Share your Experience
-
Downloaded ver 20.10 home
it's a nice experience
zero-to-ping is easy to follow
I must say that after some time playing with the CLI I don't miss a GUI anymore.
I tested it on my VMware with 8gb and 4 core, 2 x ixgben -driver e1000 (known issue, vmxnet3 does not work with mtu 9000)
the wan side is not free of traffic because I have pfSense with other servers and client running
so.. just to share a simple iperf3 after following the zero-to-ping without any network optimization
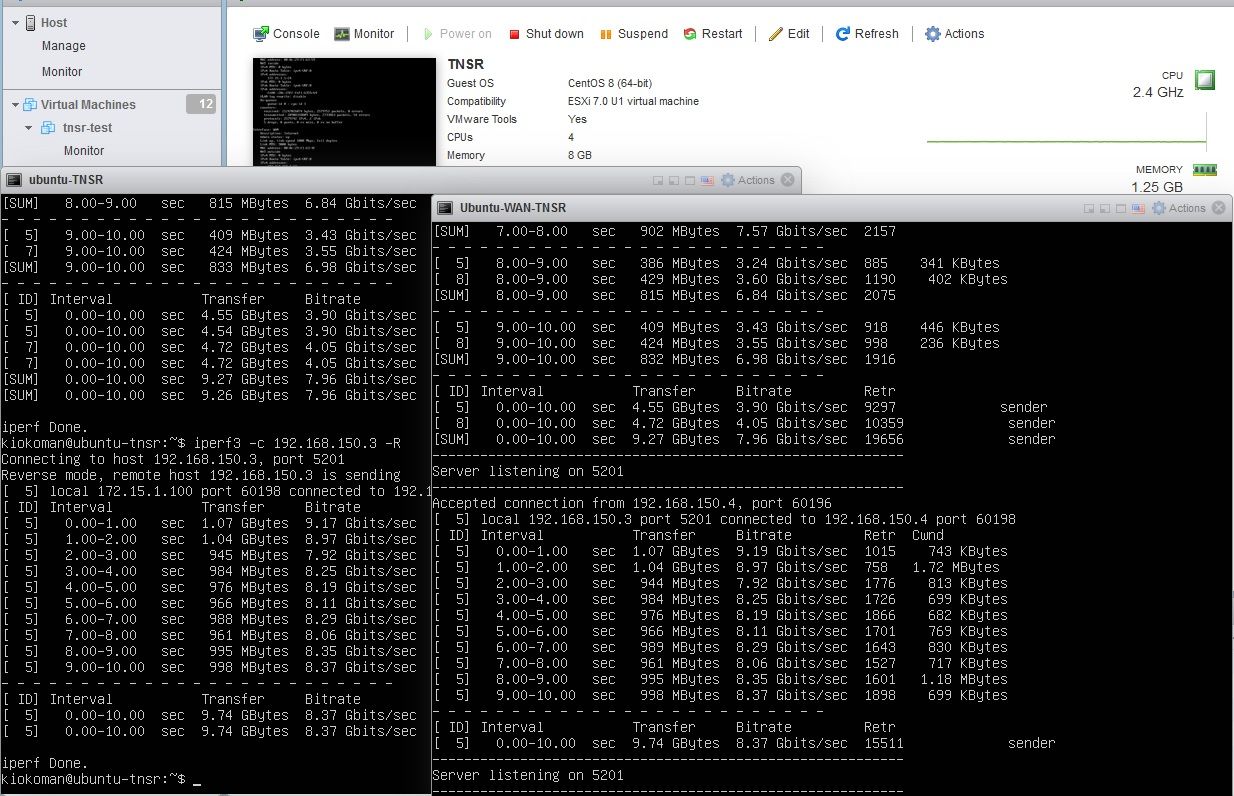
-
@kiokoman Maybe you can post a test with your pfSense speeds also, for comparison ?
Thanks -
In my use case all it needs is a GUI.
I will start to have nightmares if I have to configure all the firewall rules via CLI, configure various services like OPENVPN, IPSEC.Maybe in the future you can port pfSense GUI, customise it and add the new features for TNSR?
I like what IxSystems are doing with their TrueNas Scale, by porting the middleware to Linux.
I don't think it's the same with pfSense-->TNSR, but you asked use cases.
Thank you
-
@NRgia said in Share your Experience:
OPENVPN
There's no OpenVPN.
Maybe in the future you can port pfSense GUI, customise it and add the new features for TNSR?
AFAIK that's not the scope. Sure, one could add a UI that hooks into the API layer. But the whole system is done with automization and API capability in mind. Not to be single-user-UI friendly. Also as a high performance router, you normally don't change configurations that much.
I'd rather compare it with Ciscos ASR vs the ASA firewall. TNSR is more like a ASR on steroids that you also configure via CLI and it does one (core) thing really good - routing with SPEED. ACLs or rules are "meh" though. That's where ASA/firewalls come into play standing behind it.
So if you have a need for really high performance routing or tunnels (IPSec only) on things like border gateways or fast cloud uplinks etc. that are configurable via automation (ansible et al) TNSR really brings this! If you want firewalling and UI and rely on additional packages like HAproxy, special IDS setups or pfBlocker et al - then pfSense it is. :)
-
right, it is meant to work like on this diagram https://forum.netgate.com/post/922488
10G / 40 / 100 and up, like chattanooga ... area51... and so oni don't know who to tell this but i noticed that setting the root password during the install does not work
after the installation it reboots and i can't login with root, i must login with the additional user i created and with sudo passwd i need to change/set the password for the root account. -
@kiokoman said in Share your Experience:
i don't know who to tell this but i noticed that setting the root password during the install does not work
Which specific release did you see that on?
-
both 20.08 and 20.10
-
@kiokoman Ok thanks! Let me see what I can find out. To be clear this is on initial install?
-
@kiokoman Looks like that is on purpose. From our installation docs:
Security best practices dictate that it is best not to enable interactive logon for the root account. As such, the root account will be locked out after the installation. Use this process to add at least one alternate administrator account. -
ah good to know, that one slipped from my readings