Routing issues after Upgrade (2.4.4) - No (ICMP) Reply to packets
-
Hello,
its seems i messed up somehow after upgrading to 2.4.4_2.
Im trying to reach: 10.55.101.21 (LAN Network) from openvpn Network (10.0.8.3)
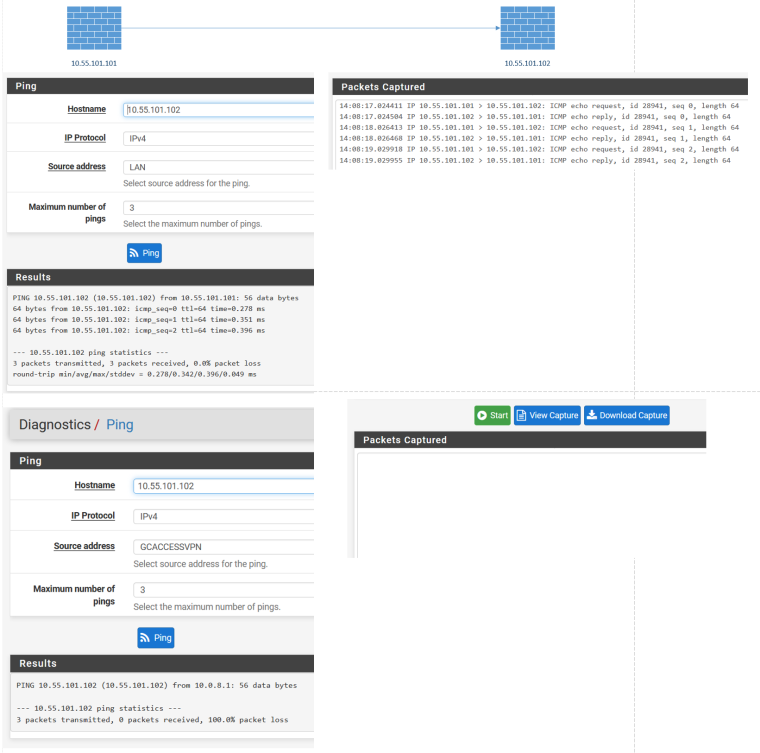
Using Diagnostics Ping it works fine from LAN Interface.
LAN -> LAN 10.55.101.21 -> okUsing Diagnostics Ping from OPENVPN Interface
GCAccessVPN -> LAN 10.55.101.21 -> noRules are set to any/any on both interfaces. Everything is open.
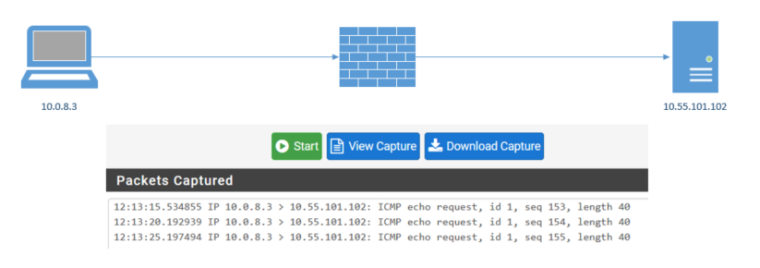
If I do Packet Capturing: I see the ECHO but no REPLY.
Any suggestions?
-
Additional Information, which makes curious.
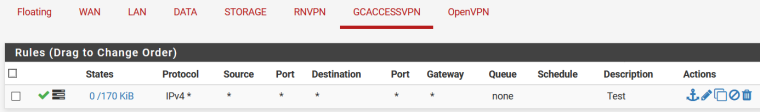
LAN Interface rules:
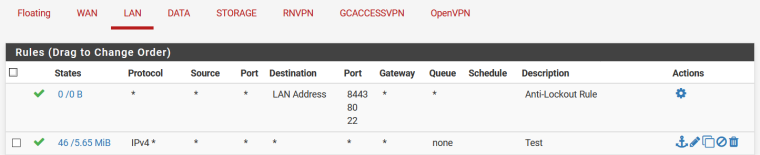
but are blocked?
