DNS Firewall Rules
-
Hey guys. I'm currently using a PiHole appliance on my network and I wanted to ensure that all DNS traffic on my local network is being forced to route through PiHole. I saw this very informative article that demonstrated how to force DNS traffic through the PfSense firewall itself.
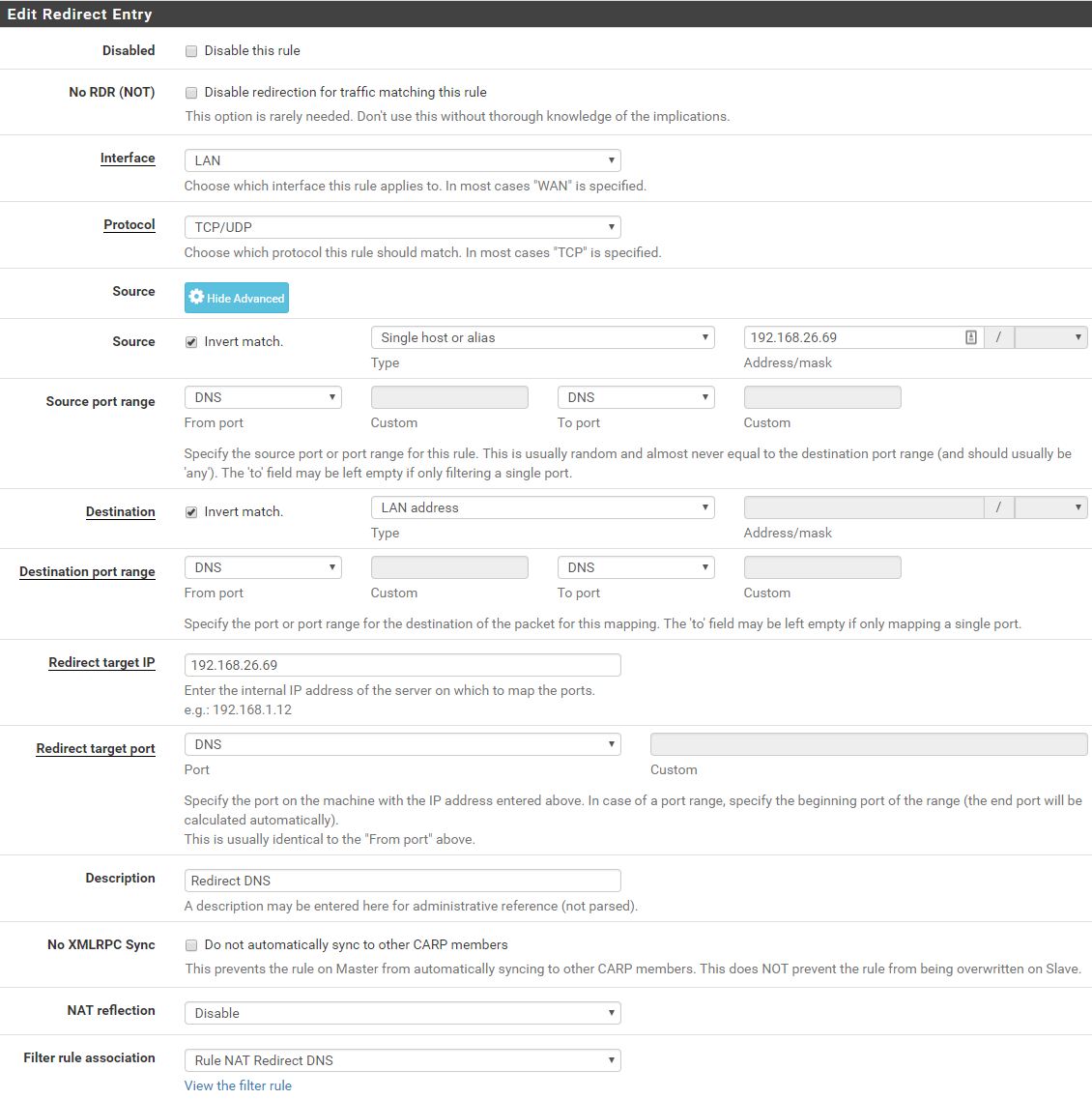
I assumed I could modify it to instead redirect all DNS traffic to the PiHole, but I have confirmed that I can in fact change my workstation's DNS to 4.2.2.2 as an example and I no longer have Ad Blocking. Please see screenshot for modified firewall rule. I'm probably missing something obvious, so any help will be welcomed. Thanks.
