Disable or prohibit routing between local subnets
-
I have two subnets going off a quad port Intel NIC.
First one on the interface em0 is my main network 10.3.0.0/24
Second one, mapped to the em3 is a freshly set up lab network 10.3.100.0/24
I would like to prohibit any devices located on the main network from being able to access the resources on the lab one and vice versa.
pfSense acts as a default gateway for the lab network but not as a DHCP server. DNS server addresses given to the devices on the lab network are public (google, etc.)
Currently the only FW rule for the lab net is the automated anti-lockout one so no traffic should be allowed in. However I can ping a server located on the lab network from my PC on the main network.
-
@morgenstern said in Disable or prohibit routing between local subnets:
Currently the only FW rule for the lab net is the automated anti-lockout one so no traffic should be allowed in. However I can ping a server located on the lab network from my PC on the main network.
Read up on how the firewall and states work.
RTFM:
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-basics.html
https://docs.netgate.com/pfsense/en/latest/book/firewall/index.html -
Sorry, but tl;dr.
Is there an easy, (what to do) answer available rather than being pointed to an encyclopaedia?
-
@morgenstern said in Disable or prohibit routing between local subnets:
Is there an easy, (what to do) answer available rather than being pointed to an encyclopaedia?
If you want to maintain your firewall right you need to understand how it works, so start reading.
-
@morgenstern said in Disable or prohibit routing between local subnets:
Sorry, but tl;dr.
Is there an easy, (what to do) answer available rather than being pointed to an encyclopaedia?
BTW, I did try putting a deny any*any rule on the lab network but I can still ping it.
-
Rules are evaluated top down, first rule to trigger wins no other rules are evaluated on the interface that traffic enters the firewall from the network.
If you want to block network/vlan A from talking to network/vlan B then the rule to deny that traffic would go on the interface A rules.
TL;DR for the manual of how firewall rules work is not going to be a valid answer - sorry ;) If you do not understand how the rules work, then you will never be able to adjust them to how you want them..
-
Rules are evaluated top down, first rule to trigger wins no other rules are evaluated on the interface that traffic enters the firewall from the network.
If you want to block network/vlan A from talking to network/vlan B then the rule to deny that traffic would go on the interface A rules.
I have put the below rule on the top of rule set for network 1 and killed all the existing connection states to the network 2.
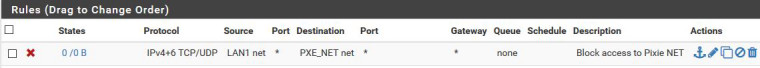
Yet, I can still ping a server located on the network 2 from my pc on the network 1.
-
Not to worry. Resolved now. Thanks all.
-
ping or (icmp) is not tcp/udp ;)