Logging connections, not their content
-
I have a small NAT network behind a pfSense firewall (latest version). I have been told that something on my network is unexpectedly making frequent connections to an external system.
I would like to use pfSense logging to record every outbound TCP connection being made by any machine on my network (just for a day or two so I can look for patterns). For each connection I'd like to record the source and destination IP addresses and TCP ports at least (automatically resolving to hostnames would be nice). I don't need to record the data that flows across the connection.
Can someone suggest how I can achieve this?
My best guess is that I need to create a firewall rule that specifically matches SYN/ACK packets, and turn on logging for that rule. I've tried this but haven't been able to get it right.
I'd really appreciate an explanation of how to do this, or a pointer to a pfSense package that easily solves my problem!
Many thanks for any help.
-
If this is on your LAN network, for example, you can simply set the logging feature to "ON" in your firewall rule that passes all traffic out to the internet.
It's under Extra Options, in the "allow LAN to any" rule.
Be aware that you need hard drive space for capturing the log data. Then, when you are done logging, read the data with a syslog program, like Wireshark, then turn off the logging function in the rule. Or, for a simple look at the rule logs, you can look under Status -> System Logs, and click on the Firewall tab to see the data.
https://docs.netgate.com/pfsense/en/latest/book/firewall/viewing-the-firewall-logs.html
The only problem I can see with the above steps is if you've got lots of NAT rules, and lots of firewall rules. Then it might be harder to narrow down which rule you actually want to do the log capture in.
Jeff
-
@akuma1x thanks!
If I understand correctly this would log all traffic through the firewall, not just the creation of new TCP connections. Is that correct?
I don't have a problem with that if it's the best way to approach my problem.
Or am I misunderstanding -- will this approach actually only log connection setup, not the packets that flow once the connection is created?
Thanks!
-
Try it and see if it's got the data you're looking for. I just turned on the logging function on my "lan to any" rule, and it shows me what internal lan machines talk to which external machines, all by IP address.
If you happen to know which "external machine" you're looking for, it should be easy to see what internal machine is talking to it.
Jeff
-
@akuma1x said in Logging connections, not their content:
If you happen to know which "external machine" you're looking fo
Well, he said so :
@anmnz said in Logging connections, not their content:
something on my network is unexpectedly making frequent connections to an external system
An external system is an identified system.
For example :
I have this site test-domaine.fr.
It has these IP's :root@ns311465:~# host test-domaine.fr test-domaine.fr has address 5.196.43.182 test-domaine.fr has IPv6 address 2001:41d0:2:927b::15 test-domaine.fr mail is handled by 30 mail.test-domaine.fr. test-domaine.fr mail is handled by 20 mail2.test-domaine.fr. test-domaine.fr mail is handled by 10 mail.test-domaineI create a pfSense alias for the IP's 5.196.43.182 and 2001:41d0:2:927b::15 called "test".
I create a firewall pass rule on my LAN :
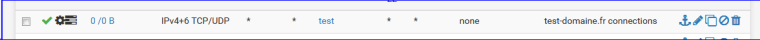
It's a pass rule.
It's logged.
Source : any.
Usage the destination : host : alias : "test"
Advanced option : SYN bits set (in and out)Now, I visit my test-domaine.fr usage a ... web browser.
Refresh the Firewall LAN rules list and check :
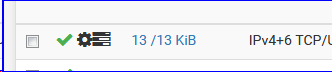
This means the rule has been "used".
Let's check the logs :
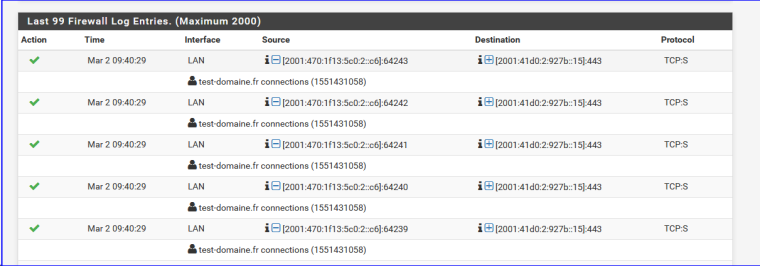
aha : it's a device using IPv6 2001:470:1f13:5c0:2::c6
root@ns311465:~# host 2001:470:1f13:5c0:2::c6 6.c.0.0.0.0.0.0.0.0.0.0.2.0.0.0.0.c.5.0.3.1.f.1.0.7.4.0.1.0.0.2.ip6.arpa domain name pointer gauche.brit-hotel-fumel.net.That device is the PC I just used to visit www.test-domaine.fr" !! The device (PC) has been identified.
I can see port numbers, so I can deduct used services (wbe server in this case), etc. -
@gertjan said in Logging connections, not their content:
Well, that's a little advanced... and BRILLIANT!

Thanks for the tips and the instructions. I didn't even think of narrowing the rule down that far. That's awesome! That would also limit the size of the log data file, since you've laser-focused it down so much to just the external machine on a single rule.
Jeff
-
Thanks @gertjan! I don't actually have the specific IP addresses my network is allegedly making connections to, but these instructions are excellent and showed me how to do what I wanted which is to log all outgoing connections from my network. Thanks very much indeed for taking the time!