FYI: My PiHole appliance is using 192.168.26.69.
-
you can not redirect traffic like that.. If you want to redirect to your pihole, then put your pihole on a different segment than lan.
Or redirect to pfsense (be it unbound or dnsmasq your using on pfsense) and then have it ask your pihole. Notice in that article you link to
"Redirect Target IP: 127.0.0.1" -
Use that doc to force all local DNS to be captured by pfSense. Then either:
-
Configure DNS Resolver in forwarding mode and set it to use your pihole by putting pihole IP address in System - General Setup - DNS Servers, or
-
Disable DNS Resolver, enable DNS Forwarder and set it to use your pihole by putting pihole IP address in System - General Setup - DNS Servers
-
-
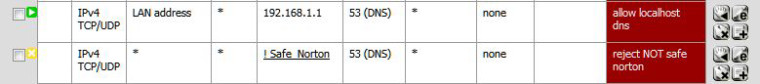
I don't know what pihole is. But I used to use open dns and norton dns for my kids. I made an alias of all the lan ip addresses the kids used (I set static mappings in dhcp), an alias for the norton/opendns ip addresses and an alias with all pc's which could use any dns. then on the lan interface made a top level rule to allow the alias to go anywhere access followed by a rule that stopped all other packets hitting the lan interface that were heading to the router on port 53. This blocked everyone but the ip's in my allowed alias. The final rule was to allow traffic on port 53 if the traffic was headed to an approved ip address in the alias.

May help, may not.
-
@mrwaltman said in DNS Firewall Rules:


If those are current screenshots your in dire need to upgrade pfSense.
-
@kom said in DNS Firewall Rules:
Use that doc to force all local DNS to be captured by pfSense. Then either:
-
Configure DNS Resolver in forwarding mode and set it to use your pihole by putting pihole IP address in System - General Setup - DNS Servers, or
-
Disable DNS Resolver, enable DNS Forwarder and set it to use your pihole by putting pihole IP address in System - General Setup - DNS Servers
I tried this and it still let me manually define an external DNS address and Ads were not being blocked. :-(
-
-
@middge said in DNS Firewall Rules:
@kom said in DNS Firewall Rules:
Use that doc to force all local DNS to be captured by pfSense. Then either:
-
Configure DNS Resolver in forwarding mode and set it to use your pihole by putting pihole IP address in System - General Setup - DNS Servers, or
-
Disable DNS Resolver, enable DNS Forwarder and set it to use your pihole by putting pihole IP address in System - General Setup - DNS Servers
I tried this and it still let me manually define an external DNS address and Ads were not being blocked. :-(
If you simply are trying to block ads, then why does manually being able to change the DNS setting matter? Simply don't change it. If you are trying to get users you have minimal control over to use a specific DNS provider, then you will want to create some rules on your LAN interface that block everything inbound on TCP and UDP ports 53 unless it is directed at whatever internal DNS you want to use (as others have suggested above, this could be your pfSense box running Unbound in forwarder mode or your pihole server iself). So with this kind of setup, any user who manually changes their DNS server IP will get nothing but DNS lookup timehouts.
-
-
@grimson
Why? Seriously, why?I am on newest version, that is at the ex's place. Lol, she would not let me have my box because she thought it had private/sensitive info of hers on it! Like, umm, facebook posts or something hahaha.
But really, are you meaning because of the router vulnerabilities or the rulesets?
-
@mrwaltman said in DNS Firewall Rules:
Why? Seriously, why?
Either you are trolling, or all hope for you is lost if you have to ask this.

