OpenVPN: TLS Negotiation Failed?
-
Hello - I seem to keep running into this issue after trying a few things and redoing the setup of OpenVPN (With and without Wizard).
Here's the network layout and purpose:
WAN (bce0) is on my Xfinity xFi Router's network (10.0.0.X), Statically assigned IPv4.
LAN (bce1) is connected to a Netgear Gigabit Plus Switch (10.0.2.X), IPv4 DHCP Server Enabled.
OPT1 is a VLAN(.10) on LAN's interface - but I disabled this for now.My purpose is to be able to tunnel into my 10.0.2.X network locally from my laptop (Macbook Air with Windows 10 via Bootcamp) using OpenVPN. My laptop is on the 10.0.0.X subnet/network. My servers operate off the 10.0.2.X network.
OpenVPN is using port 1194/UDP as of right now. I also tried to use a Dynamic DNS solution using No-IP. That is now disabled.
Tue Feb 12 00:16:53 2019 OpenVPN 2.4.6 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 26 2018 Tue Feb 12 00:16:53 2019 Windows version 6.2 (Windows 8 or greater) 64bit Tue Feb 12 00:16:53 2019 library versions: OpenSSL 1.1.0h 27 Mar 2018, LZO 2.10 Tue Feb 12 00:16:59 2019 TCP/UDP: Preserving recently used remote address: [AF_INET]10.0.0.20:1194 Tue Feb 12 00:16:59 2019 UDP link local (bound): [AF_INET][undef]:1194 Tue Feb 12 00:16:59 2019 UDP link remote: [AF_INET]10.0.0.20:1194 Tue Feb 12 00:17:59 2019 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Tue Feb 12 00:17:59 2019 TLS Error: TLS handshake failed Tue Feb 12 00:17:59 2019 SIGUSR1[soft,tls-error] received, process restarting Tue Feb 12 00:18:04 2019 TCP/UDP: Preserving recently used remote address: [AF_INET]10.0.0.20:1194 Tue Feb 12 00:18:04 2019 UDP link local (bound): [AF_INET][undef]:1194 Tue Feb 12 00:18:04 2019 UDP link remote: [AF_INET]10.0.0.20:1194Any help is appreciated. I need this to work so I can edit coding projects and other things off my home server.
-
Share your OpenVPN settings and Firewall Rules (screenshots).
-Rico
-
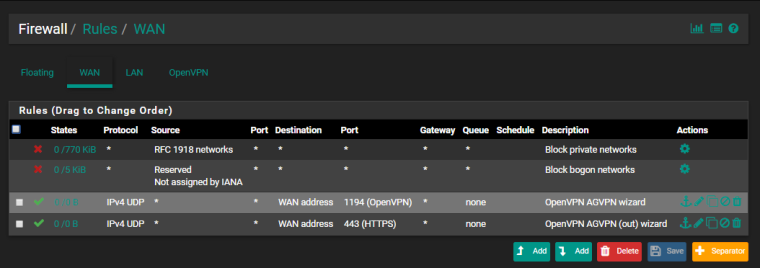
Here are all the screenshots requested. Note: "AGVPN (out)" was my Dynamic DNS Solution, I deleted the rule for it as I'm no longer using it right now, but kept some other ones and the Server config just in case I would want to try it again.
