Block ALL from pfSense box but pass all routing...
-
Migrating from nftables to pfsense (pfsense noob) over the last 3 months. Question is; How do I block ALL traffic from/to my pfSense box itself but allow all NAT'd subnets to pass through? I want to completely isolate my pfSense host box from both internal and external networks but allow it to do it's NAT job unencumbered. This was easy in nftables. I'm struggling here (by the way this is my first post here EVER. Tried my Google Fu for months.)
-
Normally traffic from pfSense itself would always be allowed out:
# let out anything from the firewall host itself and decrypted IPsec traffic pass out inet all keep state allow-opts tracker 1000010015 label "let out anything IPv4 from firewall host itself" pass out inet6 all keep state allow-opts tracker 1000010016 label "let out anything IPv6 from firewall host itself"But those are not 'QUICK' rules so you can block that traffic with user rules if you really need to.
You need to apply them as floating rules as that's the only place you can set direction 'OUT'. You can use 'this firewall' as the source there to do so.
Doing that will prevent pfSense checking for updates or fetching packages and downloading the bogon list. It's not recommended.Steve
-
Thank you for the response Stephen. Please forgive my noobness. Any floating rule that I try to make (quick or not) to block "all out from this firewall" out of my WAN interface also blocks ALL traffic from my NATed subnets. It seems that I cannot send ANYTHING out WAN with such floating rule in place.
I know that it is not recommended to block all from pfSense, but it is a hurdle for me. If I can accomplish this then I will fine tune it and allow ONLY the traffic that I want into/out of my pfSense host box and not just everything. I do not like default "allow everything" even if it's from my own, trusted firewall.
I appreciate your patience with me. -
Mmm, yes on the WAN side I guess it's matching after NAT so sees the source as 'this firewall'.
I'm not that familiar with the rule order out on WAN it's not something I ever usually deal with. In the opposite direction NAT is applied before the firewall rules.
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-processing-order.htmlCan we see a screenshot of the rules you added and whatever is showing as blocked in the firewall log?
Steve
-
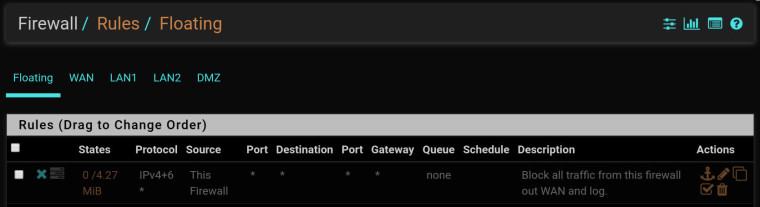
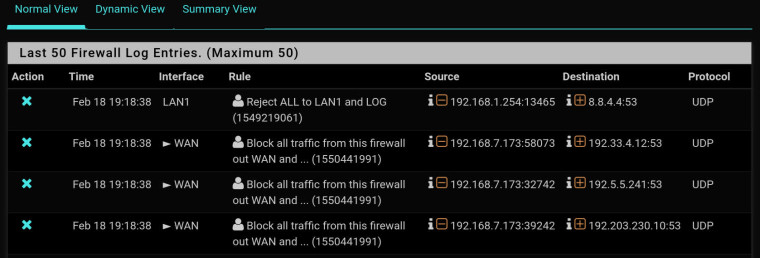
-
Hmm, about the only way I can see that working is if you add a virtual IP on the WAN and use that as the translation address for traffic from the LAN. Then you can add a pass rule for that above the block rule for everything from 'this firewall'.
Steve