Another OpenVPN TLS handshake failed issue
-
Yesterday I attempted to start setting up OpenVPN so I could connect my laptop to my home network when I'm not in the house. I have my home network separated out into a few different VLANs, which I followed most of this guide to do. Since I had success with that guide, I decided to follow this guide to complete my VPN configuration. I went through the whole process on pfSense and then installed the OpenVPN client on my laptop and exported the config file. My laptop attempts to make the connection, but I get the TLS handshake error after 60 seconds. I've looked at a lot of the other threads on here and even Googled, but nothing I've found has helped.
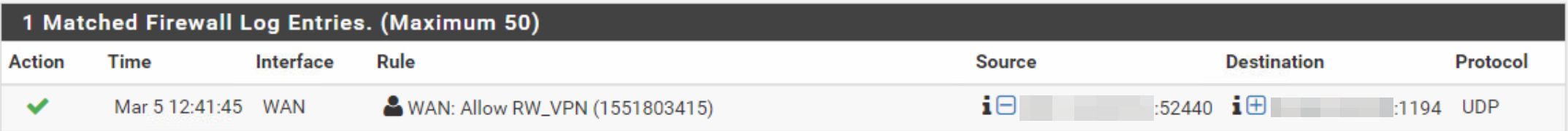
I changed the firewall rule on the WAN that allows the connection to log anything that hits the rule, and I can see the connection attempt making it to the firewall and being allowed:
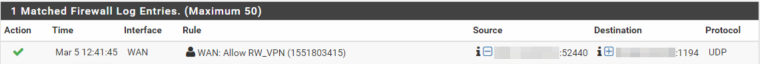
I took a packet capture from my laptop and the firewall, and I see the firewall and laptop communicating with each other, so the traffic appears to be flowing without anything being blocked. I do see in the packet capture on the client side a P_CONTROL_HARD_RESET_CLIENT_V2 and on the pfSense side a P_CONTROL_HARD_RESET_SERVER_V2. I did a Google search and found this post on StackExchange, but I'm not sure how to implement that fix on pfSense. It seems to me that pfSense is sending the traffic destined for the VPN client out the wrong interface, but I can't see a way to determine this or prove it or how to fix it. Any ideas where I could go from here?