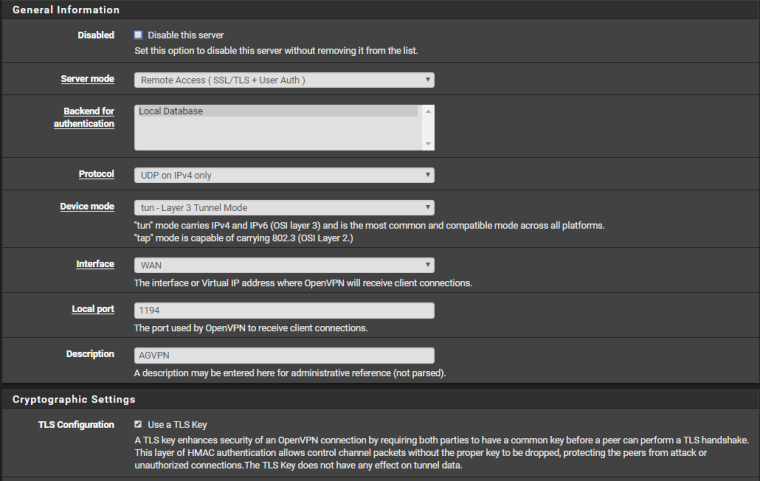
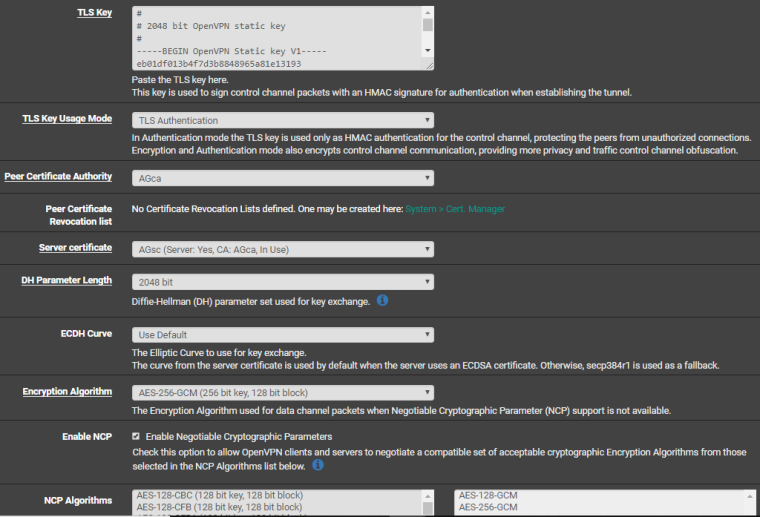
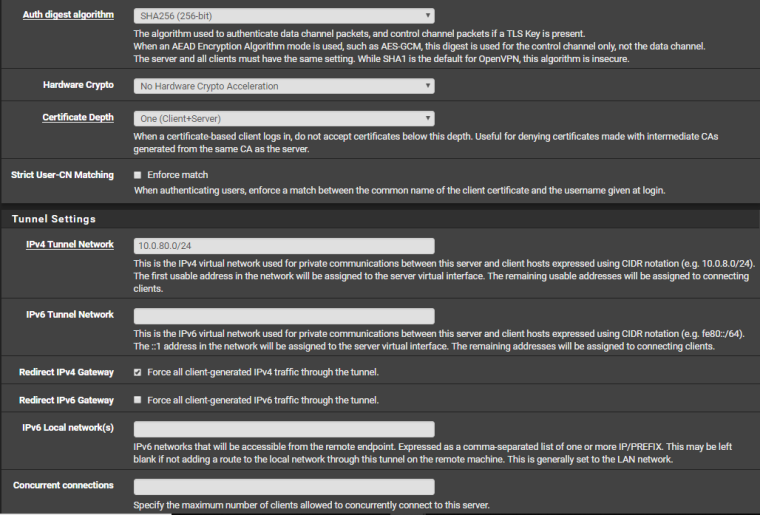
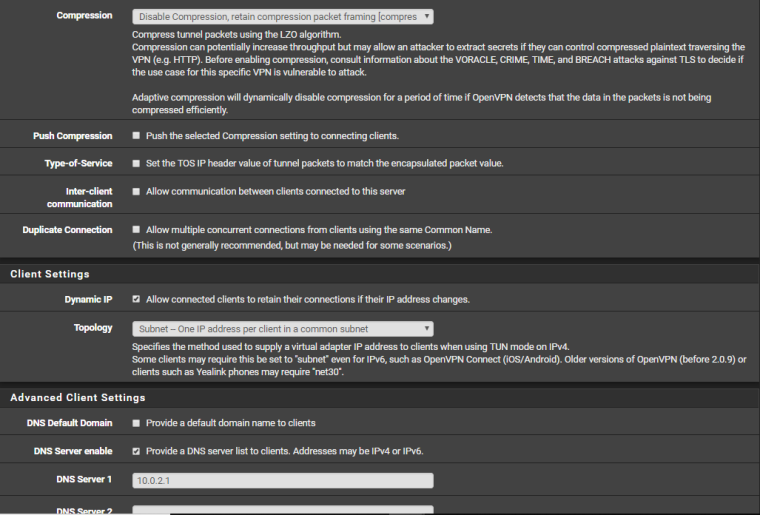
-
@rico Also - I have used User Auth only before, but I still get the same error.
