Bind webGUI only to certain interfaces
-
If you want to use 80 elsewhere, its better to change the gui port not use 80 and also disable the 80 redirection to https for the gui.
-
@dam034 said in Bind webGUI only to certain interfaces:
So visiting http://wan-ip/ I will see the web server or webGUI?
It will take you 30 seconds to answer that question ;)
Btw : ok, I agree, easy initial GUI access on port 80 from LAN exists so you can take ownership of your pfSense installation.
You're ought to install a cert - one that will be accepted by your browser **, install it into the GUi, and switch the GUI to https. This https access isn't necessary port "443".
It's like running a remote Linux/FreeBSD remote server : initially, you'll be handed over a user/password (like root/######). You ditch the root access, blow away user/password access, install private/public keys on server and your ssh client, and then your admin access is somewhat more safe.** obtain one from a certificate authority - or generate your own, and import necessary files into your browser so it won't complain.
-
If I understood good, I can't disable webGUI on WAN interface, but I can:
- change the webGUI to another port (e.g. 28428)
- forward the port 80 and 443 to web server
- disable webGUI redirect to https
- set strong username and password
Am I right?
Thanks
-
Out of the box the web gui is NOT available from the WAN, no matter what port it listens on. Unless wan is the only interface pfsense has.
You can yes access the wan IP from lan side depending on how the rules are set.. If you do not want an IP to access the web gui via the wan IP from the local networks, then block it with a firewall rule.. Turn off the antilock rule if on the lan and only allow access to web gui port from your IP..
-
@dam034 said in Bind webGUI only to certain interfaces:
change the webGUI to another port (e.g. 28428)
.....
disable webGUI redirect to httpsYou can't disable WebGUI.
You should do this :
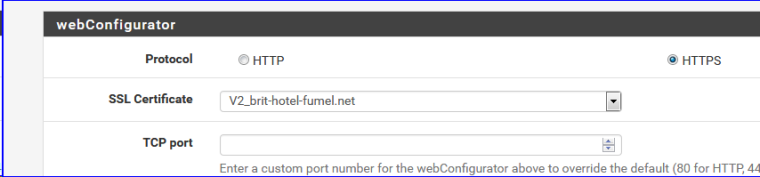
==> check the HTTPS button.
Done.
And before you switch to https, using the default "443" port or whatever (or close to what ever - see TCP port) port at your choice, you should prepare a certificate. See System => Certificate Manager.
If your imported the certicate from an certificate authority, you'll be fine right away. If the certificate is signed by your pfSense itself, export it and import into your browser (these days modern browser do not like self-signed cert anymore - importing them in the browser's trusted-list makes them stop yelling to you).Btw : If you use a cert, think about setting these
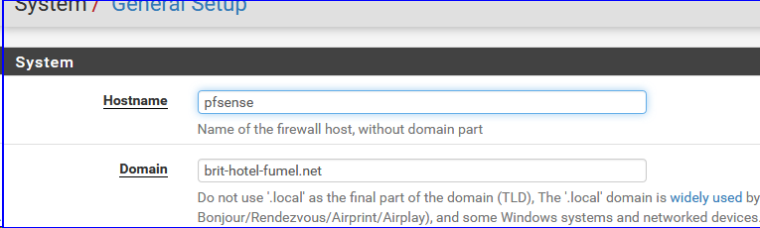
in consequence. -
Thanks for your replies.
Connecting with the data connection of my smartphone, I realized the webGUI isn't available on WAN interface, but is available from LAN interface visiting WAN IP.
About SSL, in LAN I don't need the HTTPS, but I can change the port of webGUI so the LAN users have less possibility to reach the webGUI. But I already know it's useless.
Now the question is reversed: if I will need the webGUI from the internet, can I enable it?
Thanks
-
@dam034 said in Bind webGUI only to certain interfaces:
if I will need the webGUI from the internet, can I enable it?
Yes you can - but its a REALLY BAD IDEA!!! If you need to admin pfsense from internet side it would be better to vpn in, then admin it through the vpn connection.
The gui will be available via the lan network with the antilock rules in place, no matter what port you change the gui too. You would need to turn off the antilock out rule, and then only allow the IPs you want to access the gui be it on the actual lan IP or another IP or even the wan IP from the lan side.
As to blocking users, its pretty trivial rule to block IPs you don't want to access the gui. But on the lan you have to disable the antilock out, then just create rule that blocks access to the gui port on firewall (built in alias) This will block ALL ips firewall, lan, wan, opt, etc..
