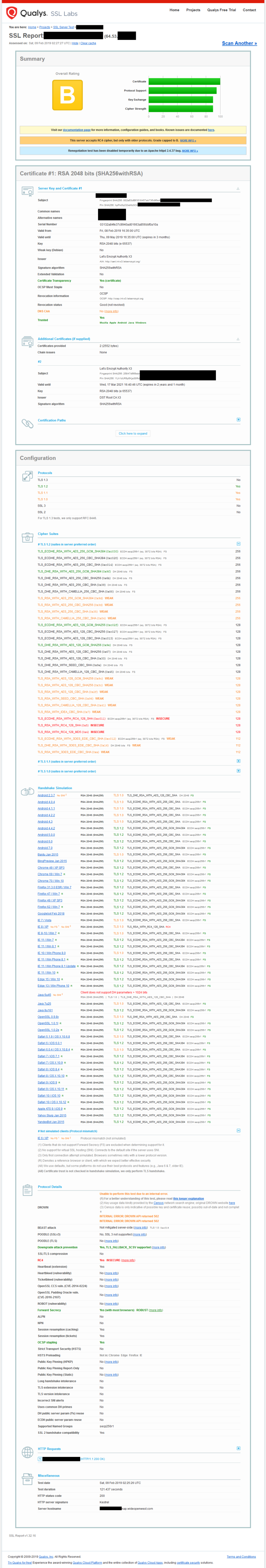
Lets see your results.. I will play with this a bit and see if can get to an A without much issue - I had saw where I could easy restrict to tls 1.2, etc. etc.. But since I lock this down to only my friends an family to access ombi to request stuff for my plex I wasn't too worry about it, etc.. But his is good excuse to set it up with better settings ;)
-
Ok that took all of a couple of minutes
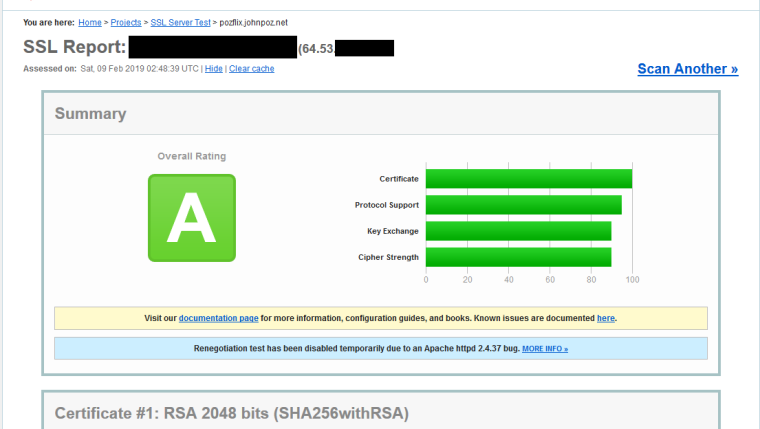
Quick google for hardening ha proxy.. Quick copy paste in the global settings. And now A rating.
ssl-default-bind-options no-sslv3 no-tls-tickets ssl-default-bind-ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHASo post up what your concerned about in your report and we can discuss.
I will for sure look into it deeper, but that was a quick jump from B to A with simple copy paste ;)
edit: Will have to play with this weekend.. 100 across the board would be the goal ;)
-
Ok played with it a bit more and up to A+ with some minor tweaks, enabled CAA in my dns record, turned on HSTS
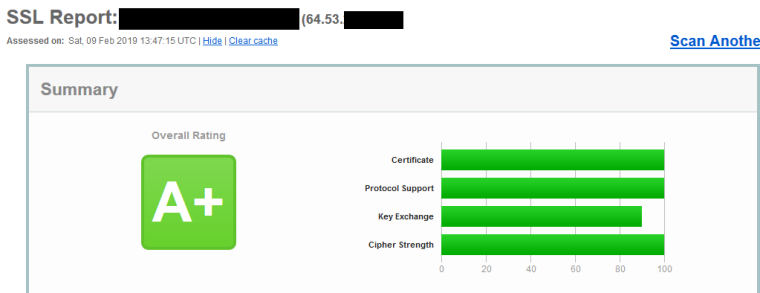
So your worried about the pinning - to be honest not sure that really took off much... But as I finish my coffee before my walk let me see if can get that going.