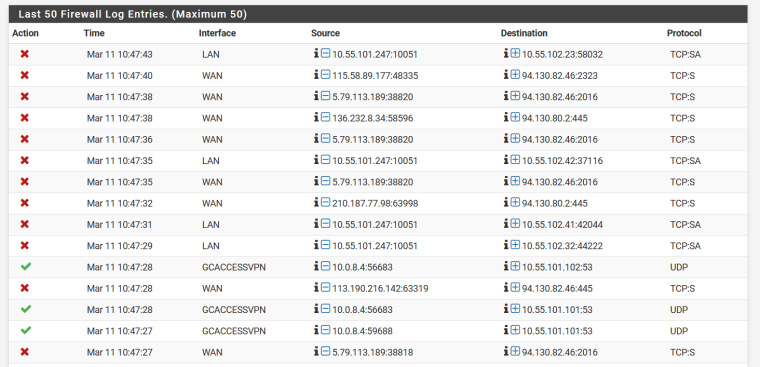
In addition to that:
Only DNS request are send thru the connection:
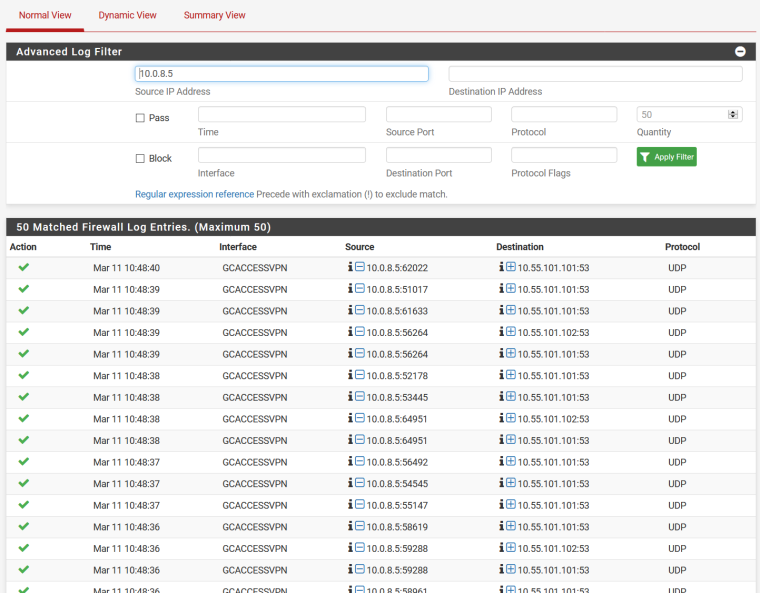
Anyone an Idea, what I have to check?
-
You seem to have asymmetrical routing..
The devices on your "lan" actually use pfsense as their default gateway?
You see those SA - tells me psense seeing the Syn,Ack (answer to syn in opening connection) but never saw the syn to open the state.
Could you draw up this network.
-
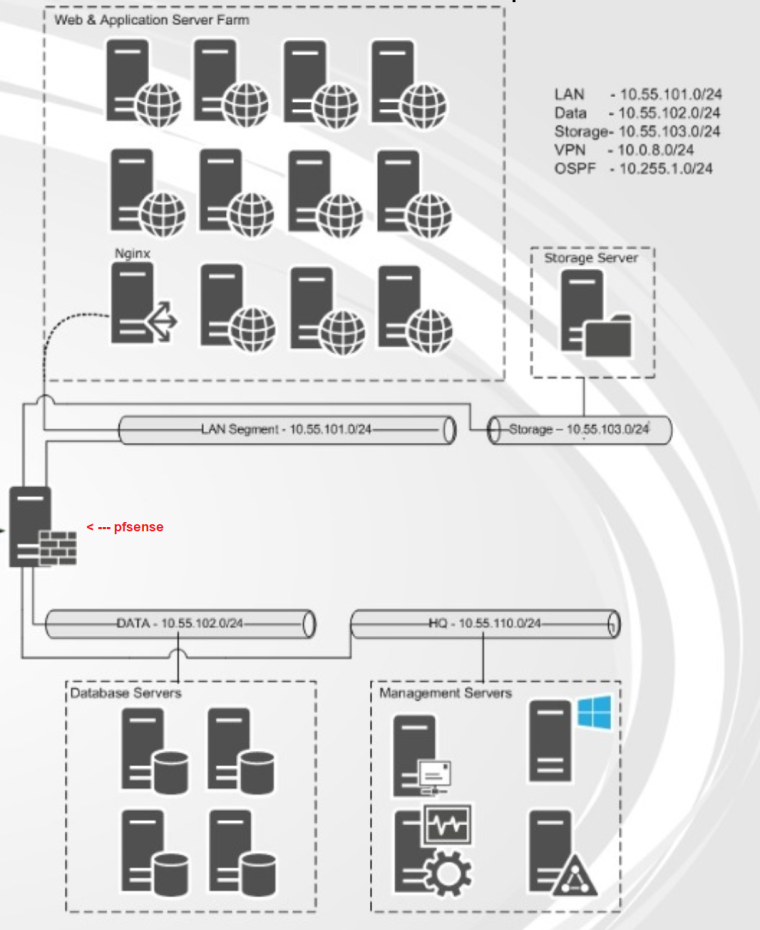
Like this? - It is virtualized on VMware ESXi 6.5
-
Ok that looks pretty sane.
So all the devices have default gateway as the IP address of pfsense in these /24s
This is sign of out of state traffic

10.55.101.247 sent syn,ack to 10.55.102.41 and to .32 but got blocked because no state would be the reason SA normally blocked.
Normally means that 101.247 got the syn without it going through pfsense so it could set up the state.. Running multiple L3 networks on the same L2 could do that. Since your saying this is VM, need to see the configuration of your vswitching.. Are you doing port groups. Is pfsense VM as well? Are you letting pfsense handle the tags for the vlans? Etc. etc..