-
Yes, I know it's a bad idea, and now I'm not thinking to do it.
I just want to know how to do it.
I have understood that there is an antilock rule which commands the webGUI.
Can you show me in what page I can manage it?Thanks
-
The anti-lock rule is on LAN, not WAN.
If you absolutely MUST access the webgui from over the WAN, I would strongly suggest source limiting the firewall rule to a subset of administrative networks/hosts (You can use a firewall Alias for this). Then you just pass TCP to WAN address on the webgui port you set in System > Advanced.
Nothing magical here.
-
The antilockout rule is ONLY On the lan interface, or on wan when there is ONLY the wan interface.
You can disable it here
System / Advanced / Admin AccessThere is checkbox to disable antilock out
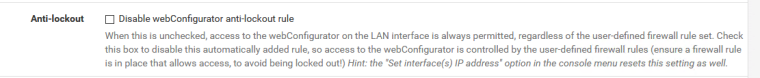
-
So now the webGUI isn't accessible from WAN, but if I create a NAT rule, it can be.
The NAT rule can accept connection from a subnet like 79.12.24.0/24 so only 254 IPs can access webGUI from WAN.
Am I right?
Thanks
-
You don't need a nat rule, just a rule to allow it on the wan to the wan address and the port the gui is on.
-
Thanks for the replies.
Now I want to ask the same informations about the SSH connection.
Should have I to open another topic or can I continue here?
Thanks
-
What is your question? That port will be allowed on lan as well for antilockout.
-
Just a moment.
I create a teporarily rule to enable the webGUI on WAN interface:
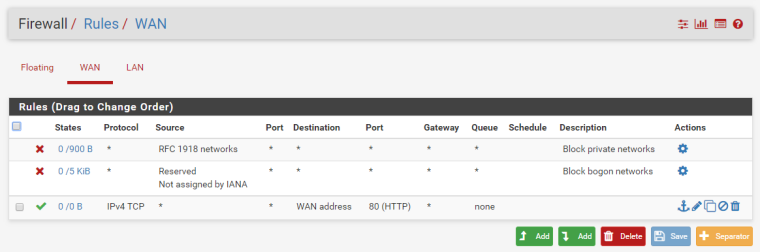
But visiting from my smartphone in data connection, I can't access it.
Am I wrong?
Thanks
-
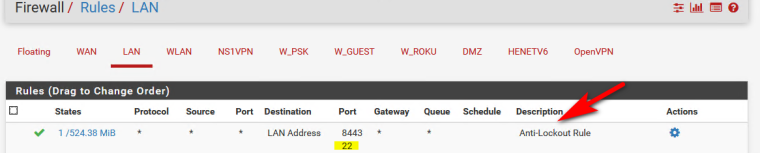
Does pfsense have a public IP on its wan, or its it behind a NAT? Its quite possible your ISP blocks port 80 inbound.. Many do on home connections, etc.
I don't see any hits on that rule - so traffic prob never even go to pfsense. that 0/0 tells me nothing has hit that rule
-
The pfsense machine WAN IP is private, and I'm now trying from another pc in the same LAN as pfsense's WAN interface.
Is there any mistake?
Thanks
-
@dam034 said in Bind webGUI only to certain interfaces:
The pfsense machine WAN IP is private, and I'm now trying from another pc in the same LAN as pfsense's WAN interface.
Is there any mistake?No mistake at all.
Look at your firewall rules.
The first rule is put in place 'automatically' when you check this option on the WAN interface.
Here it is :
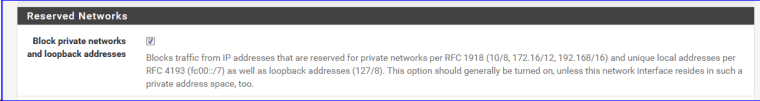
So, when this box is checked - yours is checked - local IP's like (192.168./16 10/8 etc) are blocked.
The counter in front of your first rule indicates it is blocking "something".
These must be your attempts to use your phone to connect to the GUI.When you use your phone, you use some real WAN IP (an address IPv4 that is addressable on the Internet).
The connection comes in on your first router, probably the one your ISP gave to you, or some other upstream device.
This device NAT's to the pfSense WAN IP - and this IP is a "RFC 1918" class IP.
pfSense, according to your instructions, blocks these IP's.Btw : before you ask : the second rule will not bother you, although it's a nice exercise to know who's triggering that rule ^^