- Andrew
-
Did you use the client exporter to configure the windows client?
The default compression setting is Omit Preference. Why is that changed? Do you know you need to change it?
What does the OpenVPN server log (Status > System Logs, OpenVPN) include when you try to connect?
-
@Derelict I do use the client exporter package. As for the compression setting, I don't ever remember changing that, but it seems I have (not consciously).
Here is the current System Log for OpenVPN (Most recent and current PID)
Feb 12 20:12:43 openvpn 81170 OpenVPN 2.4.6 amd64-portbld-freebsd11.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Oct 3 2018 Feb 12 20:12:43 openvpn 81170 library versions: OpenSSL 1.0.2o-freebsd 27 Mar 2018, LZO 2.10 Feb 12 20:12:43 openvpn 81345 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 12 20:12:43 openvpn 81345 TUN/TAP device ovpns1 exists previously, keep at program end Feb 12 20:12:43 openvpn 81345 TUN/TAP device /dev/tun1 opened Feb 12 20:12:43 openvpn 81345 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Feb 12 20:12:43 openvpn 81345 /sbin/ifconfig ovpns1 10.0.80.1 10.0.80.2 mtu 1500 netmask 255.255.255.0 up Feb 12 20:12:43 openvpn 81345 /usr/local/sbin/ovpn-linkup ovpns1 1500 1621 10.0.80.1 255.255.255.0 init Feb 12 20:12:43 openvpn 81345 UDPv4 link local (bound): [AF_INET]10.0.0.20:1194 Feb 12 20:12:43 openvpn 81345 UDPv4 link remote: [AF_UNSPEC] Feb 12 20:12:43 openvpn 81345 Initialization Sequence Completed -
@agnet said in OpenVPN: TLS Negotiation Failed?:
@Derelict I do use the client exporter package. As for the compression setting, I don't ever remember changing that, but it seems I have (not consciously).
Here is the current System Log for OpenVPN (Most recent and current PID)
Feb 12 20:12:43 openvpn 81170 OpenVPN 2.4.6 amd64-portbld-freebsd11.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Oct 3 2018 Feb 12 20:12:43 openvpn 81170 library versions: OpenSSL 1.0.2o-freebsd 27 Mar 2018, LZO 2.10 Feb 12 20:12:43 openvpn 81345 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 12 20:12:43 openvpn 81345 TUN/TAP device ovpns1 exists previously, keep at program end Feb 12 20:12:43 openvpn 81345 TUN/TAP device /dev/tun1 opened Feb 12 20:12:43 openvpn 81345 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Feb 12 20:12:43 openvpn 81345 /sbin/ifconfig ovpns1 10.0.80.1 10.0.80.2 mtu 1500 netmask 255.255.255.0 up Feb 12 20:12:43 openvpn 81345 /usr/local/sbin/ovpn-linkup ovpns1 1500 1621 10.0.80.1 255.255.255.0 init Feb 12 20:12:43 openvpn 81345 UDPv4 link local (bound): [AF_INET]10.0.0.20:1194 Feb 12 20:12:43 openvpn 81345 UDPv4 link remote: [AF_UNSPEC] Feb 12 20:12:43 openvpn 81345 Initialization Sequence CompletedIt doesn't seem like it's even logging any activity from the device. Could there be a setting on the xFi router I need to change? I have 1194/udp Port Forwarded to 10.0.0.20 (pfSense WAN)
-
If it's not logging anything it is probably not receiving the traffic at all. That would dovetail with the client error messages.
-
@derelict So where can I go from here? According to my current firewall rules on pfSense, it's accepting IPv4 UDP traffic on port 1194/udp.. The only other way I can see is forwarding the traffic on the xFi router to the pfSense router's WAN address (which I already did).

-
If you are connecting from afar to the pfSense WAN IP on UDP 1194 and that traffic is not hitting pfSense WAN, you need to look upstream.
pfSense can only operate on traffic that actually arrives on its interfaces.
-
@derelict I hear ya’. That’s a bummer, but makes sense... I could maybe I replace our existing router with another pfSense one and do a P2P server between both of them instead so the firewalls can talk to each other? xFi isn’t the best with their interface - far too simple. Home-Network friendly I suppose.
Thank you for the help though.