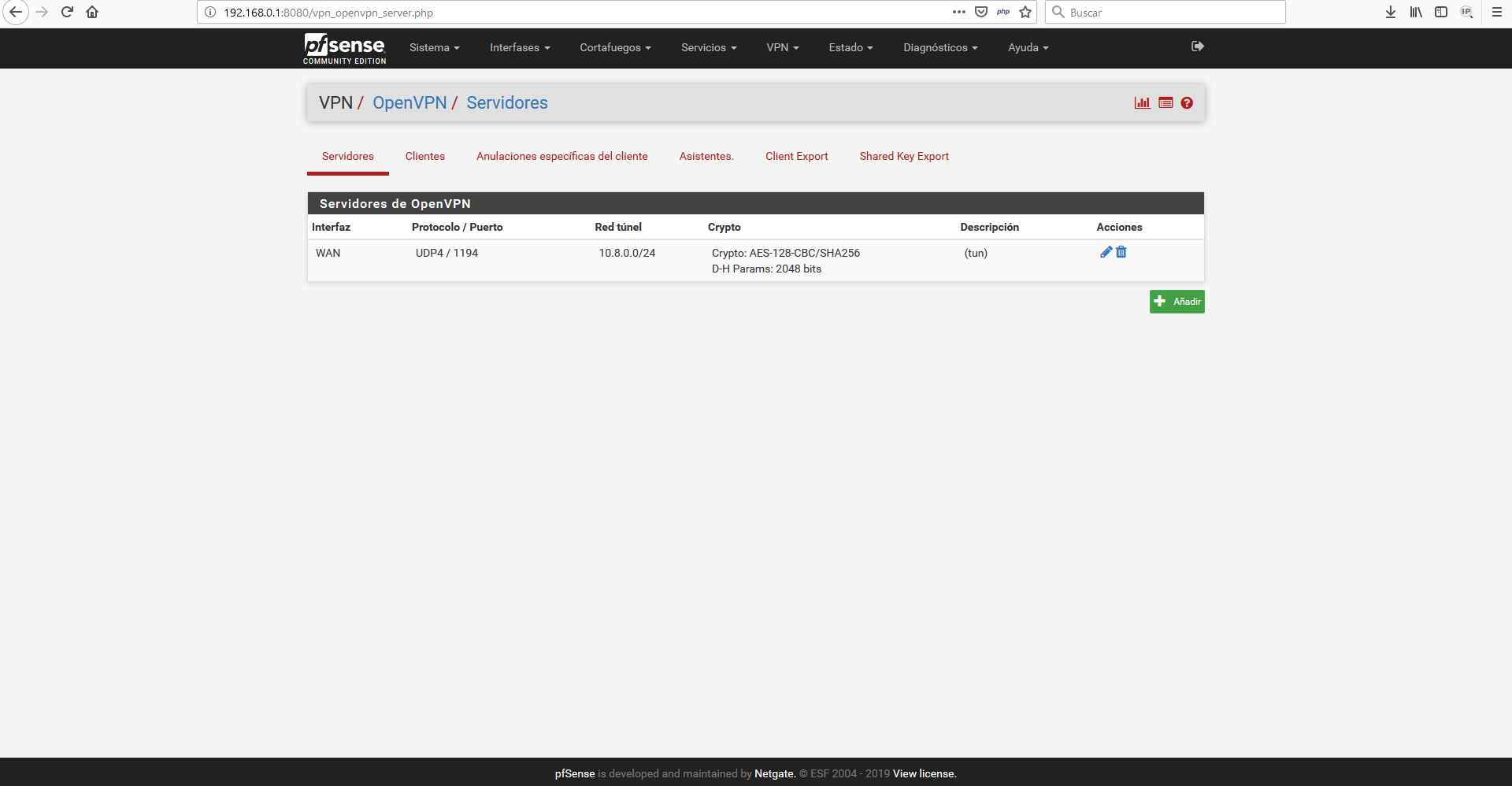
TLS Error: TLS key negotiation failed to occur within 60 seconds
-
Hi,
I get this error when I try to connect OpenVPN remotely.my pfsense configuration:ISP router:
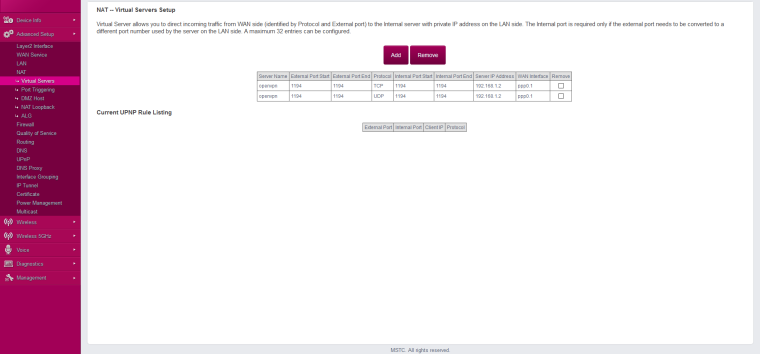
internal ISP router IP: 192.168.1.1 (192.168.1.0/24)
pfsense: WAN: 192.168.1.2
LAN: 192.168.0.1 (192.168.0.0/24)Firewall:
OpenVPN server config:
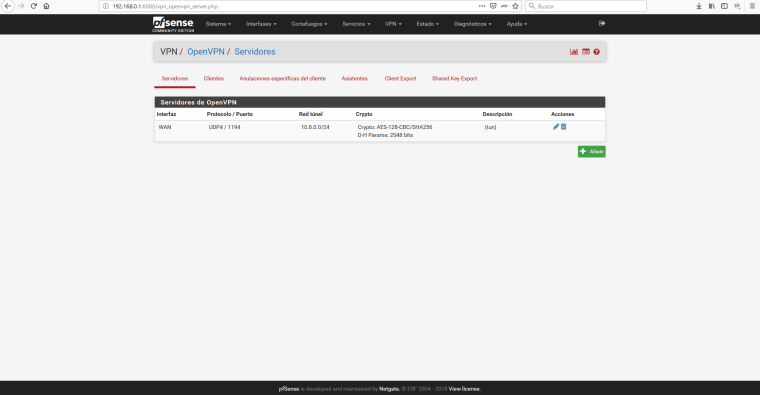
if I try in WAN pfsense network (192.168.1.0/24) with OpenVPN works very good. But if I try from internet, I cant access and have the TLS handshake failed
any idea??