-
@bmeeks said in DNS Firewall Rules:
If you are trying to get users you have minimal control over to use a specific DNS provider, then you will want to create some rules on your LAN interface that block everything inbound on TCP and UDP ports 53 unless it is directed at whatever internal DNS you want to use (as others have suggested above, this could be your pfSense box running Unbound in forwarder mode or your pihole server iself). So with this kind of setup, any user who manually changes their DNS server IP will get nothing but DNS lookup timehouts.
This is exactly what I was looking for. Thank you.
-
@middge said in DNS Firewall Rules:
@bmeeks said in DNS Firewall Rules:
If you are trying to get users you have minimal control over to use a specific DNS provider, then you will want to create some rules on your LAN interface that block everything inbound on TCP and UDP ports 53 unless it is directed at whatever internal DNS you want to use (as others have suggested above, this could be your pfSense box running Unbound in forwarder mode or your pihole server iself). So with this kind of setup, any user who manually changes their DNS server IP will get nothing but DNS lookup timehouts.
This is exactly what I was looking for. Thank you.
You're welcome. Just note that this method is not foolproof. If someone has access to a DNS server that uses TLS, then you also would need to block port 853. There are other possibilities as well. For plain vanilla non-skilled users, the method I provided is effective. For someone with a bit of skill and the brains to search on Google, they can eventually find a way around. Then it becomes a whack-a-mole game.
-
Come on man. I'm not trolling. You said,
"If those are current screenshots your in dire need to upgrade pfSense"
I said why, and was serious, and also asked is it because of router vulnerabilities or because of the ruleset, which is what you "quoted" by including it in your response.I don't need to know the exact vulnerability. I'm sure there are some. But you weren't exactly clear on why I am in dire need of an upgrade.
If you want to see this as trolling, so be it. Regardless though, I won't upgrade that machine because I would be accused of something illegal I am sure if I did, sad as that is. Crazy ex anyway.
-
It's always best to keep it updated. If your ex is that crazy, why are you managing her firewall?
-
Yeah, on a network device like pfSense I agree. I was asking because the images of the rules were quoted, and it wasn't clear if I had made a really bad error in the rules or if it was just the version being used.
As for the ex, nope, I don't manage it at all. I exported all settings but don't have a box currently at my own place, so I log in to reference it. Haha, she demanded my password for it, I said nope. Told her I would give her a different router for it, she said no. She has no idea at all about what it is haha, only that I want it, and therefore cannot have it.
Regarding updates though, I don't update anything unless there is cause to do so. From router to os to bios, unless there is a definitive security issue, it stays the same. Been bitten WAY too many times by auto updating. Had a mikroTik routerboard that did not get an update, ended up being rooted by someone in china. Reboot cleared it out, but was a good lesson in not being complacent in staying up to date on what is needed.
-
Your posted screens looked like the old red theme from the 2.1.x days. And yes, there are definitive security issues with older versions. Remember that everything is based on FreeBSD, so when that gets patches then pfSense needs them too.
What version are you running?
Good luck with your ex.
-
That box is
2.1-RELEASE (i386)
FreeBSD 8.3-RELEASE-p11I'm helping a gal who owns a business who is on a new netgate 5100 which is current build. If I ever get around to wiring my new place with CAT6 I will build up another box myself with the latest, probably one of those little atom based units.
Thanks. I liked my old box, had good hardware and was really quiet. Has a ton of squid stuff in it, kept my kids safe for many years. Smartphones changed everything, but life move's forward :)
-
Wow. Version 2.1 was released mid-2013.
https://docs.netgate.com/pfsense/en/latest/releases/versions-of-pfsense-and-freebsd.html
-
Yeah if memory serves there was an issue with maybe 2.3 and I had to reinstall everything from scratch. I can't remember what it was, it was a long time ago now. It might have had something to do with schedules or SARG.. I just can't remember but I know when I upgraded I had to reinstall all over, and thankfully I had backed it all up.
2015 was the last time I was there to keep it up I think. I check the box once in awhile, it doesn't spam traffic so maybe it's not been compromised. I originally put it in for both the kids customized rules and to maximize my CoD/BF playing. Boy, did it ever smash the DLink Gamer Lounge I had back then... ah, the good ol' days.