Continuous data traffic to WAN
-
Dear users,
Since this is the first time I'm using pfsense, I'm testing it.
Today I noticed that with hardware on, there is continuous data traffic to WAN interface, how I can show you in this video:
https://cdn.dampc.ga/ctv/pfsense-traffic.mp4
When I recorded the video, all LAN interfaces are disconnected.And I noticed that the internet speed is lower using pfsense, compared to a normal router.
Why does my hardware continuously transmit data to the internet?
Thanks
-
There is always traffic on your WAN. Always.
-
Apart from whatever data is arriving on that link, which could be anything, there are also the gateway monitoring pings that are sent out at .5s intervals by default.
https://docs.netgate.com/pfsense/en/latest/routing/gateway-settings.html#id1
Steve
-
@dam034 If you are concerned about how much traffic there REALLY is, check the Status -> Traffic Graph page and filter by Remote. It will show you EXACTLY which IP addresses the traffic is going to/from.
As mentioned above, your ISPs gateway should pop up regularly at the very least as its used to check the connection is working.
You may also see other traffic from bots on the Internet checking if you have any exploitable servers on your connection. This is perfectly normal and pfSense will block that traffic at the firewall.
-
The fact is that this test machine is behind a NAT router, and I didn't forward any port, so the traffic is all outgoing, from the pfsense machine to the internet.
The interval isn't 5 seconds, but it is continous.
Is it possible to disable this?
Thanks
-
@dam034 said in Continuous data traffic to WAN:
The fact is that this test machine is behind a NAT router, and I didn't forward any port
Says who... Where is the sniff? Who says your nat router wasn't sending out traffic? Who says other devices on the same L2 as your pfsense wan not sending out broadcasts, multicast, arps, dchp, ssdp, wsd, stp, lldp, cdp, etc. etc..
If you actually want to KNOW what the traffic is - then sniff on pfsense wan.. Post up the capture and we can discuss what we see.
-
The gateway monitoring ping is .5s inteval not 5s. You disable it by editing the gateway in System > Routing > Gateways and checking 'Disable gateway monitoring.
But you will still traffic on that interface. Any broadcast traffic on that subnet will hit it for example.
Steve
-
We can not give you any advice based on a video of a blinking LED. Run a packet capture and see what's really out there. (Probably broadcasts, ARP, gateway monitoring, etc.)
-
@derelict said in Continuous data traffic to WAN:
We can not give you any advice based on a video of a blinking LED.