thank you!!
-
You need to forward the OpenVPN port from your ISP router to pfSense.
-Rico
-
and this is in port triggering?
-
Sorry I was on mobile yesterday and did not saw your screenshots (no idea why).
I don't know your ISP router but the "Virtual Server" config looks okay. I'd remove the TCP line, you only need UDP there when running OpenVPN in default UDP mode.
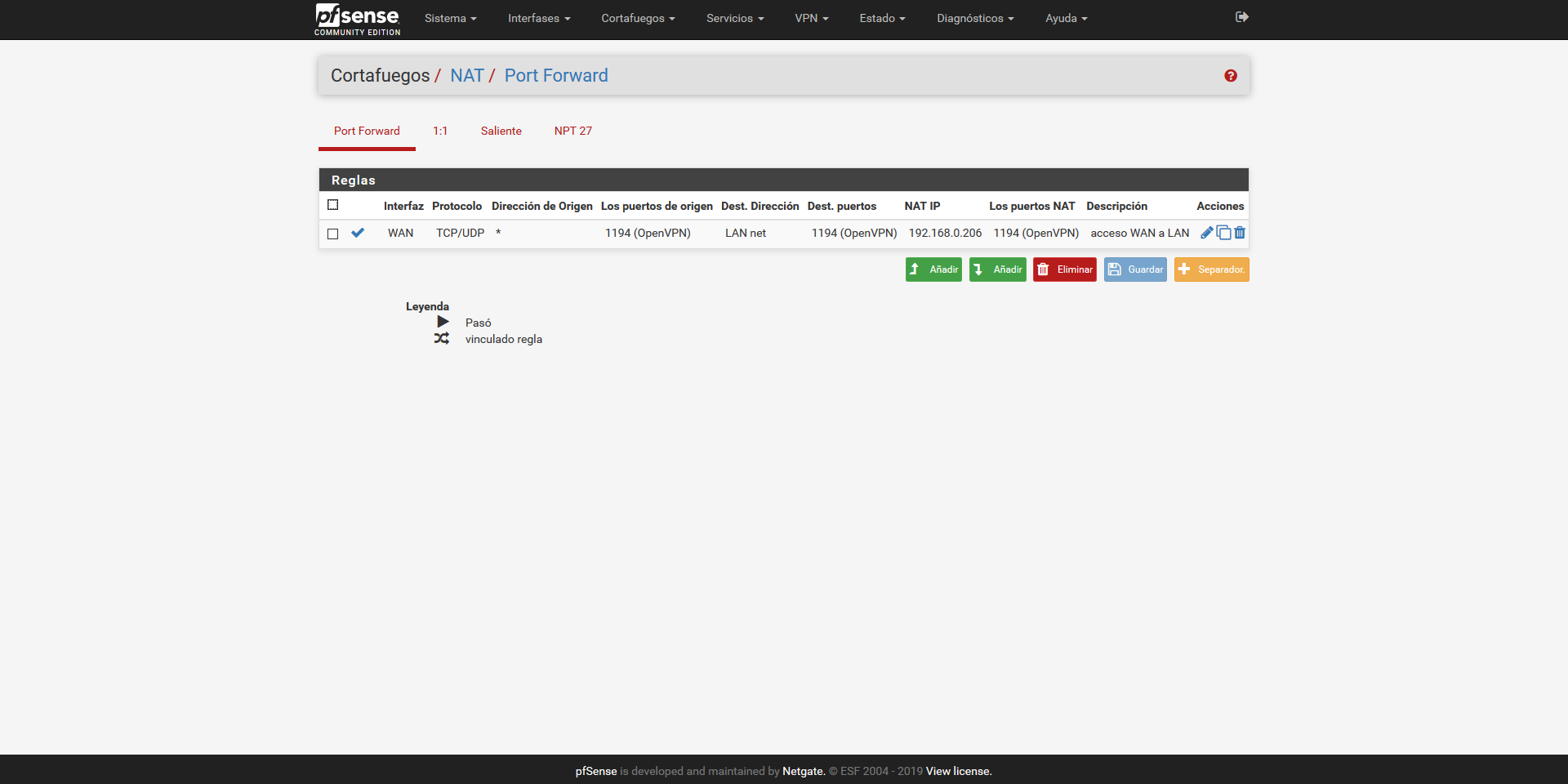
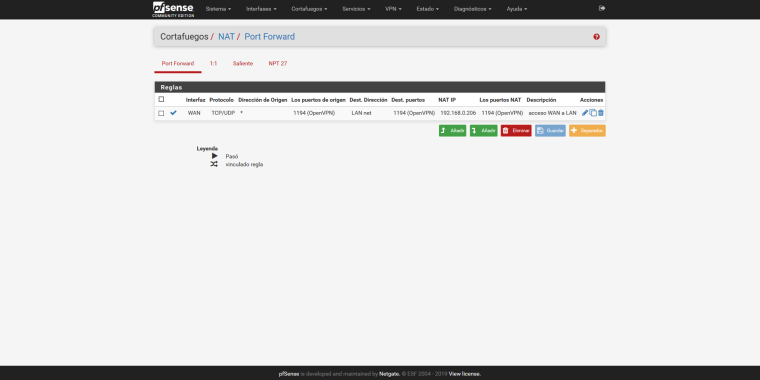
Wrong is your pfSense Port Forward. Running OpenVPN on top of pfSense only need Firewall Rules on WAN, no NAT/Port Forwarding.
What is 192.168.0.206 anyway?
Show your WAN Firewall Rules.
BTW: When creating some OpenVPN RAS via the Wizard everything you need in pfSense is automatically created for you.-Rico
-