You say you sniffed and saw the echo request.. Where did you sniff.. If you sniffed on pfsense interface into the network, then pfsense did its job and sent the request, if you don't see a reply - the box either sent it to some other gateway, didn't answer, never got it, etc.
-
Got you... but I wasn't finish yet :-)
the FW works with CARP IP (HA). The CARP IP is set a default GW for the clients. Maybe thats the reason for this asymmetrical rounting?
Well..
PING from VPN Client captured on FW
Ping direct FW -> Server
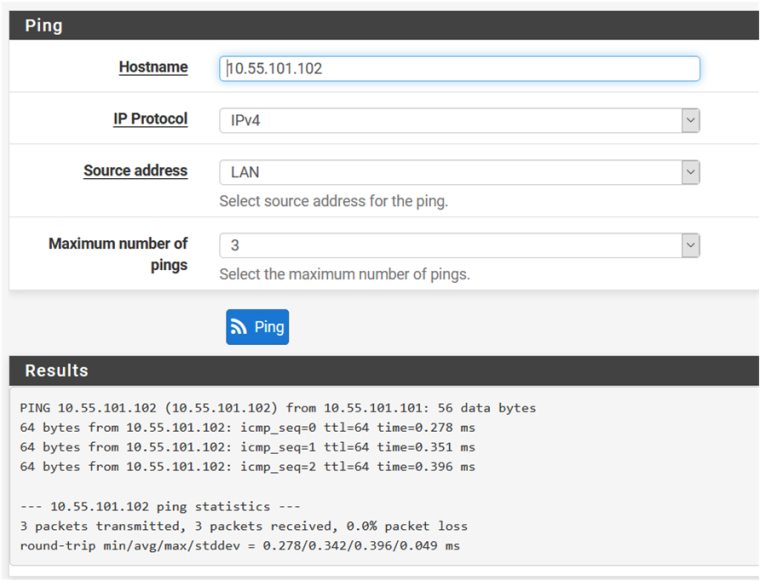
Ping VPN Interface -> Server
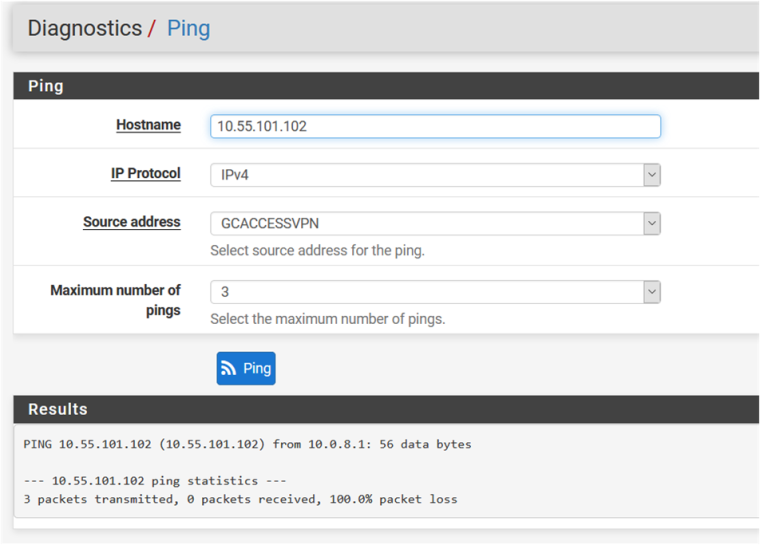
-
Yeah carp could have to do with it for sure..
You sure your HA is working correctly.. If you send the syn,ack back or echo reply back to wrong pfsense then yeah you have the same sort of issue.
-
Holy shit... it seems to be something bigger...
FW1
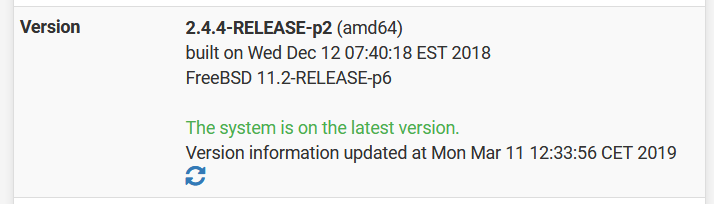
FW2
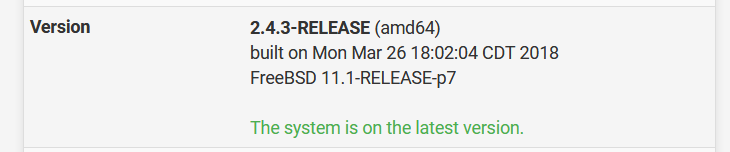
I only saw "The system is on the latest version"....
Well now i have to check, why the update didn't work and it doesn't see the missing updates.... -
Ok. HA is back and online... but the initial issue still exists :-(
Nothing arrives at .102