edit:
I would just go here and it will pull your hashes for you
https://report-uri.com/home/pkp_hashedit: Yeah I don't suggest you do pinning from everything I have been reading.. It seems to be a serious problem if you dick it up ;)
-
@johnpoz said in help setting the Public Key Pinning in HAProxy:
ah I don't suggest you do pinning from everything I have been reading.. It seems to be a serious problem if you dick it up ;)
hi @johnpoz thanks for response.. and sorri... I have been outside the coverage area.
i wiil chek my config to set my hashes according to the link has u send, and let you know if it work for me
So every time the certificate changes or is renewed thats hashes most be updated ton the hashes??
thanks -
Dude my point is there is no point to doing pinning at all.. And if you dick it going forward when you have to renew your certs, etc.
I don't see how its worth the hassle at all.. Why do you want or think you need to pin?
-
@johnpoz said in help setting the Public Key Pinning in HAProxy:
be honest not sure that really took off much... But as I finish my coffee before my walk let me see if can get that going.
edit:i tested rigth now, but the report say to me me pinin are inclomplete.. son comented entry line and report again and have an A+!
i wass generated the ssl config here: https://mozilla.github.io/server-side-tls/ssl-config-generator/ for moderns browser.
i will going to read more about public key pinnin thanks -
@johnpoz I'm not sure, I have my doubts, I should read and investigate more about pinning
-
Yup I completely agree - it took me about 5 minutes of reading to know not something that should be doing ;)
Especially with a cert that expires every 90 freaking days ;) Chrome doesn't even support it anymore.. Like back in end of 2017..
Did you read the link they send you to for info on it, on their own site they say its dead ;)
https://blog.qualys.com/ssllabs/2016/09/06/is-http-public-key-pinning-deadedit: BTW a few other tweaks, and now 100 across the board.. I removed the 128s from what moz suggest as ciphers, this gets you to 100 on ciphers.. And if your use 4096 or higher AND you set ecdhe secp384r1
So in my advanced I have set
alpn h2 ecdhe secp384r1You should get A+ with 100 across
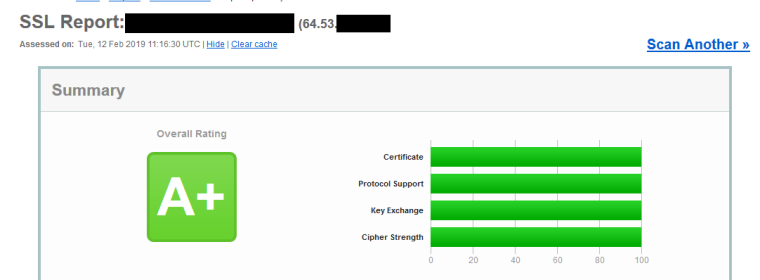
With no need to PIN ;)
And once openssl 1.1.1 comes down the pipe to pfsense we should be able to do TLS 1.3 ;)
-
@johnpoz said in help setting the Public Key Pinning in HAProxy:
alpn h2 ecdhe secp384r1
thanks for the clarification, and the links has helped me a lot to learn more about the subject. I agree and now I have an A+ too! thanks again
-
We both learned a bit ;) Thanks for the questions, it got me playing with HA proxy and ACME.. I had not had a reason to use them until you brought up the question(s)
After that I had no excuse not to use them and fired up a shared port for my openvpn that listens on 443 and then hands off to ha proxy so I can use https with my ombi plex request system via https ;)
Win Win all around I would say!