On ISP router, I rremove the TCP line and only running the UDP mode.
Pfsense firewall rules:
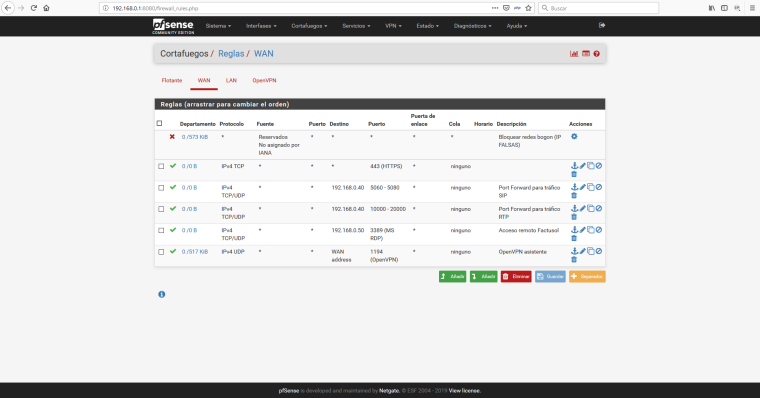
I remove the NAT por forward in pfsense firewall. Now I only have WAN rules in pfsense and UDP mode in NAT ISP router.
The OpenVPN client, look likje this. I have out bytes but no in:
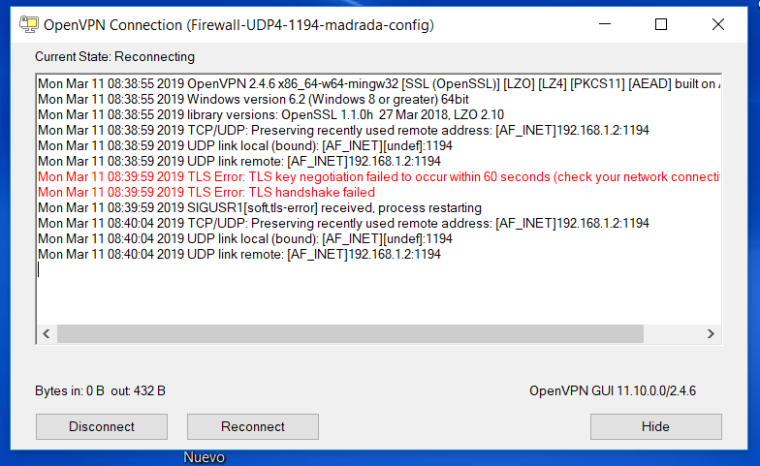
-
You need to put your public IP in the OpenVPN client config file when testing from the Internet.
Because your pfSense WAN is RFC1918 private network the export wizard put 192.168.1.2 in your client config which of course is not routed in the Internet.
So open your .ovpn file with Notepad++ for example and replace
remote 192.168.1.2 1194 udp
with
remote 1.2.3.4 1194 udp
1.2.3.4 = your public IP-Rico
-
It works!! I think the error was the public IP,
thank you !!!!