-
@dam034 said in Continuous data traffic to WAN:
The fact is that this test machine is behind a NAT router, and I didn't forward any port, so the traffic is all outgoing, from the pfsense machine to the internet.
The interval isn't 5 seconds, but it is continous.
Is it possible to disable this?
Thanks
Then you just answered your own question, as others have said it will be broadcast traffic from the LAN.
All network ports on my LAN blink like crazy because of things like my DLNA servers, routers uPNP, arp, discovery protocols from my TV, surround receiver, ShieldTV, etc.
There is lots of background traffic on any LAN because everything has to be "smart" and auto-discover each other.
-
Thanks for your replies, but I fix the issue thanks to the solution of @stephenw10
This is the gateway page:
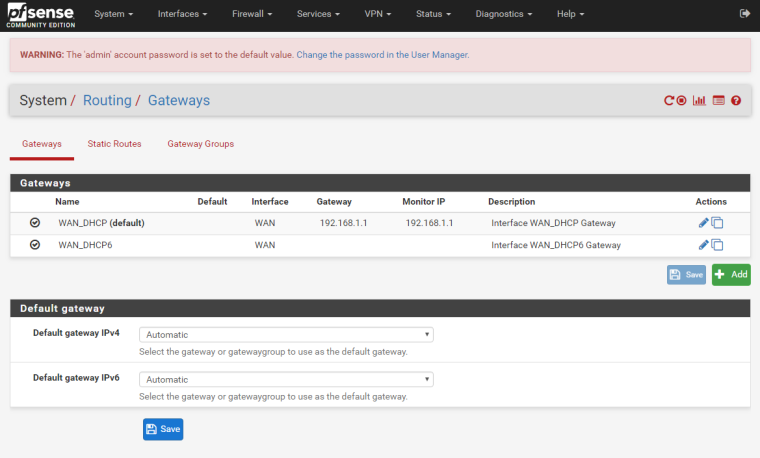
I temporarily disabled the monitoring and the traffic has been reduced to zero.
I didn't know the monitoring was going to 192.168.1.1, but I thought the traffic was outgoing to the internet. Now I re-enabled the monitoring, because I know where the traffic is directed.I solved the issue, but now I discovered another different issue, should I have to open another topic or I can continue here?
Thanks
-
Start a new topic if it isn't directly related to this problem.
-
Today I found another problem, this is the hardware configuration:
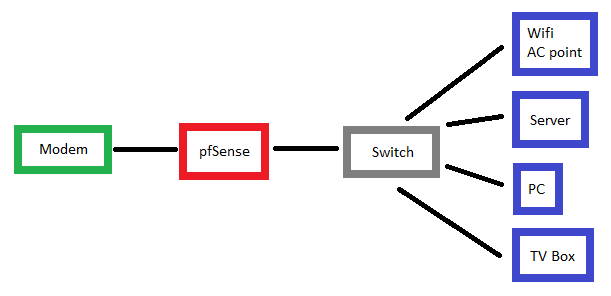
The tv box has a problem: sends continously data traffic (only when it is on).
With old router I saw all the led in switch blinking, and in the router only the port connected to the switch was blinking.
Now, with pfsense, I can see in the switch only tv box and pfsense led blinking, and in the modem also the led to the internet connection is blinking.
I think the tv box sends continuous broadcast (and/or multicast) frames.
Since I can't block this in the tv box, I want to block broadcast (and/or multicast) frames exiting the LAN in the pfsense machine.
I know I have to add a rule in the firewall, but I don't know what I have to set.What can I do?
Thanks
-
Your TV box is going to be noisy little SOB for sure..
Yup prob lots of multicast traffic, etc. One of the big reasons to segment your network into vlans, ie L2 broadcast domains is to keep such traffic away from other networks.
Put your TV Box on its own segment if you don't want your other devices to see this broadcast/multicast traffic.
If your switch or AP doesn't block this traffic such traffic can for sure kill a wifi network.. So for sure you would want to make sure that multicast traffic doesn't go out your wifi unless "needed" multicast traffic over wireless is almost always sent at the lowest datarate.. So even if not "lots" of traffic its going to slow down the wifi overall since its a shared medium.
-
I don't know if the traffic is multicast or broadcast, and if possible I'd like to see in the pfSense webGUI which type of traffic is. Have I to see the states?
I use the tv box to see on the TV some contents stored in the server, so all the devices have to stay in the same LAN, so no vlan.
About wifi, the AC point blocks all multicast and broadcast frames in both interfaces (ethernet and wifi).
So I want to prevent that these frames exit the LAN, to avoid congestion in WAN connection, because in LAN I have 1000mbps, in WAN only 30mbps.
Which rule have I to add to the firewall?
Thanks
-
@dam034 If your switch is smart (managed) and your "Wifi AC point" supports VLANs and multiple SSIDs, you can easily separate all this traffic. You have to read up on how VLANs work, obviously...
Jeff
-
Multicast and broadcast don't pass a router in the first place... So you don't have to worry about it flooding your wan..
As to your server and tvbox having to be in the same L2... Nonsense - you might not be able to use whatever broadcast/multicast discovery method your using now... But I stream stuff from my "server" to my TV every day all day and they are in different networks.
If you want to see what kind of traffic your tvbox is spewing - just do a sniff (packet capture) on pfsense lan interface under the diag menu.
-
I still don't understand why you consider any of this a "problem".
You will ALWAYS see traffic on the WAN, either from people probing your IP from the Internet, the PPPoE session to your ISP, or your IP address being refreshed over DHCP.
As for the LAN, my LEDs flash day and night, the amount of bandwidth its actually doing is microscopic. It will have zero impact on your Internet speed and be immeasurably small on your LAN speed.
Unless you have identified an actual issue with it causing problems on your LAN, blocking that traffic will only make using your devices more complicated as its there to make detecting devices on your LAN completely automatic.
Even my main smart managed switch and pfSense itself broadcasts its own traffic as I have uPNP enabled (for specific IP addresses only). Its how these devices are designed to work.
-
It's 2AM. Everyone's asleep but me. I am not chasing blinking LEDs.

-
@Derelict said in Continuous data traffic to WAN:
It's 2AM. Everyone's asleep but me. I am not chasing blinking LEDs.

It's morning here;,so I've been looking for an hour or so at your video : no red lights, all looks good to me ^^