VPN on VLAN working but disabling LAN traffic
-
I'm using Mullvad for my VPN provider. I'm having an issue where I can get the VLAN to route through Mullvad, but it kills my main LAN connection. I followed this guide to setting up Mullvad with pfsense https://mullvad.net/en/guides/using-pfsense-mullvad/. Let me discuss the steps I took to get to where I am at and see what is missing.
- Created VLAN 10 and gave it a description of IoT
- Made a new Interface assignment called IOT and put this VLAN 10 on it
- DHCP server is hading out addresses to this subnet so VLAN 10 is working
- Created a firewall rule for IOTnet to allow any to any
- Devices on VLAN 10 can get out to the Internet
- Created an OpenVPN client t Mullvad based on the guide above with the interface set to IOT
- Created a new interface assignment called OVPNiot and associated the Mullvad client to it
- Per Mullvad's guide, went to NAT, Outbound and switched it to manual.
- Copied the rule from the IOT subnet and duplicated it as per their instruction (see attached as result)
- Added their recommended DNS servers in the DHCP Server setting of IOT (not my regular lan)
- IOT devices are getting Internet
- LAN devices are not getting Internet. Funny thing is my stock trading program seems to be connected and receiving data. So perhaps this is a DNS issue.
What can I do to fix this so that IOT devices are connected to the VPN and my LAN not affected? Also I will need to disable the VPN at times to get through. It seems like disabling the OVPNIOT interface does the job. But how do I get my normal default DNS entries back in DHCP resolver (which is pfsense) for the IOT VLAN?
-
Set openvpn not to pull routes.
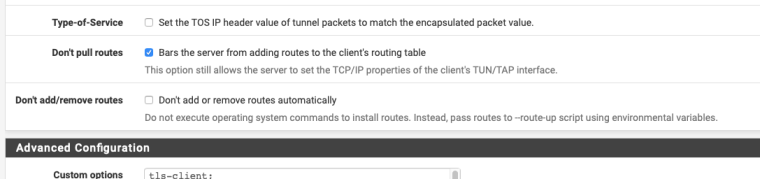
-
Also try Hybrid NAT.
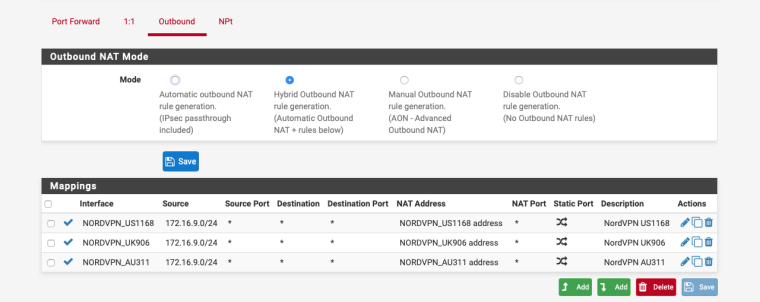
-
@nogbadthebad said in VPN on VLAN working but disabling LAN traffic:
Set openvpn not to pull routes.

This causes the VPN connection to not work. It makes my LAN work, but my IOT network does not get the VPN IP. So this does the opposite of what is happening now. I have it set to hybrid, and it seems like no change.
-
post your IOT firewall rules
-
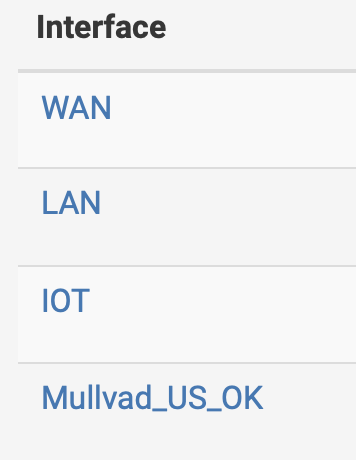
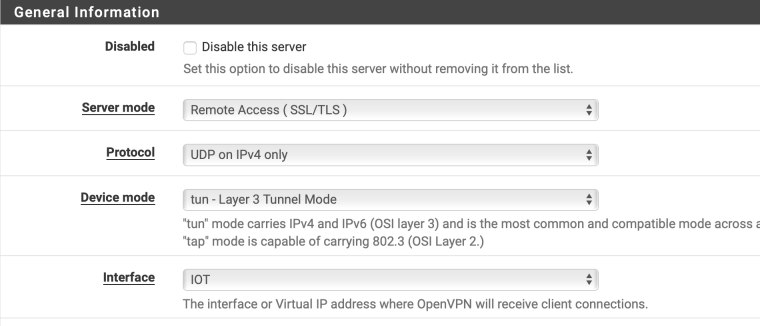
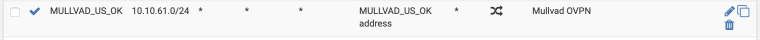
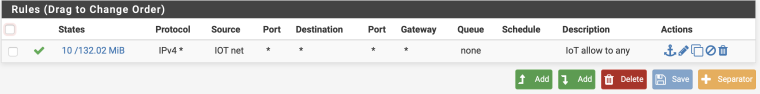
I posted my IOT rulles, my outbound Mullvad NAT, the OpenVPN client config that shows the interface it's on, and my list of interfaces.
-
As I previously mentioned you need to set the OpenVPN connection not to pull routes, without this everything will be routed out the OpenVPN interface, have a look at the routes and you'll see.
Set a gateway on the IOT outbound traffic rule to route out the OpenVPN interface.
Which is why "Also I will need to disable the VPN at times to get through"
-
I can try that. How do I setup a firewall rule for a gateway? Also, on the openvpn client for mullvad I have IOT as the interface. I’m guessing it should be that instead of WAN correct? Mullvad docs said to set it to WAN?
-
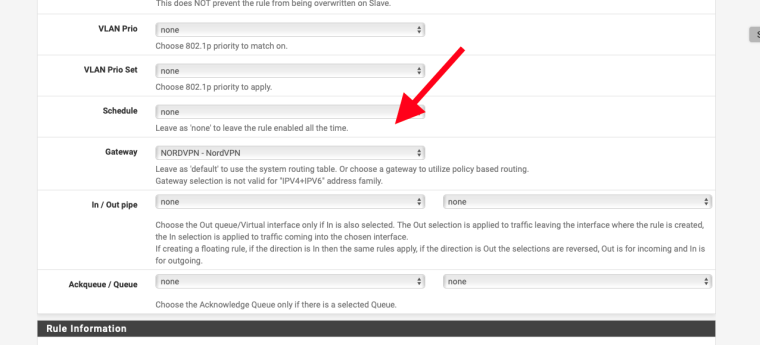
In the advanced options.
-
Thank you. That worked. I just created another rule above the IOTnet to any with this gateway. Then I can disable that rule as needed.