-
Show your settings (screenshots) and OpenVPN server+client log.
-Rico
-
Here's the CA config:
Here's the certs:
OpenVPN config:
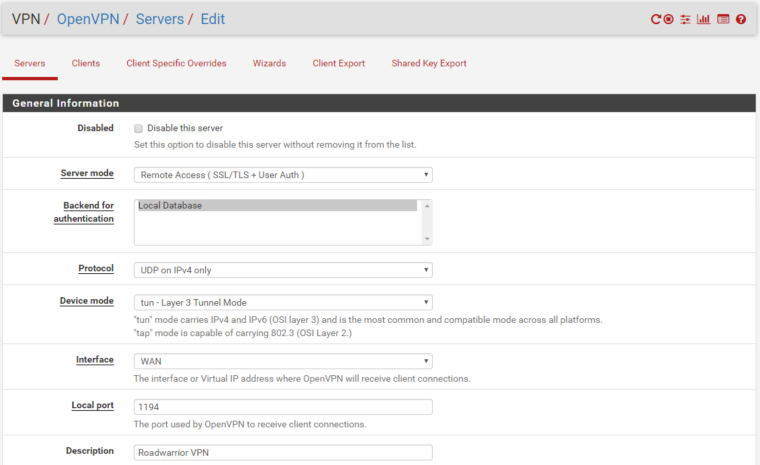

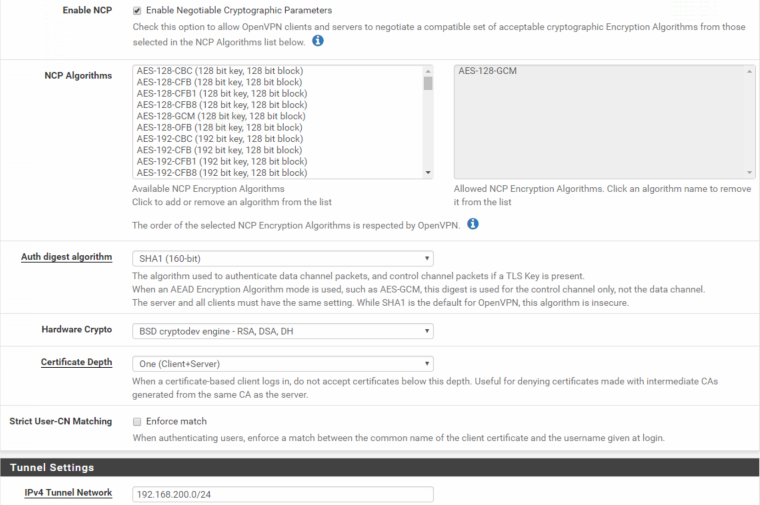
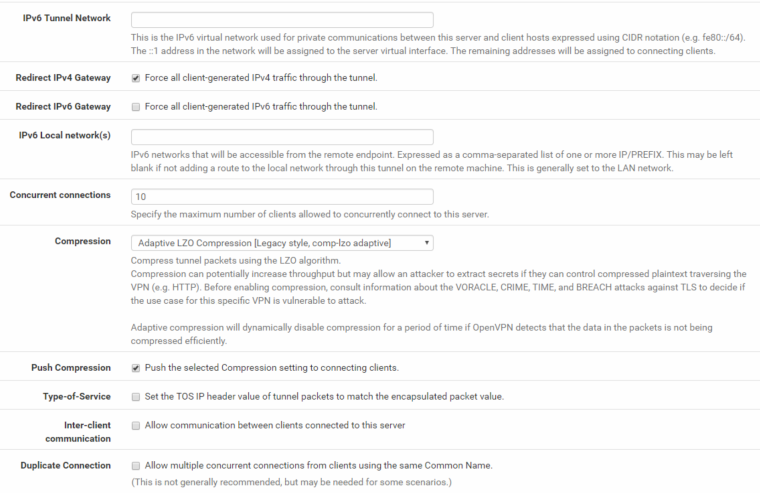
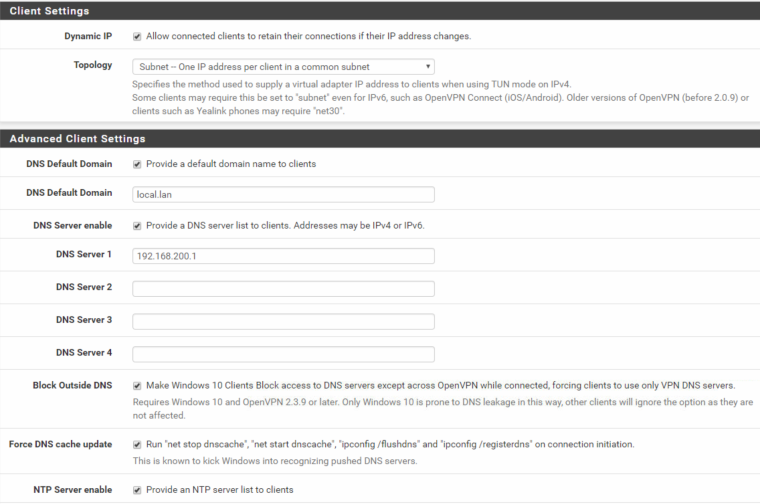
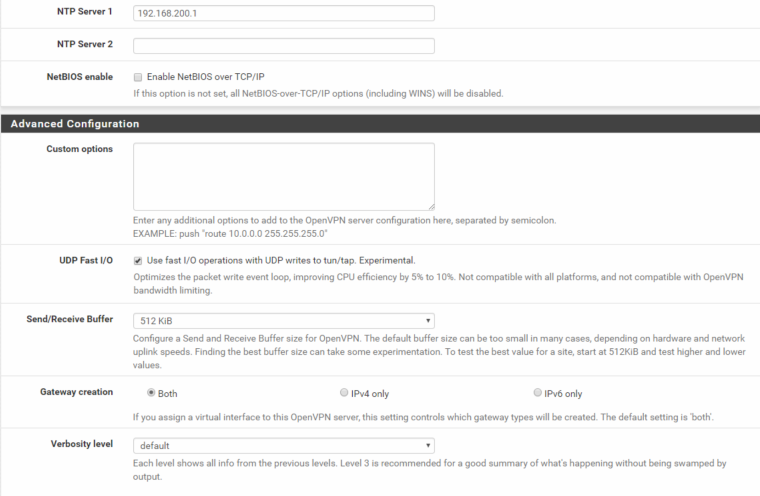
Interface assignment:
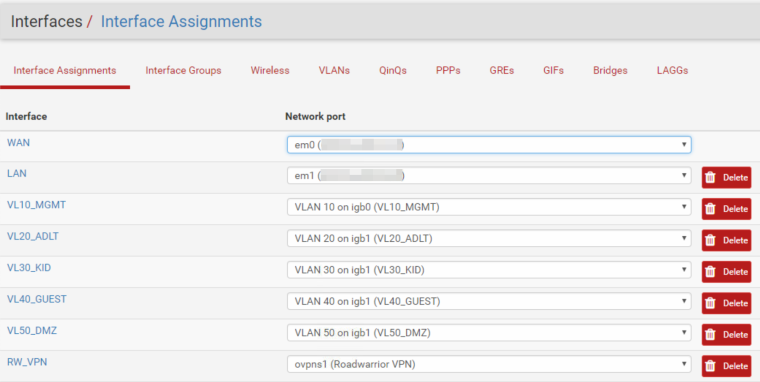
Gateway config:
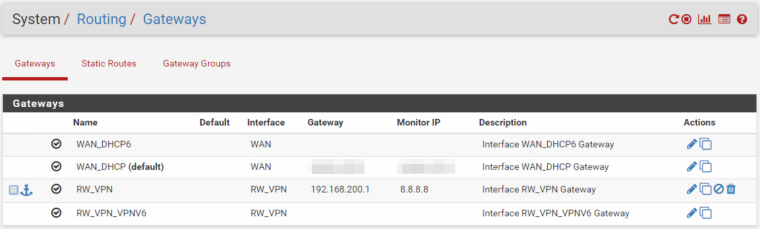
Firewall rules for RW_VPN:
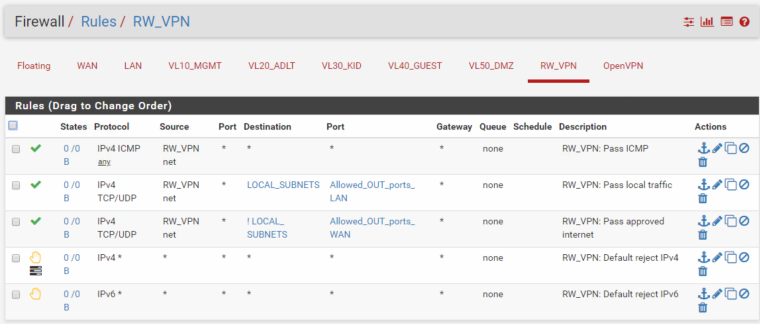
Even added this for the OpenVPN just in case:
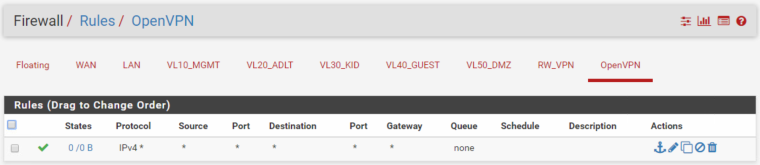
Firewall rules for WAN:
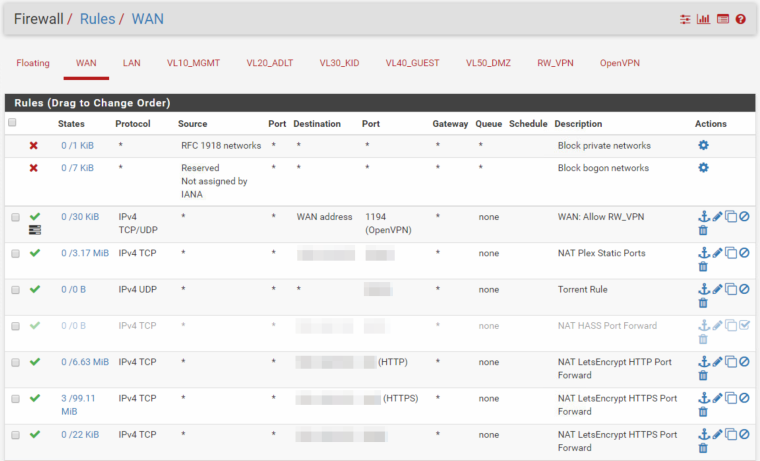
Added the RW_VPN interface to DNS resolver:
Added outbound NAT for the new VLAN:
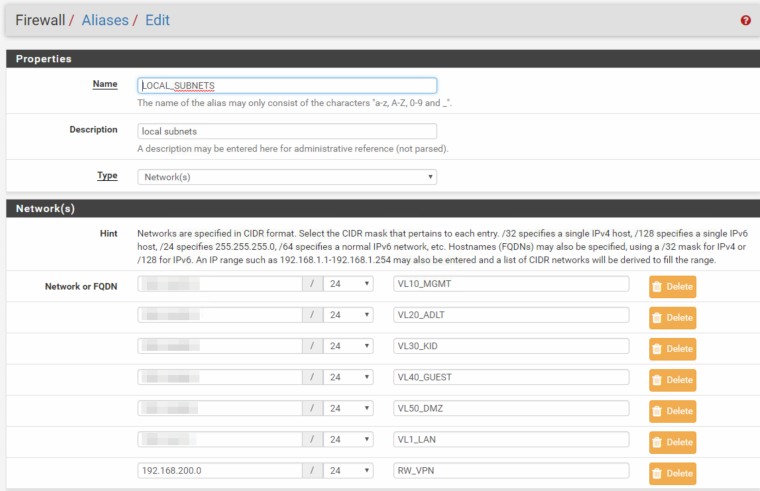
Updated my aliases:
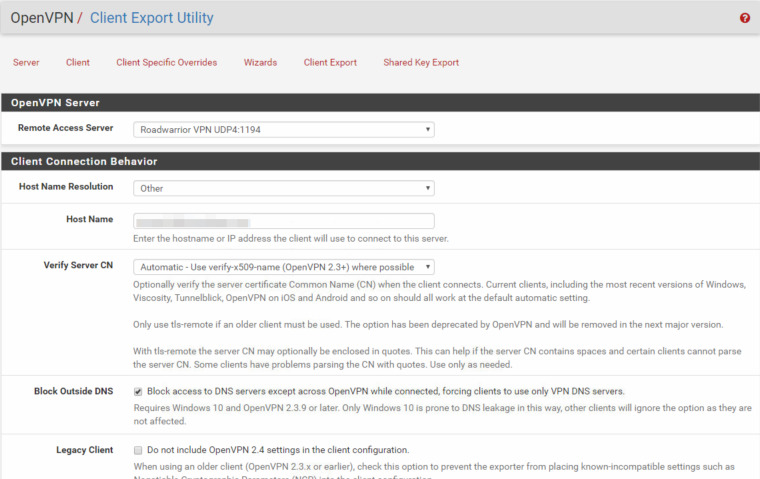
Client Export Config:
The OpenVPN client log shows:
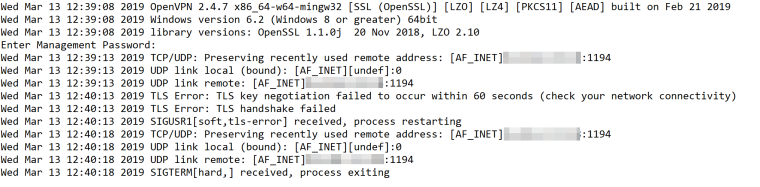
The logs in the pfSense GUI show:
The log file shows the same thing:
Mar 13 12:40:12 pfSense openvpn[5481]: 205.128.239.51:20640 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Mar 13 12:40:12 pfSense openvpn[5481]: 205.128.239.51:20640 TLS Error: TLS handshake failed
Mar 13 12:41:16 pfSense openvpn[5481]: 205.128.239.51:25518 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Mar 13 12:41:16 pfSense openvpn[5481]: 205.128.239.51:25518 TLS Error: TLS handshake failedI'm going to guess to get some more verbose logs I need to change the Verbosity level to 5 or higher?